Idempotency, a crucial concept in API design, ensures consistent and reliable operations, regardless of repeated requests. This characteristic is vital for handling potential network issues and maintaining data integrity, especially in applications where multiple attempts at an action are possible.
Imagine a user attempting to update their profile information. If the API wasn’t idempotent, a repeated request might accidentally update the profile multiple times, leading to unexpected results. Idempotency prevents these issues by guaranteeing that the operation only happens once, regardless of the number of requests.
Defining Idempotency
Idempotency is a crucial concept in software design, particularly in APIs. It ensures that repeated requests have the same effect as a single request, regardless of how many times they are sent. This predictability is vital for robustness and reliability in distributed systems.Idempotency simplifies the handling of retries, network issues, and other potential errors that can cause multiple requests to be processed.
This predictability makes systems more resilient and less prone to unexpected behavior.
Definition of Idempotency
An operation is idempotent if performing it multiple times produces the same result as performing it once. In simpler terms, an idempotent action is one that can be safely repeated without causing unintended consequences. This means that running the operation a second, third, or any number of times will not change the state of the system any more than the first time.
Core Concept in Simple Terms
Imagine you’re ordering a coffee. A non-idempotent operation would be like clicking the “order” button multiple times. Each click might create a new order, leading to multiple coffees being charged to your account. An idempotent operation, on the other hand, would be like clicking the “order” button repeatedly. Only the first click actually places the order; subsequent clicks have no effect.
Characteristics of Idempotent Operations
Idempotent operations share key characteristics that distinguish them from non-idempotent ones. They inherently avoid unintended consequences from repeated requests.
- Consistency: An idempotent operation maintains a consistent state regardless of how many times it’s invoked. A crucial characteristic.
- No Side Effects: The operation doesn’t have any unintended effects beyond the intended outcome. This is essential for predictable behavior.
- Data Integrity: The operation doesn’t corrupt or alter data in unforeseen ways when repeated. This is vital for maintaining the accuracy of data.
Idempotent vs. Non-Idempotent Operations
The following table contrasts idempotent and non-idempotent operations:
| Feature | Idempotent | Non-Idempotent |
|---|---|---|
| Effect of Repeated Execution | Produces the same result as a single execution. | Produces a different result with each execution. |
| Example | Retrieving a user profile, updating a record with a unique identifier. | Placing an order, creating a new user account. |
| Retryability | Safe to retry without causing issues. | Retry may lead to errors or unintended consequences. |
| Data Consistency | Preserves data consistency. | Can lead to data inconsistencies. |
Importance of Idempotency for Reliability
API reliability is paramount in today’s interconnected digital world. Users expect consistent and predictable responses from APIs, and failures can lead to significant operational disruptions and reputational damage. Ensuring reliability requires careful consideration of various factors, and idempotency plays a critical role in this regard.Idempotency significantly enhances API reliability by mitigating the impact of repeated requests. This is particularly crucial in scenarios where network issues, retries, or even malicious actors might trigger multiple requests for the same operation.
By guaranteeing that repeated identical requests have the same effect as a single request, idempotent APIs provide a robust foundation for handling these situations without undesired side effects.
Crucial Role of Reliability in APIs
API reliability is essential for several reasons. First, it ensures consistent user experience. If an API frequently fails or returns inconsistent results, user trust and confidence are eroded. Second, it contributes to the overall stability of applications relying on the API. Unreliable APIs can cause cascading failures throughout a system.
Third, it impacts business operations. Disruptions caused by unreliable APIs can lead to lost revenue, operational inefficiencies, and potential legal issues. Fourth, it builds customer confidence and loyalty. Reliable APIs support user expectations and foster trust in the platform’s overall functionality.
How Idempotency Contributes to API Reliability
Idempotency is a powerful tool for building reliable APIs. When an API operation is idempotent, it can be safely retried multiple times without changing the overall outcome. This characteristic is particularly valuable in handling network issues or transient failures. If a request fails due to a temporary network outage, the client can automatically retry the request without fear of unintended consequences.
This resilience is a key component of a reliable API.
Impact of Non-Idempotent Operations on API Reliability
Non-idempotent operations, on the other hand, pose significant risks to API reliability. If a request is not idempotent, multiple identical requests can lead to unexpected or undesirable results. This can include data corruption, double billing, or other inconsistencies. For instance, a non-idempotent payment API might result in the same payment being processed multiple times, leading to financial errors.
This inherent vulnerability makes non-idempotent operations more susceptible to errors and failures, thereby jeopardizing the reliability of the API.
Table Demonstrating Idempotency’s Impact on API Reliability
| Scenario | Impact of Idempotency | Impact of Non-Idempotency |
|---|---|---|
| Network interruption during a request | The client can retry the request without affecting the outcome. | Repeated requests might lead to duplicate data entries, double charges, or other inconsistencies. |
| Client-side errors or retries | Multiple requests for the same operation have no cumulative effect. | Repeated requests can lead to incorrect data or unintended changes in the system state. |
| Malicious attempts to exploit vulnerabilities | Repeated requests for the same operation do not cause significant harm. | Repeated requests might be exploited to overload the system or corrupt data. |
| Automated testing and deployment | Automated testing and deployment workflows can be implemented with greater confidence. | Automated processes might lead to unpredictable or erroneous outcomes, requiring extensive validation and error handling. |
Idempotency and Data Consistency
Idempotency is a crucial characteristic for APIs, particularly when dealing with potentially inconsistent or unreliable network conditions. Ensuring data consistency in an API is paramount for maintaining the integrity of the underlying data and the reliability of the application. Idempotency plays a significant role in achieving this goal.Idempotent operations, by their very nature, guarantee that repeated requests yield the same outcome as a single request, regardless of the number of times the request is made.
This property is instrumental in maintaining data consistency. Repeated requests with idempotent operations do not lead to unintended or unpredictable changes to the data. This inherent characteristic is vital for robust API design, particularly in scenarios where network issues or transient failures might cause multiple requests to be processed.
Impact on Data Integrity
Repeated requests with idempotent operations maintain data integrity by preventing data duplication or conflicting updates. If an operation is idempotent, multiple identical requests will not introduce errors or inconsistencies in the data. The operation will always produce the same result, irrespective of the number of times it is called. This predictability and stability are essential for maintaining data consistency and preventing unexpected outcomes.
Consequences of Data Inconsistency in APIs
Data inconsistency in APIs can lead to various detrimental consequences. Duplicate entries, incorrect data updates, or missing updates can compromise the accuracy and reliability of the system. This can lead to financial losses, reputational damage, and operational disruptions. For example, in an e-commerce system, a repeated payment request without idempotency could result in the customer being charged multiple times.
Similarly, in a banking system, incorrect transaction updates can lead to serious financial problems.
Idempotent vs. Non-Idempotent Operations
Understanding the difference between idempotent and non-idempotent operations is crucial for maintaining data consistency. A table below illustrates this difference in the context of data operations.
| Operation | Data Consistency |
|---|---|
| Create a new user | Idempotent – Only creates the user once, regardless of repeated requests. |
| Update a user’s address | Idempotent – Only updates the address once, even if requested multiple times. |
| Place an order | Non-idempotent – Each request places a new order, potentially leading to multiple orders for the same item. |
| Withdraw funds | Non-idempotent – Each request withdraws funds, leading to multiple withdrawals if repeated. |
The table clearly demonstrates how idempotent operations, unlike non-idempotent ones, preserve data integrity and prevent data duplication or conflicting updates. This is vital for maintaining the consistency and reliability of data within an API.
Implementing Idempotency in APIs
Implementing idempotent operations within API design is crucial for ensuring data integrity and reliability. This involves strategically planning how to handle repeated requests, preventing unintended data modifications, and guaranteeing consistent outcomes. This section will detail practical methods for achieving idempotency, emphasizing best practices and diverse implementation strategies.Achieving idempotency requires careful consideration of the API’s structure and the potential for repeated requests.
It is not merely a technical solution but an architectural principle that should be ingrained in the API design process. The following sections Artikel key strategies and best practices for implementing this principle.
Strategies for Achieving Idempotency
Implementing idempotency within an API involves several key strategies, each with distinct implications. These methods provide different levels of control and flexibility, allowing developers to tailor the implementation to their specific needs.
- Using Unique Request IDs: A critical strategy for ensuring idempotency is the use of unique request identifiers. Each API request should be assigned a unique identifier, which the server can then use to track and manage the request. If a duplicate request arrives with the same ID, the server can identify it as a repeat and avoid processing it again, returning the previous successful response or a confirmation of the existing status.
This approach is highly effective for ensuring that repeated requests do not lead to unwanted data modifications. For example, if a user attempts to place an order multiple times with the same ID, the server can recognize the duplicate request and return the status of the previously processed order.
- Idempotent Resource Design: The design of the API resources themselves plays a significant role in achieving idempotency. Operations should be explicitly designed to handle repeated requests without causing unintended side effects. For instance, an update operation should only modify the resource if the data differs from the current state. This ensures that subsequent requests with identical data will not cause additional updates.
For example, updating a user’s profile should only modify the fields that have changed since the last update, avoiding redundant updates.
- Idempotent HTTP Methods: Using HTTP methods that are inherently idempotent (like GET, HEAD, and PUT) helps achieve idempotency in the API’s design. The server can process these requests multiple times without causing different results. However, other methods, such as POST, may not be inherently idempotent. Using POST requests may require additional measures like unique request IDs to guarantee idempotency in API implementations.
This approach leverages the inherent properties of HTTP methods to simplify the implementation of idempotency.
- Optimistic Locking: Optimistic locking is a strategy where the client includes a version number or timestamp with each request. The server verifies that the resource has not been modified since the client retrieved the resource. If it has, the client receives an error, and the client retries the operation with the updated version. This approach is useful for preventing conflicts in concurrent updates.
For example, in a collaborative document editing application, optimistic locking ensures that only the latest version of the document is updated.
Best Practices for Ensuring Idempotency
Adhering to best practices is essential for building reliable and efficient APIs. These best practices guide the implementation and maintenance of idempotent operations, ensuring data integrity.
- Client-Side Idempotency Handling: Clients should be designed to handle potential retries and idempotent requests. If a client receives an error, it should retry the request, ideally with the same request ID. Proper retry mechanisms can be implemented to manage transient failures, ensuring that the API can recover from temporary issues and maintain data integrity.
- Server-Side Idempotency Handling: The server-side implementation should be robust to handle duplicate requests. The server should carefully check for unique identifiers and ensure that repeated requests do not lead to data corruption. This ensures that the API can handle high volumes of traffic and maintain data consistency under various conditions.
- Documentation and Testing: Thorough documentation of the idempotency requirements for each API endpoint is crucial. Thorough testing should cover various scenarios, including repeated requests, to validate the API’s idempotency. This approach allows developers and users to understand the expected behavior and prevents unexpected issues.
Implications of Choosing Specific Idempotency Strategies
The selection of idempotency strategies significantly impacts the API’s performance, scalability, and complexity. The implications must be carefully considered during the design phase.
- Performance Considerations: Strategies like unique request IDs might introduce slight overhead due to additional processing required to manage these identifiers. Careful consideration must be given to the trade-offs between performance and reliability when choosing a strategy. However, these strategies enhance overall reliability and reduce the risk of data inconsistency.
- Scalability Implications: The chosen strategy must be scalable enough to handle the anticipated volume of requests. Strategies must not introduce significant bottlenecks or slowdowns as the API grows. Strategies should allow for efficient management of duplicate requests without compromising scalability.
- Complexity Trade-offs: More complex strategies, such as optimistic locking, might add to the API’s complexity, requiring careful planning and development. The added complexity must be balanced against the need for enhanced data consistency. However, these strategies enhance the reliability and consistency of the API.
Examples of Idempotent API Methods
Idempotency is a crucial aspect of API design, ensuring reliable and predictable behavior. Understanding which API methods are idempotent and which are not is essential for building robust and resilient systems. This section provides concrete examples to illustrate the concept.The ability of an API method to produce the same result regardless of the number of times it’s invoked, even with the same input, is a defining characteristic of idempotency.
This crucial property allows for error handling and retry mechanisms, strengthening the overall API’s reliability.
Idempotent API Methods
The core principle of idempotency lies in consistent outcomes. Methods that return the same data or perform the same operation regardless of repeated calls are considered idempotent.
- GET requests are typically idempotent. A GET request retrieves data from a resource. Repeating a GET request with the same parameters will always return the same data; it does not modify the resource.
- PUT requests, when used correctly, are also idempotent. A PUT request updates a resource. Multiple identical PUT requests to the same resource will only update the resource once, as the system is designed to avoid redundant updates.
Non-Idempotent API Methods
Methods that produce different results on repeated calls with the same input are considered non-idempotent.
- POST requests are typically non-idempotent. A POST request creates or updates a resource based on the provided data. Repeated identical POST requests may lead to multiple resource creations or updates, which can have unintended consequences. For instance, consider ordering a product multiple times via a POST request to an e-commerce site; each request would generate a new order.
- PATCH requests are also generally non-idempotent. A PATCH request modifies a resource by applying a partial update. Repeating a PATCH request with the same update multiple times can have an unpredictable effect on the resource. Multiple identical PATCH requests could lead to unintended changes in the resource.
Idempotency in Specific API Scenarios
Idempotency plays a critical role in various API scenarios, enhancing reliability and data integrity. For instance, in payment processing APIs, idempotency is paramount to prevent accidental double payments. The ability to retry a payment request without unintended consequences is essential for maintaining financial stability.
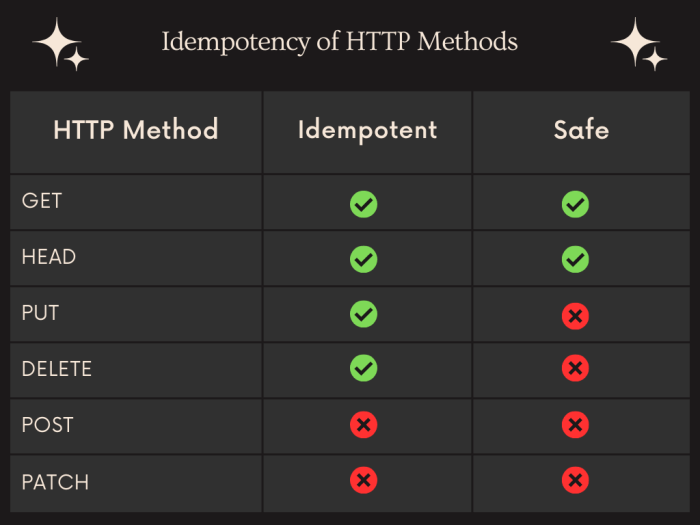
| HTTP Method | Idempotent | Description |
|---|---|---|
| GET | Yes | Retrieves data; does not modify resources. |
| PUT | Yes | Updates a resource; ensures single update despite repeated calls with the same data. |
| POST | No | Creates or updates a resource based on the provided data. Multiple identical requests may result in multiple resource creations or updates. |
| PATCH | No | Modifies a resource by applying a partial update. Repeated identical requests can lead to unpredictable results. |
Use Cases for Idempotent APIs
Idempotent APIs are crucial in modern software architecture, particularly in systems handling high volumes of requests and transactions. Their ability to handle repeated requests without altering the system’s state reliably is vital for maintaining data integrity and ensuring application stability. This section will delve into specific use cases, demonstrating how idempotency is essential in various contexts.Idempotency’s significance extends beyond simple redundancy to encompass scenarios where multiple requests might be sent due to network issues, user errors, or application bugs.
By ensuring that multiple identical requests yield the same result, idempotent APIs safeguard against unintended data modifications and system failures.
Transactional APIs
Transactional APIs, often handling financial or inventory updates, benefit significantly from idempotency. The inherent nature of transactions frequently involves multiple steps, and failures at any point can lead to inconsistencies. Idempotency ensures that if a request is repeated due to a network outage or system hiccup, the outcome remains unchanged. This crucial feature prevents double charges, lost transactions, or other financial irregularities.
Financial Transactions
Financial transactions are a prime example of where idempotency is paramount. Imagine a user initiating a payment. If the network experiences a momentary interruption, the payment request might be sent multiple times. An idempotent API ensures that even if the request is repeated, the transaction is processed only once, preventing unauthorized charges or the creation of duplicate entries in the financial records.
Real-World Scenarios
Several real-world scenarios demonstrate the importance of idempotent APIs. Consider an online booking system. If a user accidentally submits multiple booking requests, an idempotent API will ensure that only one booking is created, avoiding conflicts and ensuring accuracy. Similarly, in an e-commerce platform, an idempotent API prevents the accidental creation of duplicate orders when a customer re-submits an order due to a network issue.
Examples of APIs Requiring Idempotency
- Online Payment Processing: An API for processing online payments must be idempotent to prevent double charges if a network issue causes a request to be sent multiple times.
- Inventory Management: An API for updating inventory levels must be idempotent to avoid over- or under-counting inventory if multiple updates occur due to system failures.
- Banking Transactions: An API for handling fund transfers, payments, and other financial transactions must be idempotent to prevent double charges or other financial discrepancies.
- Cloud Storage: An API for uploading files to cloud storage needs idempotency. If a user’s upload is interrupted, the API can safely re-process the request without creating duplicate files or overwriting existing ones.
These examples highlight the critical role of idempotency in ensuring the reliability and accuracy of various applications, particularly those handling financial transactions and sensitive data.
Avoiding Common Pitfalls in API Idempotency

Ensuring idempotency in API design is crucial for reliable and robust systems. However, common pitfalls can arise if not carefully considered during the design and implementation phases. Understanding these potential issues and implementing preventative measures is vital for building robust and dependable APIs.Neglecting idempotent design can lead to data inconsistencies, wasted resources, and a negative user experience. By proactively addressing potential issues, developers can create more resilient and trustworthy APIs.
Common Errors in Designing Idempotent APIs
Incorrectly identifying idempotent operations can lead to unintended consequences. For example, an API endpoint intended for creating a new resource might not be idempotent if it accidentally modifies existing resources. In addition, complex interactions, such as those involving external services or asynchronous processes, can introduce subtle errors that make ensuring idempotency challenging. A failure to account for these interactions can lead to inconsistencies in the system’s state.
Consequences of Neglecting Idempotency in API Design
Failing to design idempotent APIs can have several detrimental consequences. Data inconsistencies, where multiple identical requests result in different outcomes, are a significant concern. This can lead to data corruption or inaccuracies, potentially impacting downstream processes and applications. Furthermore, inefficient resource utilization is another potential outcome, as redundant operations might be executed unnecessarily, consuming more processing power and bandwidth.
Finally, a negative user experience arises from unpredictable and inconsistent results.
Potential Issues Related to Network Failures and Retries with Non-Idempotent Operations
Network interruptions or transient failures are common in distributed systems. When a non-idempotent operation is executed multiple times due to a network failure, the result may vary, leading to data inconsistencies or unexpected behavior. Retries, necessary for fault tolerance, become problematic with non-idempotent APIs, as repeated attempts can cause the system to enter an undesirable state. For example, a non-idempotent order placement API might result in multiple orders being placed if the initial request fails and is retried multiple times.
The lack of idempotency can thus cause the application to experience significant data discrepancies.
Methods to Avoid Common Pitfalls in Ensuring Idempotency
Several methods can help avoid the pitfalls associated with non-idempotent APIs. One crucial step is a thorough understanding of the operations performed by the API. Analyzing each API endpoint’s logic and potential interactions with other systems is essential. Explicitly managing request uniqueness is another key approach. This involves utilizing unique identifiers or request tokens to track requests and prevent redundant executions.
Employing idempotent request handling within the API implementation is equally important. For example, the system can check if a request has already been processed and avoid performing the operation if it has. Utilizing an appropriate request queuing system to manage and control request processing can further enhance idempotency. The system can then ensure that only one request is processed at a time, thereby avoiding any unintended consequences.
Finally, rigorous testing is vital. Comprehensive testing, including simulating network failures and retries, is essential to ensure idempotent behavior under various conditions. This can help in detecting and addressing potential issues before they impact users.
Tools and Technologies for Idempotent APIs
Implementing idempotency in APIs requires careful consideration of various tools and technologies. This section explores key components and techniques for ensuring that API requests can be safely repeated without adverse effects. Appropriate selection and implementation of these tools will enhance the reliability and robustness of the API.
Programming Language Implementations
Various programming languages offer libraries and frameworks that streamline the process of creating idempotent API endpoints. These tools often provide mechanisms for managing request idempotency at the application level.
- Python: Libraries like Flask and Django offer robust support for handling HTTP requests and incorporating idempotency logic. For instance, Flask’s request object allows easy access to request headers, which can be crucial for identifying and managing idempotent requests.
- Java: Spring Boot, a popular framework, facilitates the implementation of idempotent API endpoints through annotations and configuration. This framework helps manage request data and ensures idempotency without significant manual coding.
- Node.js: Express.js, a widely used Node.js framework, enables the creation of idempotent APIs. The framework allows developers to easily implement request handling logic that verifies and manages repeated requests.
API Gateways and Idempotency
API gateways play a crucial role in managing idempotent requests. These gateways act as a central point for all incoming requests, providing an opportunity to implement idempotency logic.
- Request Deduplication: API gateways often include built-in features for deduplicating requests. This involves tracking requests by unique identifiers (e.g., request IDs, client-generated IDs), ensuring that only the first instance of a request is processed.
- Request Queuing: If a request encounters temporary issues during processing, API gateways can queue the request until the issue is resolved. This allows for the handling of potentially idempotent requests without immediate processing.
- Circuit Breakers: Gateways can implement circuit breakers to prevent cascading failures if a downstream service is experiencing problems. This approach can protect against errors while maintaining idempotency.
Database Support for Idempotency
Databases can be leveraged to enforce idempotency. They offer features that assist in preventing redundant data entries or updates.
- Optimistic Locking: This technique uses version numbers or timestamps to detect conflicts when multiple requests attempt to update the same data. The database ensures only the most recent update is applied.
- Unique Constraints: Databases enforce unique constraints on specific fields. This approach prevents duplicate entries, thus contributing to idempotency.
- Transactions: Using database transactions ensures that multiple operations are treated as a single unit of work. If any part of the transaction fails, the entire transaction is rolled back, maintaining data integrity and idempotency.
Comparing Different Idempotency Strategies
Comparing different idempotency strategies involves evaluating their strengths, weaknesses, and suitability for various API use cases. Understanding these nuances allows developers to choose the most appropriate approach for ensuring data integrity and reliability within their systems. A thoughtful selection of an idempotency strategy can significantly improve the robustness and efficiency of an API.Different strategies for implementing idempotency in APIs offer varying levels of complexity, trade-offs, and performance characteristics.
The choice of strategy often hinges on factors such as the scale of the API, the frequency of requests, and the specific requirements of the application.
Idempotency Strategies
Various strategies exist for ensuring idempotency in APIs. These strategies employ different mechanisms to handle duplicate or repeated requests.
- Request-Based Idempotency: This approach focuses on uniquely identifying each request. A unique request identifier (UUID or similar) is included in each request, and the API server maintains a record of processed requests. If a duplicate request arrives, the server can consult its records to determine if the request has already been processed, avoiding redundant actions. This strategy works well for APIs that process infrequent or low-volume requests and where the cost of storing request history is relatively low.
- Data-Based Idempotency: This approach leverages the data within the request itself. The API server checks for the existence of data associated with the request. If the data already exists, the request is considered idempotent and no further action is taken. This is suitable for scenarios where the request’s effect can be determined by examining the request data, like updating a record with specific values.
- State-Based Idempotency: This strategy focuses on the application’s internal state. The API server checks for existing data or conditions related to the request within the system’s state. For instance, a booking API could check if a seat is already booked before processing a new booking request. This strategy is well-suited for scenarios with limited data and where the application’s state can be readily queried.
Evaluating Strengths and Weaknesses
Choosing the right strategy depends on the specific requirements of the API. Request-based idempotency is generally more flexible, but can have higher storage costs if the API handles a large volume of requests. Data-based idempotency is simpler to implement but may not always be applicable depending on the nature of the request. State-based idempotency offers a streamlined approach when the application’s state can be easily consulted, but its reliance on the application’s internal state can be a limitation in some contexts.
Table of Idempotency Strategies
The following table summarizes different idempotency strategies, highlighting their strengths, weaknesses, and suitable use cases:
| Strategy | Strengths | Weaknesses | Use Cases |
|---|---|---|---|
| Request-Based | Flexible, widely applicable, suitable for high-volume requests with unique identifiers | Higher storage cost for request history, potential for complexity in handling large volumes of requests | Payment processing, order creation, complex data updates |
| Data-Based | Simple implementation, efficient for requests with specific data constraints | Not suitable for requests without identifiable data, may not be applicable for all scenarios | Updating records with specific attributes, checking for resource existence |
| State-Based | Streamlined for applications with easily accessible internal state | Limited to applications with readily available state information, may not be scalable for large-scale systems | Booking systems, resource allocation, inventory management |
Security Implications of Idempotency
Idempotency, while crucial for API reliability, also presents significant security considerations. Understanding how idempotent APIs can bolster security and how non-idempotent APIs can introduce vulnerabilities is vital for building robust and trustworthy systems. This section explores the relationship between idempotency and API security, emphasizing practical implications and mitigation strategies.Idempotent APIs, by their nature, reduce the risk of accidental or malicious duplicate requests.
This inherent characteristic can protect against various security threats, from simple typos to sophisticated attacks. Furthermore, the predictable nature of idempotent requests allows for easier auditing and monitoring, which are essential components of a strong security posture.
Impact of Idempotency on Security Threats
Idempotency directly mitigates the risk of many common attack vectors. Multiple identical requests, whether intentional or accidental, have no additional effect beyond the initial successful execution. This feature significantly reduces the potential for denial-of-service (DoS) attacks stemming from repeated requests, a common attack vector in many API environments.
Implementing Idempotency Measures while Maintaining Security
Implementing idempotency in APIs requires careful consideration of security. Robust request tracking and validation mechanisms are essential to prevent malicious actors from exploiting idempotency to their advantage. For instance, including unique request identifiers (UUIDs) allows for efficient tracking and ensures that only legitimate, non-duplicate requests are processed.
Security Risks of Non-Idempotent APIs
Non-idempotent APIs introduce security vulnerabilities. The potential for unintended consequences from repeated requests, such as accidental over-processing or resource exhaustion, creates a significant security risk. Without proper controls, an attacker could potentially overload a system by sending a high volume of identical requests. This could lead to denial-of-service attacks, data corruption, or unauthorized resource consumption. For example, imagine a non-idempotent API for transferring funds.
A malicious actor could flood the system with duplicate transfer requests, leading to significant financial losses.
Security Best Practices for Idempotent APIs
Implementing strong security measures alongside idempotency is paramount. This includes robust authentication and authorization mechanisms to ensure only legitimate users can make requests. Employing rate limiting, input validation, and proper error handling are also vital for preventing malicious exploitation of idempotent APIs.
Example of Security Vulnerability in Non-Idempotent APIs
A non-idempotent API for adding users might not properly handle duplicate requests. If an attacker sends multiple identical user creation requests, the system might create multiple identical users, leading to data inconsistencies and security breaches. Conversely, if the same user sends duplicate requests, it could cause unexpected or undesirable side effects.
Last Word
In conclusion, idempotency is not just a technical detail; it’s a fundamental requirement for building robust and reliable APIs. By understanding and implementing idempotent practices, developers can enhance the user experience, protect data integrity, and ensure the smooth functioning of their applications, particularly in scenarios involving potential retries or multiple requests.
FAQ Insights
What is the difference between idempotent and non-idempotent operations?
Idempotent operations produce the same result whether executed once or multiple times. Non-idempotent operations yield different outcomes with repeated execution. This difference is crucial for API reliability and data consistency.
How does idempotency help with handling retries?
If a request fails due to network issues, idempotency ensures that subsequent retries won’t lead to unintended data modifications. This is because the operation will always achieve the same result, no matter how many times it is attempted.
What are some common pitfalls to avoid when designing idempotent APIs?
Failing to consider the possibility of retries, neglecting to use unique request identifiers, and not properly handling potential conflicts during updates are some pitfalls. Implementing proper error handling and retry mechanisms is essential to prevent these issues.
How can I ensure data consistency in my API using idempotency?
By designing operations to be idempotent, you ensure that multiple requests for the same operation will always lead to the same result, maintaining data integrity. Using techniques like unique request IDs and checking for existing data states is essential for successful implementation.