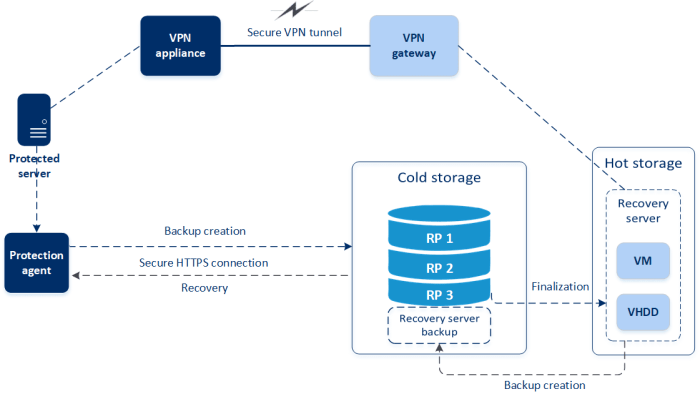
What is a blue-green deployment for migration cutover, a strategy central to modern software engineering, offers a sophisticated approach to minimize downtime and risk during application updates and infrastructure migrations. This technique, which involves maintaining two identical environments – “blue” and “green” – enables seamless transitions, allowing for testing and validation in a live environment before directing user traffic to the new, updated version.
The core principle revolves around the ability to switch between these environments rapidly, ensuring continuous service availability and enhancing the overall user experience.
This methodology distinguishes itself from traditional deployment approaches, such as in-place updates, by providing a robust rollback mechanism and reducing the probability of service interruptions. By meticulously crafting identical environments, employing automation, and integrating rigorous testing procedures, blue-green deployments empower development teams to confidently deploy changes, manage database migrations, and optimize application performance with enhanced efficiency and control. This Artikel will dissect the intricacies of blue-green deployments, offering insights into its advantages, implementation strategies, and real-world applications.
Defining Blue-Green Deployment
Blue-green deployment is a sophisticated release strategy designed to minimize downtime and risk when deploying new software versions. It involves maintaining two identical production environments: the “blue” environment, which is currently live and serving user traffic, and the “green” environment, which is a near-identical replica ready to receive the new version of the application. This approach allows for a seamless transition between versions, enhancing system availability and reducing the impact of potential issues.
Core Concept of Blue-Green Deployment
The core concept of blue-green deployment hinges on the ability to switch traffic seamlessly between two identical environments. This strategy focuses on minimizing disruption during deployments and facilitating rapid rollback in case of problems. The “blue” environment represents the currently active version, while the “green” environment serves as a staging area for the new version. Once the new version in the green environment is tested and validated, traffic is rerouted from the blue environment to the green environment.
Analogy for Understanding Blue-Green Deployments
A useful analogy to understand blue-green deployments is the concept of an airport runway. Imagine two parallel runways. One runway (blue) is actively used by airplanes (users accessing the application). The other runway (green) is undergoing maintenance or is prepared for the next batch of airplanes. When the first runway needs maintenance or is not fit for use, the traffic switches to the second runway.
The same principle applies to the application environments:* Blue Environment: The current, live environment serving user traffic.
Green Environment
The new version of the application, ready to receive traffic.
Switching Traffic
The act of rerouting user requests from the blue environment to the green environment.
Primary Objective of Utilizing Blue-Green Deployments
The primary objective of utilizing blue-green deployments is to achieve zero-downtime deployments and minimize the risk associated with software releases. This is achieved by several key mechanisms:* Reduced Downtime: By pre-staging the new version in a separate environment, the switchover can be executed quickly, minimizing the period of unavailability.
Risk Mitigation
The green environment can be thoroughly tested before the traffic switch, reducing the likelihood of deploying a faulty version. If issues arise, the traffic can be instantly switched back to the blue environment, effectively rolling back the deployment.
Simplified Rollbacks
In the event of a problem, rolling back to the previous version is as simple as switching traffic back to the blue environment. This dramatically reduces the time and complexity of recovery.
Improved User Experience
By maintaining continuous availability, blue-green deployments enhance the user experience, preventing interruptions and ensuring consistent access to the application.
Enhanced Testing Capabilities
The green environment provides a safe space for comprehensive testing, including performance and integration tests, before the new version is exposed to live traffic.
Advantages of Blue-Green Deployment
Blue-green deployments offer significant advantages over traditional deployment strategies, primarily due to their ability to minimize or eliminate downtime, enhance risk mitigation, and provide a more controlled and reversible deployment process. These benefits translate to improved user experience, reduced operational risks, and increased confidence in the deployment process.
Zero Downtime During Deployments
The core advantage of blue-green deployment lies in its ability to facilitate zero-downtime deployments. This is achieved by maintaining two identical environments, the “blue” (live, active) and the “green” (staging, inactive) environment.The process unfolds as follows:
- The “green” environment receives the new application version and is thoroughly tested.
- Once testing is complete and the “green” environment is validated, traffic is switched from the “blue” environment to the “green” environment. This switch is often implemented using a load balancer or DNS configuration change.
- The “blue” environment then becomes the inactive environment, ready for the next deployment.
This seamless transition ensures that users experience no interruption in service. The continuous availability of the application is maintained, providing a consistent user experience. Consider the following example: a major e-commerce platform uses blue-green deployments to release new features. By switching traffic instantaneously, they avoid the traditional maintenance windows that could disrupt user shopping experiences, ultimately leading to increased sales and customer satisfaction.
The underlying principle is that the switchover is a rapid operation. The speed depends on the mechanism used for traffic redirection. It could be a DNS change, which might take a few seconds to propagate, or a load balancer switch, which can be instantaneous.
Setting up the Blue and Green Environments
The creation of identical Blue and Green environments is a critical prerequisite for a successful blue-green deployment. This process involves replicating the entire production infrastructure, including hardware, software, and configurations, in two separate, isolated environments. This ensures that the Green environment can accurately mirror the Blue environment, allowing for safe testing and seamless cutover with minimal disruption.
Creating Identical Environments
The establishment of two parallel, functionally equivalent environments, often termed “Blue” and “Green,” requires a meticulous and systematic approach. This involves replicating all components of the existing production environment, including servers, databases, load balancers, and application code, within the new Green environment.
- Infrastructure Provisioning: The initial step involves provisioning the necessary infrastructure. This entails allocating the required compute resources (virtual machines, containers, etc.), storage, and networking components. This can be done manually, but is highly discouraged due to the potential for human error and the lack of repeatability. Instead, the preferred method is to leverage Infrastructure as Code (IaC) to automate and standardize this process.
- Configuration Replication: Once the infrastructure is provisioned, the configurations of all components must be replicated. This includes operating system settings, application configurations, database schemas, and network settings. The goal is to ensure that the Green environment functions identically to the Blue environment in every respect. Tools like Ansible, Chef, and Puppet are frequently used to automate configuration management and ensure consistency across both environments.
- Data Synchronization: If the application relies on a database, the data must be synchronized between the Blue and Green environments. This can be achieved through various methods, including database replication, point-in-time recovery, or data migration tools. The choice of method depends on the size of the database, the acceptable downtime, and the specific database technology. For instance, in a high-availability PostgreSQL setup, logical replication can be used to maintain a near real-time copy of the database in the Green environment, minimizing cutover downtime.
- Code Deployment: The application code itself must be deployed to the Green environment. This typically involves building and deploying the application artifacts (e.g., WAR files, JAR files, container images) to the Green environment’s servers or containers. The code deployed to the Green environment is typically the new version intended for the cutover. Proper version control and automated build pipelines are crucial to ensure the correct code is deployed consistently.
- Testing and Validation: Before activating the Green environment, thorough testing is essential. This includes functional testing, performance testing, and security testing to verify that the Green environment functions correctly and meets all performance and security requirements. This stage also includes user acceptance testing (UAT) to validate that the new version meets business requirements.
Infrastructure as Code (IaC) Importance
Infrastructure as Code (IaC) plays a pivotal role in the successful implementation of blue-green deployments. It enables the automation, standardization, and repeatability of infrastructure provisioning and configuration, minimizing manual errors and ensuring consistency between the Blue and Green environments.
- Automation: IaC allows for the automated provisioning and configuration of infrastructure components. This eliminates the need for manual configuration, which is time-consuming, error-prone, and difficult to scale. Tools like Terraform, AWS CloudFormation, and Azure Resource Manager allow you to define your infrastructure as code, and then automatically create and manage it.
- Consistency: IaC ensures that the Blue and Green environments are identical. By defining the infrastructure in code, you can guarantee that both environments have the same configurations, reducing the risk of environment-specific issues. This consistency is crucial for accurate testing and a smooth cutover.
- Repeatability: IaC allows you to easily recreate the Blue or Green environments at any time. This is particularly useful for disaster recovery, testing, and rolling back to a previous version if necessary. For example, if a critical issue is discovered in the Green environment after a cutover, the infrastructure can be quickly rolled back to the previous stable state (Blue) by redeploying the IaC configuration for the Blue environment.
- Version Control: IaC configurations are typically stored in version control systems (e.g., Git), allowing you to track changes, revert to previous versions, and collaborate effectively. This provides a complete history of infrastructure changes and facilitates auditing and troubleshooting.
- Reduced Risk: IaC reduces the risk of human error by automating the infrastructure provisioning and configuration process. This leads to fewer configuration discrepancies and a more stable and reliable environment.
Basic Architecture Diagram
The architecture diagram below illustrates a simplified blue-green deployment setup, highlighting the key components and their relationships. This diagram provides a visual representation of the two environments and the load balancer that directs traffic.
+---------------------+ | Internet | +---------+-----------+ | | (Traffic) | +------------------+------------------+ | Load Balancer | (e.g., AWS ELB, Nginx) | +---------+-----------+ | +-------------------+-------------------+ | | | | +-------------+ | +-------------+ | | | Blue | | | Green | | | | Environment | | | Environment | | | +-------------+ | +-------------+ | | | App Servers | | App Servers | | | | Database | | Database | | | | (Production) | | (Staging/New) | | | +-------------+ | +-------------+ | +-------------------+-------------------+ | | | (Traffic initially directed to Blue) | | | +-------------------------------------------+
In this diagram:
* Internet: Represents the external network accessing the application.
– Load Balancer: This acts as the entry point for all traffic. Initially, it directs all traffic to the Blue environment. During the cutover, the load balancer is configured to redirect traffic to the Green environment.
– Blue Environment: Represents the current production environment.
It includes the application servers and the database. This environment serves the existing production traffic.
– Green Environment: Represents the new, staging environment. It is a replica of the Blue environment, including the new version of the application code and potentially a copy of the production database or a database populated with the new data. The Green environment is initially inactive, receiving no live traffic.
This basic architecture can be extended to include other components, such as caching layers, monitoring systems, and security appliances. The core principle remains the same: two identical environments, with the load balancer acting as the switch between them.
Database Considerations in Blue-Green Deployments
Successfully navigating database migrations is crucial for the seamless operation of blue-green deployments. The database, as the central repository of application data, requires careful planning and execution during the cutover process. This section delves into the strategies for managing database migrations, handling schema changes, and ensuring data consistency throughout the transition.
Strategies for Managing Database Migrations
Managing database migrations involves selecting the appropriate strategy based on the application’s requirements, the complexity of the schema changes, and the desired downtime. Several approaches can be employed, each with its advantages and disadvantages.
- In-Place Migrations with Rollback: This method involves applying database schema changes directly to the active (blue) database. If issues arise, a rollback script is executed to revert to the previous state. This approach minimizes downtime but carries a higher risk of data loss if the rollback fails. The effectiveness depends on the database system’s support for transactional DDL (Data Definition Language) operations.
For instance, in PostgreSQL, using transactions for schema changes is a common practice, allowing for atomic operations and easier rollbacks.
- Dual-Write Approach: In this strategy, both the blue and green databases are updated simultaneously during the migration phase. The application is modified to write data to both databases. Once the green environment is ready, the application is switched over, and the blue database can be decommissioned. This method ensures minimal downtime and reduces the risk of data loss but requires careful consideration of data consistency issues, especially during the initial dual-write period.
The application code must be designed to handle potential inconsistencies between the two databases.
- Data Migration with Cutover: This approach involves migrating the data from the blue database to the green database. This could involve a full data copy or incremental updates using change data capture (CDC) mechanisms. The cutover involves switching the application to use the green database. This method is suitable for large databases where in-place migrations are time-consuming or risky. It allows for parallel processing of the data migration while the blue environment continues to serve traffic.
- Database Cloning: For certain database systems, cloning the existing database to create the green database is a viable option. This minimizes downtime by providing a complete, up-to-date copy of the data. After the cloning process, the schema changes are applied to the green database. The cutover then involves switching the application to the cloned and updated green database.
Examples of Handling Database Schema Changes
Database schema changes must be managed carefully to avoid application downtime or data corruption. Different types of changes require specific approaches.
- Adding a New Column: Adding a new column is generally a safe operation. It can be performed directly on the active database with minimal impact. The application code is then updated to use the new column. The green environment can be updated first, followed by the blue environment, to maintain compatibility during the transition.
- Adding a Non-Nullable Column: Adding a non-nullable column requires careful planning. Since existing rows will not have a value for the new column, a default value must be provided or the column must be added in a separate migration step. For example, in PostgreSQL, you can use the `ALTER TABLE ADD COLUMN` statement with a `DEFAULT` value. The application code then needs to be updated to handle the default values.
- Removing a Column: Removing a column requires careful consideration, as it can impact existing data. The column should be deprecated in the application code before removal. The removal can be performed after ensuring the application no longer uses the column. A separate migration script can be executed to remove the column.
- Changing a Data Type: Changing a data type can be complex, especially if data loss is possible. A migration strategy that includes data conversion and careful testing is crucial. The data type conversion is usually performed in stages. For example, in a conversion from `INT` to `BIGINT`, you can initially add the `BIGINT` column, copy the data, and then switch the application to use the new column.
- Adding Indexes: Adding indexes can improve query performance but may also impact write operations. The impact should be tested in a staging environment before applying the change to the production database. Index creation is often performed during off-peak hours to minimize the impact on performance.
Methods for Ensuring Data Consistency During the Cutover
Maintaining data consistency during the cutover is paramount. Several methods can be used to minimize the risk of data loss or corruption.
- Change Data Capture (CDC): CDC mechanisms capture changes made to the blue database and replicate them to the green database in real-time or near real-time. This ensures that the green database is up-to-date with the latest data. Popular CDC tools include Debezium (for various database systems), AWS Database Migration Service (DMS), and Oracle GoldenGate. The use of CDC minimizes the data synchronization window during the cutover.
- Transaction Management: Using transactions ensures that database operations are atomic, meaning that either all changes are applied, or none are. This is critical for maintaining data integrity, especially during complex schema changes or data migrations. Transactions can be used to wrap multiple SQL statements into a single unit of work.
- Idempotent Migrations: Idempotent migration scripts can be run multiple times without causing unintended side effects. This ensures that the schema changes are applied correctly regardless of how many times the script is executed. The script checks the current state of the database and only applies the changes if they are not already present.
- Testing and Validation: Thorough testing and validation are essential to ensure data consistency. This includes unit tests, integration tests, and end-to-end tests. The data in both the blue and green databases should be validated after each migration step to verify data integrity. Data validation can be performed using SQL queries, checksums, and other techniques.
- Monitoring and Alerting: Implementing robust monitoring and alerting systems is crucial to detect and respond to any data consistency issues during the cutover. Monitoring tools should track database performance, data replication status, and any errors or anomalies. Alerts should be configured to notify the operations team of any critical issues.
Load Balancing and Traffic Routing
Load balancing and traffic routing are critical components in a blue-green deployment strategy, ensuring seamless transitions and minimal disruption to users. They manage the distribution of incoming requests across the active environments, enabling the cutover from the blue environment to the green environment with zero downtime. The proper implementation of these elements is paramount to the success of the deployment.
Role of Load Balancers in Blue-Green Deployments
Load balancers act as the central point of contact for incoming client requests. They sit in front of the blue and green environments, distributing traffic based on configured rules and health checks. This provides several advantages, including high availability, scalability, and the ability to perform the cutover process.
Load balancers facilitate the following functionalities:
- Traffic Distribution: They distribute incoming requests across the available servers in the active environment, preventing any single server from being overloaded.
- Health Checks: They continuously monitor the health of the servers in both the blue and green environments. If a server fails a health check, the load balancer automatically stops sending traffic to it.
- Cutover Control: Load balancers are crucial for directing traffic to the green environment during the cutover. This involves changing the routing rules to shift all or a portion of the traffic from the blue environment to the green environment.
- Rollback Capability: In case of issues with the green environment, the load balancer allows for a quick rollback by rerouting traffic back to the blue environment.
Comparison of Load Balancing Strategies
Various load balancing algorithms can be employed, each with its strengths and weaknesses. The choice of a specific algorithm depends on the application’s requirements and the infrastructure setup.
Common load balancing strategies include:
- Round Robin: This is the simplest strategy, where requests are distributed sequentially to each server in a rotating fashion. It is easy to implement but may not be optimal for handling varying server capacities or request complexities.
- Least Connections: This algorithm directs new requests to the server with the fewest active connections. It is suitable for scenarios where server load is connection-based.
- IP Hash: This strategy uses the client’s IP address to determine which server receives the request. It ensures that a client’s requests are consistently routed to the same server, which is useful for maintaining session affinity.
- Weighted Round Robin: This method assigns weights to each server based on its capacity. Servers with higher weights receive a proportionally larger share of the traffic.
- Least Response Time: This algorithm routes requests to the server with the fastest response time, optimizing for performance.
For example, consider an e-commerce platform with two servers in the blue environment and two servers in the green environment. Using the Round Robin strategy, each incoming request would be distributed cyclically among the four servers. In contrast, using the Least Connections strategy, the load balancer would send new requests to the server with the fewest active connections, potentially balancing the load more effectively.
The Weighted Round Robin strategy would allow for scaling, if one environment has more powerful servers than the other.
Configuring Traffic Routing to the Green Environment
Configuring traffic routing to the green environment is the core of the cutover process. This involves modifying the load balancer’s configuration to direct traffic from the blue environment to the green environment. The process can be executed in different ways.
Here are some common approaches for routing traffic:
- Full Cutover: In this approach, all traffic is instantaneously switched from the blue environment to the green environment. This is the simplest method, but it can lead to a sudden increase in load on the green environment.
- Gradual Rollout (Canary Deployment): This strategy involves routing a small percentage of traffic to the green environment initially and gradually increasing the percentage over time. This allows for monitoring the performance and stability of the green environment before fully switching over. For instance, start with 1% of the traffic, then increase to 10%, 25%, 50%, and finally 100%.
- Blue-Green with A/B Testing: This approach allows you to direct different traffic segments to the blue and green environments. For instance, users with different browser versions, from specific geographic locations, or matching specific user attributes are routed to either the blue or the green environment.
- DNS-Based Routing: Changes to the DNS records can redirect traffic. This is less immediate than load balancer-based routing, as DNS propagation can take time.
An example of a gradual rollout is observed in the software updates of major tech companies. Companies like Netflix or Google frequently utilize canary deployments. They first roll out the update to a small subset of their infrastructure. If the initial performance is acceptable, the rollout is expanded incrementally. If issues are found, the rollout is paused or reversed.
This approach allows for early detection of problems and minimizes the impact on users.
The Migration Cutover Process
The migration cutover process represents the pivotal moment in a blue-green deployment, where the operational workload transitions from the established blue environment to the newly provisioned green environment. This phase demands meticulous planning and execution to minimize downtime and ensure a seamless user experience. Success hinges on precise orchestration of traffic routing, thorough monitoring, and a well-defined rollback strategy in case of unforeseen issues.
Switching Traffic to the Green Environment
The procedure for redirecting user traffic from the blue environment to the green environment involves several critical steps. This process requires a controlled and phased approach to minimize the risk of widespread disruptions.
The primary mechanism for traffic redirection is the load balancer, which acts as the central point of control. The load balancer is initially configured to direct all traffic to the blue environment. The goal is to reconfigure the load balancer to route traffic to the green environment.
- Verification of Green Environment Readiness: Prior to any traffic shift, a comprehensive verification of the green environment’s functionality is essential. This includes verifying application responsiveness, data integrity, and the performance of critical services. This often involves running automated tests and manual checks.
- Pre-Cutover Configuration: Before initiating the cutover, the load balancer must be prepared. This may involve configuring health checks for the green environment, ensuring that it’s correctly registered, and setting up appropriate routing rules.
- Gradual Traffic Shift (Phased Rollout): A phased rollout is often the preferred approach. Instead of switching all traffic at once, a small percentage of traffic is initially routed to the green environment. This allows for monitoring and detection of any immediate issues. The traffic percentage is gradually increased over time, provided no problems are observed. For example, you might start with 1%, then increase to 5%, 10%, 25%, 50%, 75%, and finally 100%.
This incremental approach helps mitigate the impact of any unforeseen errors.
- Monitoring and Alerting: Throughout the traffic shift, continuous monitoring of the green environment’s performance is paramount. This includes monitoring key metrics such as response times, error rates, and resource utilization. Alerts should be configured to trigger automatically if any anomalies are detected.
- Rollback Strategy: A predefined rollback strategy is critical. If issues arise during the cutover, the load balancer can be quickly reconfigured to redirect traffic back to the blue environment. This minimizes the impact on users.
- Final Traffic Shift: Once the green environment is deemed stable and performing optimally, the load balancer is configured to direct 100% of the traffic to the green environment.
- Decommissioning the Blue Environment: After a period of observation and confirmation that the green environment is functioning correctly, the blue environment can be safely decommissioned. This frees up resources and reduces operational costs.
Importance of Monitoring During the Cutover
Continuous and vigilant monitoring during the cutover process is non-negotiable. Monitoring provides real-time insights into the health and performance of the green environment, allowing for rapid detection and resolution of any problems that may arise.
Monitoring encompasses a broad spectrum of metrics, including application performance, server resource utilization, database performance, and user experience. Proactive monitoring, coupled with well-defined alerting rules, ensures that any deviations from expected behavior are immediately flagged, enabling swift corrective action.
- Performance Metrics: Key performance indicators (KPIs) such as response times, transaction throughput, and error rates are carefully tracked. Significant increases in response times or error rates can indicate problems with the green environment.
- Resource Utilization: Monitoring CPU usage, memory consumption, disk I/O, and network traffic provides insights into resource bottlenecks. High resource utilization may indicate inefficient code or resource constraints.
- Database Performance: Database performance metrics, such as query response times and connection pool utilization, are crucial for ensuring data access is not impacted.
- User Experience: Monitoring user experience metrics, such as page load times and session durations, provides a direct measure of user satisfaction. A decrease in user experience metrics could indicate that the new environment is not performing well.
- Alerting and Notifications: Automated alerting systems are configured to trigger notifications based on predefined thresholds for performance metrics. These alerts notify operations teams immediately of any issues. For example, if the error rate exceeds a certain threshold, an alert is triggered, prompting an investigation.
- Logging and Tracing: Detailed logs and transaction tracing are essential for troubleshooting issues. They provide valuable context for identifying the root cause of any problems.
Checklist for the Cutover Procedure
A comprehensive checklist is an indispensable tool for managing the cutover procedure. This checklist ensures that all necessary steps are executed in the correct order and that no critical tasks are overlooked.
The checklist acts as a standardized guide, promoting consistency and reducing the risk of human error. It provides a clear, step-by-step procedure for executing the cutover, ensuring that all stakeholders are aware of their responsibilities and that all critical tasks are completed.
- Preparation:
- Confirm the green environment is fully deployed and tested.
- Verify all database migrations have been completed successfully.
- Review and update the rollback plan.
- Confirm all monitoring and alerting systems are configured correctly.
- Notify stakeholders of the cutover schedule and expected downtime (if any).
- Pre-Cutover Checks:
- Run final health checks on the green environment.
- Verify load balancer configuration.
- Verify DNS settings (if applicable).
- Take a final backup of the database (optional).
- Traffic Shift:
- Gradually shift traffic to the green environment (e.g., 1%, 5%, 10%, 25%, 50%, 75%, 100%).
- Monitor performance metrics in real-time.
- Address any issues immediately.
- Document all steps and observations.
- Post-Cutover Verification:
- Confirm the green environment is handling 100% of the traffic.
- Monitor performance for a predetermined period (e.g., 24 hours).
- Verify data integrity.
- Confirm all services are functioning correctly.
- Rollback (If Necessary):
- If issues are detected, revert traffic to the blue environment immediately.
- Investigate and resolve the issues in the green environment.
- Restart the cutover process once the issues are resolved.
- Decommissioning:
- Once the green environment is confirmed stable, decommission the blue environment.
- Remove any unused resources.
- Update documentation.
Monitoring and Rollback Strategies
Effective monitoring and robust rollback strategies are critical components of a successful blue-green deployment. They provide the necessary mechanisms to observe the performance of the new (green) environment and to revert to the previous (blue) environment if issues arise, minimizing downtime and ensuring service availability. Real-time insights and pre-defined procedures are key to mitigating risks associated with the migration.
The Importance of Real-Time Monitoring
Real-time monitoring is paramount during a blue-green deployment, allowing for immediate detection of anomalies and performance degradation in the green environment. It provides a continuous feedback loop, enabling engineers to quickly assess the health of the application and its infrastructure. The ability to observe system behavior as changes are rolled out is crucial for maintaining a stable and performant service.
Failure to monitor in real-time can lead to undetected problems, potentially resulting in widespread service outages and significant business impact.
Examples of Metrics to Monitor During and After Deployment
Comprehensive monitoring involves tracking a variety of metrics to gain a holistic understanding of the system’s health. The following are crucial metrics to monitor during and after deployment:
- Application Performance Metrics: These metrics provide insights into the responsiveness and efficiency of the application.
- Response Time: Measure the time taken for the application to respond to user requests. A sudden increase in response time can indicate performance bottlenecks or resource constraints. For example, an increase in average response time from 200ms to 1 second would be a red flag.
- Error Rates: Track the rate of errors, such as HTTP 500 errors or application-specific exceptions. A high error rate signals potential problems with the code, configuration, or dependencies. For instance, an increase in the rate of 500 errors from 0.1% to 5% would be a critical indicator.
- Throughput: Measure the number of requests processed per unit of time. A decrease in throughput can indicate performance issues or resource limitations.
- Infrastructure Metrics: These metrics provide insights into the underlying infrastructure resources.
- CPU Utilization: Monitor the percentage of CPU usage on the servers. High CPU utilization can indicate that the servers are overloaded. For example, if CPU utilization consistently exceeds 80%, it suggests a potential need for scaling.
- Memory Utilization: Track the amount of memory used by the servers. High memory utilization can lead to performance degradation and potential crashes.
- Disk I/O: Monitor disk input/output operations per second (IOPS). High disk I/O can indicate disk bottlenecks.
- Database Metrics: These metrics provide insights into the database performance and health.
- Query Performance: Track the execution time of database queries. Slow queries can significantly impact application performance.
- Connection Pool Utilization: Monitor the number of database connections in use. Insufficient connection pool size can lead to connection errors.
- Replication Lag: For replicated databases, monitor the lag between the primary and secondary databases. Significant lag can impact data consistency.
- User Experience Metrics: These metrics provide insights into the user experience.
- Page Load Time: Measure the time it takes for web pages to load in a user’s browser. Slow page load times can lead to user frustration.
- Conversion Rates: Track the percentage of users who complete a desired action, such as making a purchase. A drop in conversion rates can indicate problems with the application or user experience.
These metrics, when monitored in conjunction, offer a comprehensive view of the system’s health and performance, enabling proactive identification and resolution of issues.
Rollback Procedures if Issues Arise in the Green Environment
A well-defined rollback procedure is crucial for mitigating the impact of issues encountered in the green environment. The primary goal of a rollback is to quickly revert to the stable blue environment, minimizing downtime and data loss.
- Triggering the Rollback: The decision to rollback should be based on pre-defined thresholds and alerts generated by the monitoring system. For example, if the error rate exceeds a certain percentage or response times increase significantly, the rollback process should be initiated automatically.
- Reverting Traffic: The primary step in a rollback is to revert traffic back to the blue environment. This typically involves modifying the load balancer configuration to direct all traffic to the blue environment. This process should be fast and automated.
- Database Considerations: Depending on the database changes made during the deployment, specific database rollback steps might be necessary.
- Schema Changes: If schema changes were deployed, these changes might need to be rolled back. This can involve restoring a database backup or running scripts to revert the schema changes.
- Data Migration: If data migration was performed during the deployment, consider data consistency. In some cases, data migrated to the green environment might need to be reconciled with the data in the blue environment.
- Monitoring the Rollback: After initiating the rollback, continuous monitoring is crucial to ensure the blue environment is functioning correctly. This includes verifying application performance, error rates, and user experience metrics.
- Post-Mortem Analysis: After a successful rollback, a post-mortem analysis should be conducted to identify the root cause of the issues and prevent similar problems in the future. This analysis should include reviewing logs, metrics, and deployment processes.
By implementing these procedures, organizations can ensure a swift and effective response to issues, minimizing the impact of deployment failures and maintaining service availability. The effectiveness of a rollback procedure is directly proportional to the level of preparation and automation involved.
Testing and Validation
Thorough testing and validation are paramount in blue-green deployments to ensure a smooth transition and minimize the risk of downtime or service disruptions during the cutover. Rigorous testing confirms the functionality, performance, and security of the green environment before it handles live traffic. This meticulous process provides confidence in the new environment and facilitates a quick rollback to the blue environment if issues arise.
Importance of Thorough Testing Before Cutover
Before directing user traffic to the green environment, comprehensive testing is essential. It serves as a crucial checkpoint to identify and rectify any defects or performance bottlenecks that might exist. Neglecting this phase could lead to significant problems.
- Risk Mitigation: Comprehensive testing significantly reduces the risk of deploying a faulty system, which could negatively impact user experience, damage brand reputation, and lead to financial losses.
- Performance Validation: Testing verifies that the green environment can handle the expected load and performs optimally under various conditions, ensuring that the transition doesn’t degrade performance.
- Functional Accuracy: It confirms that all functionalities and features of the application work correctly in the green environment, mirroring the functionality of the blue environment.
- Security Assurance: Security testing, including vulnerability scans and penetration testing, is vital to identify and address potential security weaknesses before exposing the new environment to live traffic.
- User Experience: Rigorous testing ensures that the user experience remains consistent and that any issues are addressed before they affect the end-users.
Comparison of Testing Strategies
Several testing strategies can be employed in blue-green deployments, each with its specific focus and purpose. Combining different testing types provides a more complete validation process.
- Smoke Tests: Smoke tests are a quick set of initial tests to ensure that the core functionalities of the application are working correctly. They are designed to verify that the basic functionality is intact before proceeding with more in-depth testing.
Smoke tests are analogous to a “smoke test” in hardware, where the device is turned on to see if it “smokes” or fails immediately.
- Functional Tests: Functional tests validate that individual features and components of the application function as expected. These tests cover various scenarios, including user input, data processing, and output verification.
- Performance Tests: Performance tests evaluate the application’s performance under various load conditions. These tests help identify bottlenecks and ensure the system can handle the anticipated user traffic. Load testing and stress testing are commonly used to assess performance.
For example, consider an e-commerce platform. Performance testing would simulate a surge in traffic during a flash sale to determine if the system can handle the increased load without slowing down.
- User Acceptance Testing (UAT): UAT involves end-users testing the application in a realistic environment to ensure that it meets their requirements and expectations. This testing phase is critical for identifying usability issues and ensuring that the system meets business needs.
For instance, in a banking application, UAT would involve actual bank users testing the new system’s functionalities like fund transfers, bill payments, and account management to ensure the features align with their expectations.
- Integration Tests: Integration tests verify the interaction between different components and systems. They ensure that various parts of the application and its integrations work seamlessly together.
- Security Tests: Security tests, including penetration testing and vulnerability scanning, assess the application’s security posture. These tests aim to identify vulnerabilities and ensure that the system is protected against potential threats.
Methods for Validating the New Environment
Validating the green environment involves several methods to confirm its readiness for live traffic. These methods focus on different aspects of the system to ensure a comprehensive evaluation.
- Automated Testing: Automating tests, including functional, performance, and security tests, is essential for efficient and repeatable validation. Automated tests can be run frequently, providing rapid feedback on the state of the green environment.
- Canary Releases: Canary releases involve directing a small percentage of live traffic to the green environment while monitoring its performance and behavior. This allows for detecting issues in a controlled environment before impacting a large user base.
For example, a company might route 5% of its traffic to the green environment. If no errors are observed, the percentage can be gradually increased.
- A/B Testing: A/B testing can be used to compare different versions of the application (blue and green) side by side. This method can help determine which version performs better based on user behavior metrics.
- Monitoring and Alerting: Implementing robust monitoring and alerting systems is crucial for detecting and responding to issues in the green environment. Monitoring tools track key performance indicators (KPIs) such as response times, error rates, and resource utilization. Alerts notify the operations team when anomalies occur.
- Real-time Data Comparison: Comparing real-time data between the blue and green environments provides insight into data consistency and application behavior. This can include comparing database records, transaction logs, and API responses.
- Rollback Readiness: Validate that the rollback process is functioning correctly. Simulate a rollback scenario to ensure that the blue environment can be quickly restored if issues arise in the green environment. This validation includes testing the data synchronization mechanisms to prevent data loss.
Automation and Tooling
Automating blue-green deployments is critical for achieving the benefits of this deployment strategy, namely reduced downtime and risk. Automation minimizes human error, streamlines the process, and enables faster and more frequent deployments. This section details the advantages of automating deployments and the types of tools used to achieve this.
Benefits of Automated Deployment
Automating blue-green deployments offers several key advantages. These benefits translate to increased efficiency, reduced risk, and improved reliability for software releases.
- Reduced Downtime: Automation minimizes the manual steps involved in the cutover process. This, in turn, accelerates the transition, significantly decreasing the time the application is unavailable to users. For example, consider a scenario where a manual cutover takes 2 hours. Automation can reduce this to minutes, resulting in a dramatic improvement in service availability.
- Reduced Risk: Automated processes are less prone to human error, such as incorrect configuration or missed steps. This leads to a reduction in deployment-related incidents and rollback scenarios. For instance, automated scripts can consistently configure the environment, reducing the chance of misconfigurations that could lead to system failures.
- Increased Speed of Deployment: Automation enables faster deployments, allowing for more frequent releases and quicker delivery of new features and bug fixes. This faster feedback loop enables quicker iterations and faster adaptation to market needs.
- Improved Consistency: Automated deployments ensure consistent configurations across environments, reducing the likelihood of discrepancies between the blue and green environments. This consistency makes it easier to troubleshoot issues and improves the overall reliability of the deployment process.
- Enhanced Scalability: Automated processes can be easily scaled to handle deployments across multiple environments and to manage complex application architectures. This scalability is crucial for supporting growing application needs.
- Simplified Rollback: Automated rollback procedures are simpler and faster to execute, reducing the impact of deployment failures. The automation scripts can automatically revert to the previous working version of the application.
Tools Commonly Used for Blue-Green Deployments
A variety of tools can be used to automate blue-green deployments. These tools encompass configuration management, continuous integration/continuous delivery (CI/CD) pipelines, infrastructure-as-code (IaC), and load balancing solutions.
- Configuration Management Tools: Tools like Ansible, Chef, and Puppet automate the configuration of servers and applications, ensuring consistent environments. They manage the deployment of software, configurations, and dependencies.
- CI/CD Pipelines: CI/CD tools, such as Jenkins, GitLab CI, and CircleCI, orchestrate the entire deployment process, from code commit to production release. They automate building, testing, and deploying applications.
- Infrastructure-as-Code (IaC) Tools: IaC tools, including Terraform and AWS CloudFormation, allow infrastructure to be defined and managed as code. This enables automated provisioning and configuration of the blue and green environments.
- Load Balancers: Load balancers, such as HAProxy, Nginx, and cloud-based load balancers like AWS Elastic Load Balancing (ELB), are essential for directing traffic between the blue and green environments during the cutover process.
- Container Orchestration: Container orchestration tools, like Kubernetes and Docker Swarm, simplify the management and scaling of containerized applications, making blue-green deployments easier to implement and manage.
Comparison of Deployment Tools
The selection of deployment tools should be based on the specific requirements of the project, including the application architecture, existing infrastructure, and team expertise. The following table provides a comparison of popular deployment tools.
| Tool | Key Features | Pros | Cons |
|---|---|---|---|
| Jenkins | Open-source CI/CD server; extensive plugin ecosystem; supports a wide range of build and deployment tasks. | Highly customizable; large community support; integrates well with various tools and technologies. | Can be complex to configure and maintain; requires significant setup and configuration. |
| GitLab CI | Integrated CI/CD pipelines within GitLab; supports automatic testing, building, and deployment; uses a declarative YAML configuration file. | Easy to set up and integrate with GitLab; user-friendly interface; excellent for version control and CI/CD. | Tightly coupled with GitLab; less flexible than some other options. |
| CircleCI | Cloud-based CI/CD platform; supports parallel testing and builds; offers fast build times and automated deployments. | Easy to set up and use; integrates well with various platforms; offers fast and reliable performance. | Can be expensive for larger projects; limited customization options compared to Jenkins. |
| Terraform | Infrastructure-as-code tool; allows the definition and management of infrastructure resources; supports multiple cloud providers. | Declarative configuration; supports infrastructure versioning; enables infrastructure automation. | Steeper learning curve than some other tools; can be complex to manage large infrastructures. |
Real-World Use Cases and Examples
Blue-green deployments have become a cornerstone of modern software delivery, enabling organizations to reduce downtime, mitigate risks, and improve the overall user experience during application updates and migrations. This section explores real-world examples and case studies, demonstrating the practical application and impact of blue-green deployments across diverse industries and application architectures. The examples provided showcase the versatility and benefits of this deployment strategy, including improvements in performance, reduced risk, and streamlined rollbacks.
Successful Implementations of Blue-Green Deployments
Several prominent companies have adopted blue-green deployments to enhance their software delivery processes. These examples illustrate how the strategy can be applied to different scenarios and application complexities.
- Netflix: Netflix, a global streaming giant, utilizes blue-green deployments extensively to update its platform. The company’s architecture, built on microservices, allows for granular updates and testing of new features. The implementation of blue-green deployments facilitates seamless updates to its vast infrastructure, minimizing disruptions for millions of users worldwide. Netflix can switch between green and blue environments rapidly, ensuring a consistent and high-quality streaming experience.
This approach enables Netflix to test new features and updates in a production-like environment without affecting the live user base. This strategy is critical for managing a platform with millions of concurrent users and frequent feature releases.
- Shopify: Shopify, an e-commerce platform provider, leverages blue-green deployments to ensure the availability and stability of its platform for millions of merchants. The platform’s complex infrastructure and frequent updates necessitate a robust deployment strategy. Shopify uses blue-green deployments to perform updates with minimal downtime. The process includes the simultaneous operation of two environments and a gradual switch of traffic to the new environment, while monitoring for any issues.
The implementation allows Shopify to quickly roll back to the previous version if problems arise, ensuring the platform remains operational.
- Atlassian: Atlassian, the developer of popular collaboration tools like Jira and Confluence, uses blue-green deployments to deliver frequent updates to its cloud-based services. The company employs this method to ensure its services are available and perform well during upgrades. The approach enables Atlassian to release new features and bug fixes quickly, maintaining high availability and minimizing disruption to its user base.
The implementation of blue-green deployments is critical for maintaining a positive user experience and ensuring the reliability of its services.
Case Studies Detailing Blue-Green Deployment Implementations
These case studies delve into specific implementations, providing detailed insights into the challenges, solutions, and outcomes of blue-green deployments. The examples highlight the technical aspects, decision-making processes, and quantifiable results achieved.
- Case Study 1: E-commerce Platform Migration
An e-commerce company, with a monolithic application, decided to migrate its infrastructure to the cloud and modernize its deployment process. The company implemented a blue-green deployment strategy to facilitate the migration. The initial setup involved creating identical blue and green environments in the cloud. The green environment served as the active production environment, while the blue environment was used for testing and staging the migrated application.
The migration was carried out in phases, with each component or service migrated to the blue environment and tested thoroughly before being switched over. The traffic was gradually routed to the blue environment after each successful migration, ensuring that users experienced minimal disruption. This approach enabled the company to migrate its entire application to the cloud with zero downtime, and reduced the risk of critical failures during the transition.
The successful implementation of the blue-green deployment led to a significant improvement in deployment frequency and a reduction in deployment-related issues.
- Case Study 2: Financial Services Application Update
A financial services firm required a deployment strategy to update its core banking application, which had stringent availability requirements. The firm implemented a blue-green deployment to update the application without downtime. The process began by establishing a new green environment that mirrored the existing blue environment. The new version of the banking application was deployed to the green environment and tested rigorously.
After the tests were successfully completed, traffic was switched from the blue environment to the green environment. Monitoring was implemented to detect any performance degradation or errors. In case of any issues, the firm could quickly switch back to the blue environment. The blue-green deployment enabled the firm to update its critical application with zero downtime, reduced the risk of application failures, and provided a streamlined rollback mechanism.
Impact of Blue-Green Deployments on Application Performance
Blue-green deployments can have a significant impact on application performance. The ability to test new releases in a production-like environment before they go live allows organizations to identify and address performance bottlenecks. The strategy also facilitates the deployment of performance enhancements and optimizations without disrupting user experience.
- Reduced Downtime: The most immediate impact of blue-green deployments is the elimination of downtime during deployments. By switching traffic between environments, applications can be updated without interrupting user access. This improvement is critical for applications with high availability requirements.
- Improved Response Times: Deploying to a new environment and thoroughly testing before directing live traffic can allow performance improvements. The new version of the application can be optimized in the green environment before the switchover, reducing response times for users.
- Reduced Risk of Performance Degradation: Thorough testing in a production-like environment allows organizations to identify performance issues before they impact users. This reduces the risk of deploying a slow or unstable application version.
- Simplified Rollbacks: The ability to quickly switch back to the previous environment provides a safety net if performance issues arise. This quick rollback capability minimizes the impact of performance problems on users.
Ultimate Conclusion
In summation, the exploration of what is a blue-green deployment for migration cutover unveils a transformative methodology for modern software deployment and migration. By embracing the principles of environment duplication, strategic load balancing, comprehensive testing, and meticulous monitoring, organizations can achieve near-zero downtime, reduce deployment risks, and maintain continuous service availability. The success of blue-green deployments hinges on careful planning, robust automation, and a proactive approach to addressing potential challenges.
Ultimately, the adoption of this strategy represents a significant step towards achieving agility, resilience, and operational excellence in the dynamic landscape of software development.
Detailed FAQs
What is the primary goal of a blue-green deployment?
The primary goal is to minimize downtime during deployments and migrations, enabling a seamless transition between application versions or infrastructure configurations while maintaining service availability.
How does blue-green deployment differ from a traditional deployment?
Traditional deployments often involve updating the existing environment directly, which can lead to downtime or service disruptions. Blue-green deployments, on the other hand, utilize two separate environments, allowing for testing and validation of the new version before switching over traffic.
What are the key components of a blue-green deployment architecture?
Key components include two identical environments (blue and green), a load balancer to manage traffic routing, a database strategy to handle data migrations, and a monitoring system to track performance and identify issues.
How is the database handled during a blue-green deployment?
Database changes are managed through strategies such as schema migrations and data synchronization. The goal is to ensure data consistency between the blue and green environments and facilitate a smooth transition during the cutover.
What happens if there are issues in the green environment after the cutover?
A rollback strategy is implemented, allowing for a quick return to the blue environment if issues are detected. This ensures that the application continues to function without significant disruption.