Embark on a journey into the world of Open Policy Agent (OPA), a powerful and versatile tool revolutionizing policy enforcement in modern software architectures. This guide will illuminate how OPA empowers organizations to manage and enforce policies across diverse systems, from microservices to APIs, ensuring consistent and secure operations. We’ll delve into OPA’s core concepts, architecture, and practical applications, transforming the complex landscape of policy management into an accessible and manageable process.
This exploration covers everything from understanding the Rego policy language to integrating OPA with various systems and optimizing performance. We’ll examine real-world use cases, advanced features, and strategies for testing, debugging, and monitoring OPA. By the end of this guide, you’ll possess the knowledge and tools to leverage OPA effectively, streamlining your policy enforcement efforts and bolstering your overall security posture.
Introduction to Open Policy Agent (OPA)
Open Policy Agent (OPA) is a powerful, open-source policy engine that enables unified policy enforcement across a wide range of software systems. It provides a declarative language, Rego, for defining policies and allows for decoupling policy decision-making from the core application logic. This approach enhances security, simplifies compliance, and improves overall system manageability.
Core Concepts of OPA and Its Role in Policy Enforcement
OPA operates on the principle of “policy as code,” treating policies as programmable artifacts that can be versioned, tested, and deployed alongside application code. Its core function revolves around evaluating data against defined policies to make authorization decisions.
- Policy Definition: Policies are written in Rego, a declarative language specifically designed for expressing complex rules. Rego’s syntax allows for clear and concise policy definitions, making them easier to understand and maintain. For instance, a policy could define access control rules, data validation checks, or resource allocation limits.
- Data Input: OPA receives input data, which can include information about users, resources, and actions. This data is used in conjunction with the defined policies to evaluate the relevant rules. The input data can be sourced from various systems, such as databases, APIs, or configuration files.
- Evaluation and Decision: OPA evaluates the input data against the defined policies. This evaluation process determines whether the data satisfies the policy rules. The result of the evaluation is a decision, typically a boolean value (allow/deny) or a more complex data structure representing the outcome.
- Enforcement: The decision made by OPA is then used by the application or system to enforce the policy. This can involve granting or denying access, validating data, or taking other actions based on the policy outcome.
Concise Definition of OPA and Key Benefits
Open Policy Agent (OPA) is a general-purpose policy engine that unifies policy enforcement across the cloud-native stack. It offers a centralized and consistent approach to policy management, enabling organizations to define and enforce policies in a declarative and auditable manner.Key benefits include:
- Centralized Policy Management: OPA provides a single point of control for defining and managing policies, eliminating the need to scatter policy logic across different applications and systems.
- Policy as Code: Policies are defined in code (Rego), enabling version control, testing, and automated deployment, promoting consistency and repeatability.
- Decoupled Policy Enforcement: OPA separates policy decision-making from the application logic, allowing for easier updates and modifications to policies without impacting the core application functionality.
- Improved Security and Compliance: OPA helps enforce security best practices and compliance requirements consistently across the organization.
- Extensibility and Integration: OPA integrates seamlessly with various systems and technologies, including Kubernetes, Docker, APIs, and databases.
Brief History of OPA’s Development and Evolution
OPA was initially developed by Styra, a company focused on policy-based control for cloud-native applications. The project was open-sourced in 2016 and has since gained significant traction within the cloud-native community.The evolution of OPA has been marked by continuous improvements and feature enhancements, including:
- Early Development: The initial focus was on providing a robust and flexible policy engine for Kubernetes and other cloud-native environments.
- Community Growth: As the project gained popularity, a strong community emerged, contributing to the development of new features, integrations, and documentation.
- Expansion of Use Cases: OPA’s applicability expanded beyond Kubernetes to encompass a wide range of use cases, including API authorization, data validation, and infrastructure management.
- Formalization and Standardization: The project has been embraced by the Cloud Native Computing Foundation (CNCF), further solidifying its position as a key component of the cloud-native ecosystem.
The Problem OPA Solves in Modern Software Architectures
Modern software architectures, particularly in cloud-native environments, are characterized by their complexity, distributed nature, and the need for rapid iteration. This poses significant challenges for policy enforcement. OPA addresses these challenges by providing a unified and consistent approach to policy management.Here are the key problems OPA solves:
- Inconsistent Policy Enforcement: Without a centralized policy engine, policies are often implemented ad-hoc across different applications and services, leading to inconsistencies and security vulnerabilities.
- Difficult Policy Updates: Modifying policies can be a time-consuming and error-prone process, especially when policies are embedded within application code.
- Lack of Visibility and Auditability: Tracking policy decisions and ensuring compliance can be difficult without a centralized logging and auditing mechanism.
- Complexity and Scalability: As systems grow in size and complexity, managing and enforcing policies becomes increasingly challenging.
- Vendor Lock-in: Relying on vendor-specific policy solutions can limit flexibility and make it difficult to adopt new technologies.
OPA solves these problems by providing a centralized, declarative, and extensible policy engine that can be easily integrated into various software systems, enabling organizations to enforce policies consistently, securely, and efficiently. For example, a company using Kubernetes can define policies with OPA to ensure that only authorized users can deploy pods with specific resource requests and limits. This centralized approach simplifies policy management and enhances security.
OPA’s Architecture and Components
Open Policy Agent (OPA) functions as a powerful, general-purpose policy engine. Understanding its architecture and components is crucial for effectively leveraging its capabilities in various policy enforcement scenarios. This section details the core elements that make OPA function and how they interact.
Major Components of OPA
OPA’s functionality is built upon a few key components that work in concert to evaluate and enforce policies. These components, working together, provide a robust and flexible policy enforcement solution.
- Policy Engine: The core of OPA is the policy engine. This engine is responsible for evaluating policies against input data and producing a decision. It takes input data, loads the policies written in Rego, and returns the evaluation results. The policy engine is designed for performance and scalability, allowing it to handle complex policies and large volumes of data.
- Policy Language (Rego): Rego is the declarative query language used to write policies for OPA. Rego allows you to define policies in a clear and concise manner, making them easy to understand and maintain. Rego is designed to be expressive enough to handle a wide range of policy requirements, from simple access control rules to complex business logic.
Example:
package example.authzallow
input.method == "GET"
input.path == ["/data"]This simple Rego policy grants access to the /data endpoint via GET requests.
- Bundle Server: OPA utilizes a bundle server to manage and distribute policies and associated data. This server is responsible for serving the policies and data that OPA needs to evaluate. The bundle server ensures that OPA always has the latest version of the policies and data it needs. This is crucial for ensuring policy consistency and up-to-date enforcement.
- Decision Logs: OPA can generate decision logs that provide valuable insights into policy evaluations. These logs contain information about the input data, the evaluated policies, and the resulting decisions. Decision logs are crucial for auditing, debugging, and monitoring policy enforcement. They allow administrators to understand why a particular decision was made and to identify any potential issues with the policies.
OPA’s Integration with Different Systems and Services
OPA’s versatility stems from its ability to integrate seamlessly with a wide array of systems and services. This flexibility makes it adaptable to various environments, from cloud-native applications to traditional on-premise infrastructure.
- API Gateways: OPA can be integrated with API gateways to enforce access control policies. The API gateway acts as a proxy, intercepting requests and passing them to OPA for evaluation. Based on the policy evaluation results, the gateway either allows or denies the request. Examples include Kong, Envoy, and Tyk.
- Kubernetes: In Kubernetes environments, OPA can be used to enforce admission control policies. OPA intercepts requests to the Kubernetes API server and validates them against defined policies. This helps to ensure that only valid configurations are deployed. Gatekeeper is a popular project that integrates OPA with Kubernetes.
- Service Meshes: OPA can be integrated with service meshes like Istio to enforce policies at the service level. This allows for fine-grained control over service-to-service communication, including authorization and traffic management.
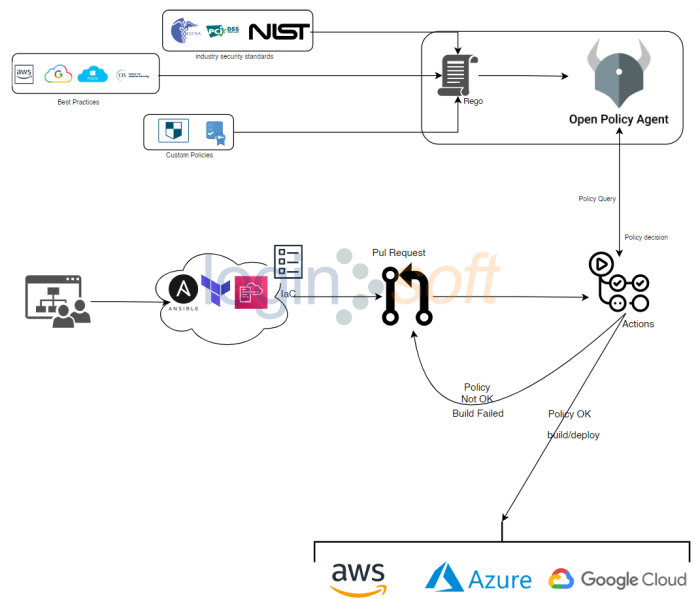
- CI/CD Pipelines: OPA can be incorporated into CI/CD pipelines to validate infrastructure-as-code configurations. This ensures that infrastructure changes comply with organizational policies before they are deployed. Tools like Terraform can be integrated with OPA for policy enforcement.
- Custom Applications: OPA can be embedded directly into custom applications to provide policy enforcement capabilities. This allows developers to incorporate policy decisions directly into their application logic.
Communication Channels and Protocols Used by OPA
OPA utilizes various communication channels and protocols to interact with different systems and services, ensuring efficient and reliable policy enforcement. These communication methods are essential for OPA’s operational efficiency.
- HTTP/HTTPS: OPA typically communicates with other systems using HTTP or HTTPS. This is the standard protocol for RESTful APIs, making it easy to integrate OPA with various services.
- gRPC: gRPC is a high-performance, open-source remote procedure call (RPC) framework that OPA can use for communication. gRPC provides a more efficient way to exchange data compared to HTTP, especially in high-throughput environments.
- WebSockets: OPA can utilize WebSockets for real-time policy updates and decision streaming. This allows for dynamic policy enforcement and immediate responses to changes in input data.
- Configuration Management Systems (e.g., Consul, etcd): OPA can integrate with configuration management systems to receive policy updates and data. These systems act as a central repository for policies and data, ensuring consistency across all OPA instances.
- Custom Integrations: OPA’s flexibility allows for custom integrations using various protocols and communication methods, depending on the specific requirements of the environment.
OPA Architecture Diagram
The following diagram illustrates the architecture of OPA and its interactions with various components.
The diagram illustrates the flow of a request through OPA.
The diagram is structured as follows:
The center of the diagram is the “Open Policy Agent (OPA)” box, which contains the “Policy Engine” and a connection to the “Rego Policies” data store.
On the left side of the diagram, there is a “Client Application” box, which sends a “Request” to OPA.
The “Request” arrow goes into the “OPA” box.
OPA also receives “Input Data” from a “Data Source”.
On the right side of the diagram, there is an “Enforcement Point” box.
OPA sends a “Decision” to the “Enforcement Point”, which then takes an “Action” based on the decision.
The “Enforcement Point” could be an API Gateway, Kubernetes, or a Service Mesh.
The diagram shows a simplified flow where the client application makes a request, OPA evaluates the request against its policies and data, and the enforcement point acts on the decision. The data source provides input data to OPA, while Rego policies define the rules.
Installing and Configuring OPA
To effectively utilize Open Policy Agent (OPA), proper installation and configuration are essential. This section provides a comprehensive guide to setting up OPA on different operating systems and configuring it for your specific needs. We’ll cover the installation process, basic configuration options, verification steps, and a sample configuration file to get you started.
Installing OPA
The installation process for OPA varies depending on the operating system. Here are the steps for installing OPA on the most common platforms:
- Linux (using package manager): The easiest way to install OPA on Linux is typically through your distribution’s package manager. For example, on Debian/Ubuntu systems, you can use `apt`:
- Update the package list:
sudo apt update - Install OPA:
sudo apt install opa - Verify installation (see below).
On Red Hat/CentOS/Fedora systems, use `yum` or `dnf`:
- Update the package list:
sudo yum updateorsudo dnf update - Install OPA:
sudo yum install opaorsudo dnf install opa - Verify installation (see below).
- Update the package list:
- macOS (using Homebrew): Homebrew is a popular package manager for macOS. To install OPA using Homebrew:
- Update Homebrew:
brew update - Install OPA:
brew install open-policy-agent - Verify installation (see below).
- Update Homebrew:
- Windows (using Chocolatey): Chocolatey is a package manager for Windows. To install OPA using Chocolatey:
- Install Chocolatey (if you don’t have it already).
- Open an elevated command prompt (run as administrator).
- Install OPA:
choco install opa - Verify installation (see below).
- From Binaries: You can download pre-built binaries from the OPA releases page on GitHub (https://github.com/open-policy-agent/opa/releases).
- Download the appropriate binary for your operating system.
- Extract the binary to a location in your system’s PATH (e.g.,
/usr/local/binon Linux/macOS or a directory in your PATH on Windows). - Verify installation (see below).
- From Source (for developers): If you want to build OPA from source, you’ll need Go installed.
- Clone the OPA repository:
git clone https://github.com/open-policy-agent/opa.git - Navigate to the OPA directory:
cd opa - Build OPA:
go build -o opa ./cmd/opa - Move the built binary to a location in your PATH.
- Verify installation (see below).
- Clone the OPA repository:
Basic Configuration Options for OPA
OPA’s configuration is managed through command-line flags and a configuration file, usually named `config.yaml` or `config.json`. The configuration file allows you to define various settings, including network settings, logging levels, and other operational parameters.
- Network Settings: OPA can be configured to listen on specific network interfaces and ports.
--server: Starts OPA in server mode, listening for HTTP requests.--addr: Specifies the address to listen on (default:0.0.0.0, which listens on all interfaces).--port: Specifies the port to listen on (default:8181).
For example, to start OPA on port 8181:
opa run --server --port 8181. - Logging: OPA supports different logging levels to control the verbosity of the output.
--log-level: Sets the log level (e.g.,info,debug,warn,error). The default isinfo.
For example, to set the log level to debug:
opa run --server --log-level debug. - Configuration File: Using a configuration file allows for more complex setups and persistent settings. The configuration file is usually loaded using the
--configflag.
Verifying a Successful OPA Installation
After installing OPA, it’s important to verify that the installation was successful. This involves checking the OPA version and ensuring that the OPA server is running correctly.
- Check the OPA version: Run the following command in your terminal:
opa version. This should display the installed OPA version. - Start the OPA server: Start the OPA server using the command:
opa run --server. This command starts OPA in server mode, listening on the default port (8181). - Test the OPA server: You can test the server by sending a simple query using `curl` or another HTTP client. For example:
curl -X POST -d '"query": "data.example.allow"' http://localhost:8181/v1/data. If OPA is running correctly and you have a policy loaded, you should receive a response. If you get a “connection refused” error, it indicates the server isn’t running or is not accessible on the specified port.
Sample Configuration File for a Basic OPA Setup
Here’s a sample `config.yaml` file that demonstrates basic configuration options. This configuration sets the server to listen on port 8181, sets the log level to `info`, and specifies a directory for policy files.“`yamlservices:
address
0.0.0.0 port: 8181 protocol: http tls: enabled: false
address
0.0.0.0 port: 9191 protocol: grpc tls: enabled: falsedecision_logs: truelog_level: infobundles:
id
my-policies resource: policies path: /policies format: rego services:
service
default address: 0.0.0.0 port: 8181 protocol: http tls: enabled: false“`This configuration file:
- Defines two services, one for HTTP and one for gRPC, listening on all interfaces (
0.0.0.0) on ports 8181 and 9191, respectively. - Sets the decision logs to be enabled.
- Sets the log level to
info. - Specifies a bundle with ID “my-policies” to load policies from the “/policies” path. The policies are in rego format.
To use this configuration file, save it as `config.yaml` and start OPA using: opa run --config config.yaml. You can then place your Rego policies in a directory named `policies` in the same directory as the `config.yaml` file.
Writing Policies with Rego
Now that we’ve covered the foundational aspects of Open Policy Agent (OPA), including its architecture and setup, we’ll delve into the heart of OPA: the Rego policy language. Rego allows you to define and enforce policies across your systems, enabling fine-grained access control, compliance checks, and much more. This section will provide a comprehensive guide to writing effective Rego policies.
The Syntax and Structure of the Rego Policy Language
Rego is a declarative query language designed for expressing policies. It’s built upon the principles of Datalog and is designed to be easy to read and understand. The core structure revolves around rules, which are the building blocks of your policies.The basic structure of a Rego policy file consists of:* Package Declaration: Defines the namespace for the policy.
This helps organize policies and prevent naming conflicts.
Import Statements
Imports other packages or external data.
Rules
The core logic of the policy, defining how decisions are made. Rules can be simple or complex, depending on the policy requirements.
Comments
Used for documentation and to explain the policy logic.Here’s a basic example illustrating the structure:“`regopackage my.packageimport data.usersallow user := input.user users[user].role == “admin”deny not allow“`In this example:* `package my.package` declares the policy’s namespace.
- `import data.users` imports data from an external source (which is assumed to be loaded into OPA).
- The `allow` rule defines when access is granted. It checks if the user’s role is “admin”.
- The `deny` rule defines when access is denied. It denies access if the `allow` rule doesn’t grant it.
Rego’s syntax is designed to be intuitive:* Variables: Start with a lowercase letter (e.g., `user`, `role`).
Operators
Use standard operators like `=`, `!=`, ` <`, `>`, `&&` (and), `||` (or), and `!` (not).
Data Structures
Supports arrays, objects (JSON-like structures), and sets.
Built-in Functions
Offers a rich set of built-in functions for string manipulation, data validation, and more.
Simple Rego Policies for Access Control
Access control is a common use case for OPA. Let’s look at some simple examples to illustrate how Rego can be used to manage access.Consider a scenario where you want to control access to a resource based on a user’s role. We can define a policy that checks the user’s role against a list of allowed roles.Here’s a policy example:“`regopackage authz.accessimport data.rolesallow user := input.user resource := input.resource roles[user].permissions[resource] == true“`In this policy:* `input.user` and `input.resource` represent the user and the resource being accessed, respectively.
These are provided as input to OPA.
`data.roles` is assumed to contain user roles and permissions. For example
“`json “roles”: “alice”: “permissions”: “read”: true, “write”: false , “bob”: “permissions”: “read”: true, “write”: true “`* The `allow` rule grants access if the user has the necessary permission for the resource.Another example, demonstrating denying access based on a specific condition:“`regopackage authz.accessdeny input.method == “DELETE” input.user == “guest”“`This policy denies DELETE requests from the “guest” user.These examples showcase the flexibility of Rego.
You can easily adapt these policies to enforce various access control requirements.
Defining Variables, Functions, and Rules in Rego
Rego offers features that enable writing complex and reusable policies. Variables: Variables are used to store values and make policies more readable.“`regopackage exampleallow user := input.user resource := input.resource is_admin(user) resource == “sensitive_data”is_admin(user) data.users[user].role == “admin”“`In this example, `user` and `resource` are variables. Functions: Functions allow you to encapsulate logic and reuse it throughout your policies.
They improve readability and maintainability.“`regopackage exampleis_allowed(user, resource) has_permission(user, resource)has_permission(user, resource) data.permissions[user][resource] == true“`In this example, `is_allowed` and `has_permission` are functions. Rules: Rules are the core building blocks of Rego policies. They define the conditions under which a policy evaluates to true or false. Rules can have multiple clauses, and they can refer to other rules and functions.“`regopackage exampleallow input.method == “GET” is_authenticated(input.user)is_authenticated(user) data.users[user].active == true“`This policy grants access to GET requests from authenticated users.
Best Practices for Writing Readable and Maintainable Rego Policies
Writing clean and maintainable Rego policies is crucial for long-term success. Here are some best practices:* Use Meaningful Names: Choose descriptive names for packages, rules, variables, and functions. This makes it easier to understand the policy’s intent.* Comment Your Code: Add comments to explain complex logic or the purpose of specific rules. This is especially important when working in a team.* Keep Rules Concise: Break down complex rules into smaller, more manageable parts.
This improves readability and makes it easier to debug.* Use Functions for Reusable Logic: Encapsulate common logic into functions to avoid repetition and improve maintainability.* Organize Policies into Packages: Use package declarations to group related policies and prevent naming conflicts.* Test Your Policies: Write unit tests to verify that your policies behave as expected. OPA provides built-in testing capabilities.* Follow a Consistent Style: Adopt a consistent style guide for indentation, spacing, and naming conventions.
This improves readability and makes it easier to collaborate with others.* Modularize Policies: Break down large policies into smaller, more focused modules. This makes it easier to understand, maintain, and reuse policy components.* Document Your Policies: Create documentation that explains the purpose of your policies, how they work, and how to use them.* Leverage Data: Design your policies to use data effectively.
Externalize configuration and use data to drive policy decisions.By following these best practices, you can create Rego policies that are easy to understand, maintain, and evolve over time. This leads to more robust and reliable policy enforcement.
Integrating OPA with Different Systems
Integrating Open Policy Agent (OPA) into existing systems is crucial for realizing its policy enforcement capabilities. The approach varies depending on the system type and architecture. This section explores the integration methods, comparing different approaches, and providing a practical example of integrating OPA with an API gateway.
Methods for Integrating OPA with Different Application Types
OPA can be integrated with various application types, including APIs, microservices, and even monolithic applications. The primary goal is to intercept requests or events and apply the defined policies before allowing access or processing to continue.
- APIs: APIs are a common target for OPA integration. This typically involves intercepting API requests and evaluating them against OPA policies. Based on the policy evaluation result (allow or deny), the request is either forwarded to the backend service or rejected.
- Microservices: In a microservices architecture, OPA can be integrated into each microservice or deployed as a sidecar. This enables consistent policy enforcement across the entire system. The choice depends on factors like performance requirements and the level of centralized policy management desired.
- Monolithic Applications: For monolithic applications, OPA can be integrated directly into the application code or deployed as a proxy in front of the application. This approach requires careful planning to minimize performance impact and ensure seamless integration.
- Event-Driven Systems: OPA can also be used in event-driven systems to validate events before they are processed. This is useful for ensuring that events comply with specific rules or constraints.
Comparing and Contrasting Different Integration Approaches
Different integration approaches have varying trade-offs concerning performance, complexity, and management overhead. Understanding these differences is essential for selecting the best approach for a specific use case.
- Sidecar Proxies: In this approach, OPA runs as a sidecar container alongside the application. The application sends requests to the sidecar proxy, which then evaluates the request against OPA policies. If the policies allow the request, the proxy forwards it to the application.
- Advantages: This approach offers excellent isolation and reduces the need to modify the application code. It also simplifies policy management because policies can be updated independently of the application.
- Disadvantages: The sidecar approach can introduce some performance overhead due to the extra hop for each request. It also adds complexity to the deployment and management process.
- Direct Integration: In this approach, OPA is integrated directly into the application code, typically using a client library provided by OPA. The application calls the OPA client library to evaluate policies before processing a request.
- Advantages: Direct integration can offer better performance because there is no extra hop. It can also be simpler to set up in some cases.
- Disadvantages: This approach requires modifying the application code, which can be time-consuming and may require redeployment of the application whenever policies are updated. It can also make policy management more difficult because policies are tightly coupled with the application.
- API Gateways: API gateways can be configured to integrate with OPA. The gateway intercepts all API requests and evaluates them against OPA policies. This is a centralized approach to policy enforcement.
- Advantages: API gateways provide a centralized point for policy enforcement, simplifying policy management and ensuring consistency across all APIs.
- Disadvantages: API gateways can introduce a single point of failure. They may also require significant configuration to integrate with OPA.
Integrating OPA with a Specific API Gateway
Integrating OPA with an API gateway allows for centralized policy enforcement across all APIs managed by the gateway. This example uses a hypothetical API gateway, but the general principles apply to most gateways. This assumes that the API gateway supports an external authorization mechanism or has a plugin architecture.
- Choose the API Gateway: Select an API gateway that supports integration with external authorization services or plugins. Popular choices include Kong, Tyk, and Apigee. Ensure the gateway has well-documented integration capabilities.
- Install OPA and the OPA Client Library: Install OPA and the necessary client library on a machine accessible by the API gateway. The client library allows the gateway to communicate with OPA.
- Configure OPA Policies: Define the policies in Rego that you want to enforce. These policies should specify the conditions under which requests are allowed or denied.
For example, a policy might check the user’s role and the requested resource to determine if access should be granted.
- Configure the API Gateway to use OPA: Configure the API gateway to use the OPA client library. This typically involves specifying the OPA server’s address and the policies to evaluate. The gateway should be configured to intercept API requests and send them to OPA for policy evaluation.
- Implement the Integration Logic: The gateway will use the OPA client library to send requests to OPA for evaluation. The library will format the request as JSON, including relevant data like the user’s identity, the requested resource, and the HTTP method.
OPA will evaluate the request against the defined policies and return a decision (allow or deny).
- Handle the Policy Decisions: The API gateway must handle the policy decisions returned by OPA. If OPA returns “allow,” the gateway forwards the request to the backend service. If OPA returns “deny,” the gateway rejects the request, typically returning an appropriate HTTP error code (e.g., 403 Forbidden).
- Test the Integration: Thoroughly test the integration to ensure that policies are being enforced correctly. Create test cases that cover various scenarios, including different user roles, resource access, and HTTP methods. Verify that the API gateway behaves as expected in each scenario.
- Monitor and Maintain: Monitor the integration to ensure that it is performing as expected. Monitor the API gateway logs for errors and performance issues. Regularly review and update the OPA policies to reflect changes in the application’s security requirements.
Policy Enforcement Strategies
Open Policy Agent (OPA) provides various strategies to enforce policies effectively, ensuring that decisions are made efficiently and reliably across different systems. These strategies address performance, manageability, and the ability to handle complex policy scenarios. Understanding these methods is crucial for deploying OPA in production environments.
Decision Caching
Caching is a critical optimization technique for improving OPA’s performance, particularly when dealing with frequent policy evaluations. By caching the results of policy decisions, OPA can avoid re-evaluating the same policies for the same inputs repeatedly.
- Mechanism: OPA maintains a cache of policy decisions. When a request is received, OPA first checks the cache for a matching decision. If a cached result is found, it is returned immediately, bypassing the policy evaluation process.
- Configuration: Caching behavior is configurable, allowing for the specification of cache size, time-to-live (TTL), and other parameters. The optimal cache configuration depends on the specific workload and the frequency of policy updates.
- Impact: Caching significantly reduces latency and CPU usage, especially in scenarios with a high volume of requests and relatively stable policy rules. For instance, in a microservices architecture where each service frequently queries OPA for authorization, caching can prevent OPA from becoming a performance bottleneck.
- Example: Consider a system where users request access to resources. If the access control policy rarely changes, caching the “allow” or “deny” decisions for a specific user and resource combination can drastically improve response times.
Policy Updates
Managing policy updates is a core aspect of using OPA in a dynamic environment. OPA supports several methods for updating policies, enabling changes to be deployed quickly and safely.
- Methods:
- Local Files: Policies can be loaded from local files, which are updated manually or through automated scripts.
- HTTP Endpoints: Policies can be fetched from an HTTP endpoint, enabling centralized policy management and distribution.
- Policy Bundles: Policies can be packaged into bundles and distributed to OPA instances. This method is particularly useful for managing complex policy sets and ensuring consistency across deployments.
- Considerations: When updating policies, it is important to consider the impact on running systems. OPA supports features like graceful updates and policy versioning to minimize disruption.
- Example: Imagine a security policy that needs to be updated to address a new vulnerability. With OPA, the policy can be quickly modified and deployed to all instances, ensuring that the system is protected. Using versioning allows rolling back to a previous version if the update introduces unexpected issues.
Handling Policy Conflicts and Exceptions
Policy conflicts and exceptions are inevitable in complex systems. OPA provides mechanisms for managing these situations effectively.
- Conflict Resolution: When multiple policies apply to the same request and their decisions conflict (e.g., one policy allows access while another denies it), OPA uses a decision-making algorithm to resolve the conflict. The default behavior depends on the policy’s evaluation type (e.g., allow/deny, count).
- Exception Handling: Policies can be designed to handle exceptions. For example, a policy might include specific rules to override the default behavior in certain situations.
- Example: In a financial system, a policy might deny transactions over a certain amount. However, there might be an exception for authorized personnel. OPA allows you to define specific rules to handle these exceptions. For example, if a transaction is initiated by a user with the “admin” role, the policy could allow the transaction, overriding the default denial.
- Implementation: The best approach to handle conflicts and exceptions depends on the specific requirements of the system. Careful planning and policy design are crucial to ensure that the system behaves as expected.
Optimizing OPA Performance in Production Environments
Optimizing OPA’s performance is crucial for ensuring its scalability and reliability in production. Several strategies can be employed to achieve optimal performance.
- Caching: As mentioned earlier, caching is a fundamental optimization technique. Properly configuring the cache can significantly reduce latency and resource consumption.
- Query Optimization: Write efficient Rego policies. Avoid complex queries and loops that can degrade performance. Use built-in functions and operators effectively.
- Hardware Resources: Ensure that OPA has sufficient resources (CPU, memory) to handle the workload. Monitor resource usage and scale resources as needed.
- Monitoring: Implement monitoring to track OPA’s performance metrics, such as query latency, cache hit rates, and CPU usage. Use these metrics to identify performance bottlenecks and areas for improvement.
- Load Testing: Regularly perform load testing to simulate production traffic and identify performance limitations. This allows you to proactively address potential issues before they impact users.
- Example: A large e-commerce platform uses OPA for authorization. By implementing caching and optimizing Rego policies, the platform can handle thousands of authorization requests per second without significant latency.
Policy Bundles for Distributing and Managing Policies
Policy bundles provide a mechanism for packaging, distributing, and managing policies across multiple OPA instances. This approach simplifies policy management and ensures consistency.
- Mechanism: Policy bundles are essentially archives (e.g., ZIP files) that contain policy files, data files, and other metadata.
- Distribution: Bundles can be distributed via various methods, such as HTTP servers, cloud storage, or internal systems.
- Versioning: Policy bundles can be versioned, allowing for rollback and controlled updates.
- Verification: Bundles can be signed and verified to ensure integrity and authenticity.
- Benefits:
- Centralized Management: Simplifies policy updates and distribution.
- Consistency: Ensures that all OPA instances have the same policies.
- Auditing: Facilitates auditing and tracking of policy changes.
- Example: Consider a company that uses OPA to enforce security policies across multiple Kubernetes clusters. They can create a policy bundle containing all the necessary policies, distribute it to each cluster, and update the bundle as needed. This approach ensures that all clusters are consistently enforcing the same security rules.
Testing and Debugging OPA Policies
Testing and debugging are critical aspects of the policy development lifecycle. Thorough testing ensures that policies behave as expected and do not introduce unintended consequences. Effective debugging helps identify and resolve issues when policies fail to meet their intended goals. This section details various methods for testing and debugging Open Policy Agent (OPA) policies.
Testing Rego Policies
Testing Rego policies involves verifying their behavior against a set of inputs and expected outputs. This process ensures the policies correctly enforce the desired access control and governance rules. There are two primary approaches to testing Rego policies: unit testing and integration testing.
- Unit Testing: Unit tests focus on testing individual Rego rules or functions in isolation. This involves providing specific inputs to a rule and verifying that the output matches the expected outcome. Unit tests are typically smaller and faster to execute, allowing for rapid feedback during policy development.
- Integration Testing: Integration tests verify the interaction between multiple rules and components within a policy. This approach tests how different parts of a policy work together to enforce the overall policy logic. Integration tests often use more complex input data and simulate real-world scenarios.
Using the OPA CLI for Testing and Debugging
The OPA Command Line Interface (CLI) provides powerful tools for testing and debugging Rego policies. The CLI allows developers to evaluate policies against data and input, inspect the evaluation process, and identify potential issues.
- Testing with `opa test`: The `opa test` command runs tests defined in `.rego` files. These test files typically contain input data, expected results, and assertions to validate policy behavior. The CLI reports the results of each test, indicating whether the policy passed or failed.
For example, consider a policy file `policy.rego`:
“`rego
package exampleallow
input.method == “GET”
input.path == “/data”“`
And a test file `policy_test.rego`:
“`rego
package exampletest_allow_get_data
input :=
“method”: “GET”,
“path”: “/data”,allow == true
test_deny_post_data
input :=
“method”: “POST”,
“path”: “/data”,allow == false
“`
Running `opa test policy.rego policy_test.rego` would execute the tests and report the results.
- Evaluating Policies with `opa eval`: The `opa eval` command allows developers to evaluate policies against specific input and data. This is useful for manually testing policies and inspecting their behavior. The command returns the output of the policy evaluation, including the values of variables and the results of rule evaluations.
For example, to evaluate the `allow` rule from the previous example with a specific input, you could use:
“`bash
opa eval –data data.json –input input.json “data.example.allow”
“`Where `data.json` contains the policy data and `input.json` contains the input data.
- Inspecting the Evaluation Process: The OPA CLI can provide detailed information about the evaluation process, including the values of variables at different stages and the rules that were evaluated. This information is invaluable for debugging complex policies. The `–explain` flag can be used with `opa eval` to show the evaluation steps.
Debugging Techniques within OPA
OPA offers several debugging techniques to assist in identifying and resolving policy issues. These techniques help understand why a policy is behaving unexpectedly and pinpoint the root cause of the problem.
- Using the `–explain` flag: The `–explain` flag, when used with `opa eval`, provides a detailed explanation of the evaluation process. It shows the steps taken by OPA, including the rules that were evaluated, the values of variables, and the reasons for decisions. This is particularly helpful for understanding complex policy logic.
- Logging: OPA supports logging, which allows developers to insert log statements into their Rego policies. These log statements can be used to print the values of variables, track the execution flow, and monitor the behavior of the policy. Logging can be enabled by using the `trace` function. For instance:
“`rego
package exampleallow
trace(“Input:”, input)
input.method == “GET”
trace(“Path:”, input.path)
input.path == “/data”“`
This will print the input and path values during policy evaluation.
- Using the OPA Playground: The OPA Playground is a web-based tool that allows developers to experiment with Rego policies, input data, and queries. The playground provides real-time feedback on policy evaluation, including the output, the evaluation trace, and any errors. This interactive environment is an excellent tool for learning and debugging policies.
Testing Scenarios and Expected Outcomes
The following table illustrates various testing scenarios and the expected outcomes for a hypothetical policy that governs access to resources based on user roles and resource types.
| Scenario | Input Data | Policy Data | Expected Outcome | Explanation |
|---|---|---|---|---|
| User with admin role accessing a document | "user": "role": "admin" , "resource": "type": "document" | "roles": "admin": ["document", "image"] | Allow access | The policy allows admins to access all document types. |
| User with editor role accessing an image | "user": "role": "editor" , "resource": "type": "image" | "roles": "editor": ["image"] | Allow access | The policy allows editors to access images. |
| User with viewer role accessing a document | "user": "role": "viewer" , "resource": "type": "document" | "roles": "viewer": ["image"] | Deny access | The policy denies viewers access to documents, as the viewer role is only permitted for images. |
| User with admin role accessing an unknown resource type | "user": "role": "admin" , "resource": "type": "unknown" | "roles": "admin": ["document", "image"] | Deny access | The policy denies access to resources of an unknown type, even for admins. |
Real-World Use Cases of OPA
Open Policy Agent (OPA) has gained significant traction across various industries, offering a powerful and flexible solution for policy enforcement. Its ability to centralize and manage policies independently from the applications they govern makes it a valuable tool for organizations seeking to improve security, compliance, and operational efficiency. This section explores diverse real-world applications of OPA, providing concrete examples and highlighting the benefits achieved by adopting this technology.
Use Cases in Cloud Native Environments
Cloud native environments, characterized by microservices, containerization, and dynamic infrastructure, present unique policy challenges. OPA addresses these by providing consistent policy enforcement across a rapidly changing landscape.
- Kubernetes Admission Control: OPA is frequently used as a Kubernetes admission controller. It intercepts requests to the Kubernetes API server and evaluates them against defined policies. This allows organizations to enforce best practices for resource allocation, security configurations (e.g., image scanning, pod security policies), and compliance requirements. For instance, OPA can be configured to reject pods that do not specify resource requests and limits, preventing resource exhaustion.
- Service Mesh Policy Enforcement: In service mesh architectures like Istio and Linkerd, OPA enforces policies related to traffic management, authentication, and authorization. Policies can control which services can communicate with each other, enforce TLS encryption, and implement rate limiting. This helps secure inter-service communication and control access to sensitive data.
- Infrastructure-as-Code (IaC) Policy Validation: OPA can be integrated into CI/CD pipelines to validate infrastructure configurations defined in tools like Terraform or CloudFormation. This ensures that infrastructure deployments comply with organizational policies before they are provisioned. For example, policies can check for the use of approved instance types, the proper configuration of security groups, and the adherence to naming conventions.
Use Cases in API Gateways
API gateways serve as the entry point for API traffic and are critical for security and access control. OPA provides a powerful means to enforce policies at this crucial point.
- API Access Control: OPA can be integrated into API gateways to enforce access control policies. Policies can define which users or applications are authorized to access specific APIs, based on factors such as user roles, authentication methods, and IP addresses. This prevents unauthorized access and protects sensitive data.
- Rate Limiting and Throttling: OPA can be used to implement rate limiting and throttling policies to protect APIs from abuse and ensure fair usage. Policies can limit the number of requests a user or application can make within a specific time period.
- Request and Response Validation: OPA can validate API requests and responses against defined schemas and business rules. This ensures that data is in the correct format and that responses comply with expected formats, improving data quality and security.
Use Cases in Security and Compliance
Organizations across all industries must adhere to various security and compliance regulations. OPA streamlines the enforcement of these requirements.
- Compliance with Regulations: OPA can be used to automate compliance with regulations such as GDPR, HIPAA, and PCI DSS. Policies can be written to enforce data privacy, security controls, and access restrictions, helping organizations meet their compliance obligations.
- Security Auditing and Reporting: OPA provides audit trails and logging capabilities, allowing organizations to track policy decisions and identify potential security vulnerabilities. This information can be used for security audits and reporting.
- Zero Trust Security: OPA is a key component of zero-trust security architectures. It helps enforce policies based on identity, device posture, and other contextual factors, ensuring that access is granted only to authorized users and devices.
Comparative Table of Use Cases
Here’s a table summarizing different use cases, their associated challenges, and the solutions provided by OPA:
| Use Case | Challenge | Solution with OPA | Benefits Realized |
|---|---|---|---|
| Kubernetes Admission Control | Enforcing consistent security and operational policies across Kubernetes clusters. | Using OPA as an admission controller to validate pod configurations, resource requests, and security settings. | Improved security posture, reduced operational overhead, and consistent policy enforcement. |
| Service Mesh Policy Enforcement | Securing inter-service communication and controlling access within a service mesh. | Integrating OPA with service meshes like Istio to enforce traffic management, authentication, and authorization policies. | Enhanced security, simplified access control, and improved observability of service interactions. |
| API Access Control | Protecting APIs from unauthorized access and enforcing access control policies. | Integrating OPA into API gateways to implement role-based access control, rate limiting, and authentication policies. | Improved API security, controlled access to sensitive data, and protection against abuse. |
| IaC Policy Validation | Ensuring infrastructure deployments comply with organizational policies before provisioning. | Integrating OPA into CI/CD pipelines to validate Terraform, CloudFormation, or other IaC configurations. | Reduced risk of misconfigurations, improved compliance, and faster, more reliable deployments. |
Advanced OPA Features

Open Policy Agent (OPA) offers a rich set of advanced features that significantly enhance its capabilities beyond basic policy enforcement. These features allow for more sophisticated policy definitions, integrations with external data sources, and the implementation of policy-as-code practices. This section delves into these advanced aspects, providing examples and demonstrating their practical applications.
Data Filtering and External Data Integration
OPA’s ability to filter data and integrate with external sources is crucial for building context-aware policies. This functionality allows policies to consider information beyond the immediate request, enabling more informed and nuanced decision-making.To filter data, OPA uses its Rego query language to select and transform data from various sources. This data can then be used within policy rules to determine access, authorization, or any other policy decision.OPA can integrate with a wide variety of external data sources, including:
- APIs: Fetching data from REST APIs to incorporate real-time information.
- Databases: Querying databases (e.g., PostgreSQL, MySQL) for persistent data.
- Files: Reading data from local or remote files (e.g., JSON, YAML).
- Key-Value Stores: Integrating with key-value stores (e.g., etcd, Consul) for configuration data.
Integrating external data is typically achieved using the `http.get` or `data.external` built-in functions in Rego. For instance, to fetch user roles from an API:“`regopackage authzimport future.sdefault allow = false# Example: Allow access if the user has the “admin” role.allow user_role := http.get(“https://api.example.com/users/alice/role”).result.role user_role == “admin”“`In this example, the policy retrieves the user’s role from an external API and allows access if the role is “admin”.
This demonstrates how OPA leverages external data to make policy decisions.
Policy as Code
OPA is designed to support policy-as-code principles, treating policies as code that can be version-controlled, tested, and deployed in an automated manner. This approach improves policy management, reduces errors, and increases agility.Implementing policy as code involves several key practices:
- Version Control: Storing policies in a version control system (e.g., Git) to track changes and enable collaboration.
- Testing: Writing unit tests to verify policy behavior and ensure correctness.
- Automation: Automating the deployment of policies to OPA instances.
- Modularity: Designing policies in a modular way, breaking down complex logic into reusable components.
For example, a CI/CD pipeline can be set up to automatically test and deploy OPA policies whenever changes are pushed to the repository. This process ensures that policies are consistently enforced and updated.
Advanced Policy Design Patterns
Several advanced policy design patterns can be implemented using OPA to address complex policy requirements. These patterns help in writing more maintainable and effective policies.
Example: Attribute-Based Access Control (ABAC) ABAC uses attributes of the subject, object, action, and environment to determine access. OPA can be used to implement ABAC by defining policies that evaluate these attributes against specific rules. For example:
“`rego package authz default allow = false allow # Subject attributes user := input.user # Object attributes resource := input.resource # Action action := input.action # Environment attributes (e.g., time of day) time_of_day := time.now_ns() / 1000000000 # Policy rules user == “alice” resource == “sensitive_data” action == “read” time_of_day > 83600 # Allow read access after 8 AM
time_of_day < 17- 3600 # and before 5 PM ```
This policy grants “alice” read access to “sensitive_data” between 8 AM and 5 PM, demonstrating how ABAC can be implemented using OPA.
Monitoring and Logging OPA
Effective monitoring and logging are crucial for maintaining the health, performance, and security of any system, and Open Policy Agent (OPA) is no exception. By implementing robust monitoring and logging strategies, you can gain valuable insights into OPA’s behavior, identify potential issues, and ensure that your policies are being enforced as intended. This section will delve into the specifics of monitoring and logging OPA, covering performance monitoring, policy evaluation logging, integration with monitoring systems, and the use of metrics and dashboards.
Monitoring OPA Performance
Monitoring OPA’s performance involves tracking key metrics that provide insights into its efficiency and responsiveness. These metrics help identify bottlenecks, optimize resource allocation, and ensure OPA is meeting its performance goals.To effectively monitor OPA performance, consider the following key aspects:
- Request Latency: This metric measures the time it takes for OPA to evaluate a policy and return a decision. High latency can indicate performance issues, especially under heavy load. Monitor the average, 95th percentile, and 99th percentile latencies to identify potential slowdowns.
- Query Rate (QPS): The number of policy evaluation requests processed per second. Monitoring QPS helps assess OPA’s ability to handle the incoming workload. A sudden drop in QPS might indicate a problem.
- Evaluation Time: The time spent evaluating individual policies. Slow policy evaluations can negatively impact overall latency. Analyze the time spent on each policy and identify the most time-consuming ones for optimization.
- Cache Hit Ratio: OPA uses a built-in cache to store policy decisions. A high cache hit ratio indicates that OPA is efficiently reusing cached results, improving performance. A low hit ratio suggests that the cache might be too small or that the policies are not cache-friendly.
- Resource Consumption (CPU, Memory): Track CPU and memory usage to ensure OPA has sufficient resources to operate effectively. High resource consumption can indicate inefficient policies or a need for more resources.
- Errors and Failures: Monitor the number of errors and failures that occur during policy evaluations. This includes errors in the policy itself, as well as issues with the data sources used by OPA.
Logging Policy Evaluations and Audit Trails
Logging policy evaluations is essential for understanding how OPA is making decisions, providing an audit trail for compliance purposes, and troubleshooting policy issues.To implement effective policy evaluation logging, consider these approaches:
- Logging Policy Decisions: Log the results of each policy evaluation, including the input data, the policy being evaluated, and the decision (allow, deny, or other).
- Logging Evaluation Details: Include detailed information about the evaluation process, such as the rules that were evaluated, the data that was accessed, and any errors that occurred.
- Structured Logging: Use a structured logging format (e.g., JSON) to make it easier to parse and analyze the logs. This format allows for easier querying and analysis of log data.
- Contextual Information: Include contextual information in the logs, such as the user ID, the request ID, and the service that initiated the policy evaluation.
- Sensitive Data Handling: Be mindful of sensitive data. Avoid logging sensitive information directly. Instead, consider masking or redacting sensitive data or using techniques like data anonymization to protect privacy.
- Log Rotation: Implement log rotation to manage the size of the log files and prevent them from consuming excessive disk space.
Integrating OPA with Monitoring and Logging Systems
Integrating OPA with existing monitoring and logging systems allows you to centralize and correlate OPA-related data with other system metrics and logs. This approach offers a comprehensive view of your system’s behavior.Consider the following strategies for integrating OPA with your monitoring and logging systems:
- Log Forwarding: Configure OPA to forward its logs to a centralized logging system, such as Elasticsearch, Splunk, or the cloud provider’s logging service (e.g., AWS CloudWatch, Google Cloud Logging, Azure Monitor).
- Metrics Export: Expose OPA metrics in a format that can be scraped by a monitoring system like Prometheus. Prometheus can then collect and store these metrics for analysis and visualization.
- API Integration: Use OPA’s API to retrieve policy evaluation results and other data and then integrate this data with your monitoring and logging systems.
- Custom Loggers: Implement custom loggers within OPA to format and send log data to your preferred logging systems.
- Sidecar Containers: Deploy OPA as a sidecar container alongside your applications. The sidecar can then collect logs and metrics from OPA and forward them to your monitoring and logging infrastructure.
Metrics and Dashboards for OPA Monitoring
Using metrics and dashboards is a visual and efficient way to monitor OPA’s performance and policy decisions. Dashboards can provide real-time insights and historical trends, allowing you to proactively identify and address issues.Here are some metrics and dashboard elements to consider:
- Request Rate (QPS): A line chart showing the number of policy evaluation requests per second.
- Request Latency: Line charts showing the average, 95th percentile, and 99th percentile request latencies.
- Cache Hit Ratio: A gauge or a line chart displaying the cache hit ratio.
- Evaluation Time: A histogram or distribution chart showing the distribution of policy evaluation times.
- Error Rate: A line chart showing the rate of errors during policy evaluations.
- Resource Usage (CPU, Memory): Line charts showing CPU and memory usage.
- Policy Decision Breakdown: A pie chart or bar chart showing the distribution of policy decisions (allow, deny, etc.).
- Top Policies by Evaluation Time: A table or bar chart listing the policies that are taking the longest to evaluate.
- Dashboard Tools: Use tools like Grafana, Kibana, or the monitoring dashboards provided by your cloud provider to create and visualize your OPA metrics.
Closure
In conclusion, mastering Open Policy Agent unlocks a new dimension of control and efficiency in policy enforcement. From its elegant architecture to its flexible integration capabilities, OPA offers a robust solution for modern software challenges. By embracing the principles and techniques Artikeld in this guide, you can confidently navigate the complexities of policy management, securing your systems and ensuring compliance with ease.
The journey with OPA is a continuous learning process, and the benefits it provides are substantial, making it an indispensable asset for any organization striving for robust security and streamlined operations.
Question Bank
What is the primary advantage of using OPA for policy enforcement?
OPA provides a centralized and unified approach to policy management, enabling consistent enforcement across different systems and services, thereby reducing complexity and improving security.
How does OPA differ from traditional access control mechanisms?
OPA moves beyond simple access control lists by allowing for more sophisticated policy definitions, incorporating contextual data and dynamic rules to make decisions based on various factors.
Is OPA suitable for both cloud-native and on-premise environments?
Yes, OPA is designed to be highly adaptable and can be implemented in both cloud-native and on-premise environments, providing consistent policy enforcement regardless of the infrastructure.
What is the learning curve for Rego, the OPA policy language?
Rego is designed to be relatively easy to learn, with a syntax similar to declarative languages. Basic policies can be written quickly, and more complex policies can be developed with practice and experience.
How can I monitor the performance of OPA in a production environment?
OPA provides metrics and logging capabilities that can be integrated with monitoring systems to track performance, policy decisions, and audit trails, allowing for proactive identification of issues and optimization opportunities.


