Embark on a journey into the realm of automated software development with Jenkins, a powerhouse for Continuous Integration (CI). This guide will illuminate the path to efficient, reliable, and streamlined software delivery. We’ll delve into the core concepts of CI, explore Jenkins’ history, and uncover its pivotal role in the modern software development lifecycle. Prepare to transform your development workflow and experience the benefits of automated builds, tests, and deployments.
This guide provides a structured approach, starting with the fundamentals of Jenkins and CI, then progressing through installation, configuration, job creation, and advanced techniques. We’ll cover everything from setting up your Jenkins environment to implementing sophisticated pipelines, integrating with version control systems, and leveraging advanced features like Docker and Kubernetes. Along the way, we’ll provide practical examples, troubleshooting tips, and best practices to ensure a smooth and successful implementation of Jenkins in your projects.
Introduction to Jenkins and Continuous Integration
Continuous Integration (CI) has become a cornerstone of modern software development, streamlining the build, test, and release processes. Jenkins, an open-source automation server, plays a pivotal role in implementing CI practices. This section explores the core concepts of CI, its advantages, and the significance of Jenkins in the software development lifecycle.
Core Concepts of Continuous Integration
Continuous Integration is a development practice where developers frequently merge their code changes into a central repository. After each merge, an automated build and test process is triggered. The primary goal is to identify and address integration issues early and frequently, leading to faster feedback loops and more stable software.
- Frequent Integration: Developers integrate their code changes into a shared repository multiple times a day.
- Automated Builds: Each integration triggers an automated build process, compiling the code and creating an executable.
- Automated Testing: After the build, automated tests (unit, integration, etc.) are executed to verify the code’s functionality.
- Feedback and Remediation: If the build or tests fail, developers receive immediate feedback, allowing them to quickly identify and fix the problem.
The advantages of Continuous Integration are significant.
Benefits of Continuous Integration
Implementing CI offers numerous advantages for software development teams. These benefits contribute to increased efficiency, improved software quality, and faster delivery cycles.
- Reduced Integration Risks: Integrating code frequently minimizes the chances of major integration problems later in the development cycle.
- Early Bug Detection: Automated testing helps identify bugs early, when they are easier and less expensive to fix.
- Faster Feedback Loops: Developers receive rapid feedback on their code changes, enabling them to address issues quickly.
- Improved Software Quality: CI practices contribute to higher software quality through rigorous testing and continuous monitoring.
- Increased Team Productivity: Automated processes free up developers from manual tasks, allowing them to focus on writing code.
- Faster Release Cycles: By automating the build, test, and release processes, CI enables faster and more frequent software releases.
History and Rise of Jenkins
Jenkins emerged as a fork of the Hudson project in 2011, following a dispute within the Hudson community. It quickly gained popularity due to its flexibility, extensibility, and open-source nature. Its adoption has grown exponentially.
- Origins in Hudson: Jenkins originated as a fork of the Hudson project, an open-source continuous integration tool.
- Open Source and Community Driven: Jenkins is open source, fostering a vibrant community that contributes to its development and provides support.
- Extensibility through Plugins: Jenkins’s plugin architecture allows users to extend its functionality to support a wide range of tools and technologies.
- Wide Adoption: Jenkins has become one of the most widely used CI/CD tools, adopted by organizations of all sizes.
Role of Jenkins in the Software Development Lifecycle
Jenkins serves as a central hub for automating the build, test, and deployment processes in the software development lifecycle. It orchestrates the various stages of the CI/CD pipeline.
- Automated Builds: Jenkins automates the process of building software from source code.
- Automated Testing: Jenkins integrates with various testing frameworks to execute automated tests.
- Deployment Automation: Jenkins can automate the deployment of software to various environments.
- Continuous Monitoring: Jenkins provides dashboards and reports to monitor the CI/CD pipeline’s performance.
- Integration with Version Control Systems: Jenkins integrates seamlessly with version control systems like Git to trigger builds upon code changes.
- Orchestration of CI/CD Pipelines: Jenkins allows teams to define and manage complex CI/CD pipelines.
Installing and Setting up Jenkins
Setting up Jenkins is a crucial step in establishing your continuous integration and continuous delivery (CI/CD) pipeline. This section will guide you through the installation process and initial configuration, ensuring a smooth start to your CI/CD journey. We will cover system requirements, installation steps for different operating systems, and accessing the Jenkins web interface.
System Requirements for Jenkins Installation
Before installing Jenkins, it is important to ensure your system meets the minimum requirements for optimal performance. These requirements vary based on the expected load and usage of Jenkins.
- Hardware: The recommended hardware specifications depend on the size and complexity of your projects.
- CPU: A multi-core processor is recommended to handle concurrent builds.
- RAM: Minimum 2GB of RAM is recommended, but 4GB or more is preferable, especially for complex projects with multiple plugins.
- Storage: Sufficient disk space is required for storing build artifacts, logs, and Jenkins configuration data. Consider at least 50GB for a starting point, and scale up as needed.
- Software: Jenkins requires a Java Runtime Environment (JRE) or Java Development Kit (JDK) to run.
- Java: Jenkins officially supports Java 8, Java 11, and Java 17. Ensure a compatible version is installed.
- Operating System: Jenkins can be installed on various operating systems, including Linux (e.g., Ubuntu, CentOS, Debian), Windows, and macOS.
- Network: Access to the internet is needed for downloading plugins and updates. Ensure proper network configuration.
Installing Jenkins on Different Operating Systems
The installation process for Jenkins varies slightly depending on the operating system. Here’s a guide for the most common platforms.
- Linux (Debian/Ubuntu): The installation process typically involves using the package manager.
- Step 1: Add the Jenkins repository key to your system. This ensures the authenticity of the Jenkins packages.
- Step 2: Add the Jenkins repository to your sources list. This tells the package manager where to find the Jenkins packages.
- Step 3: Update the package list to include the Jenkins repository.
- Step 4: Install Jenkins using the package manager.
- Step 5: Start the Jenkins service.
- Example:
wget -q -O - https://pkg.jenkins.io/debian/jenkins.io.key | sudo apt-key add -sudo sh -c 'echo deb https://pkg.jenkins.io/debian-stable binary/ > /etc/apt/sources.list.d/jenkins.list'sudo apt-get updatesudo apt-get install jenkinssudo systemctl start jenkins
- Linux (CentOS/RHEL): The installation process is similar to Debian/Ubuntu, using the appropriate package manager.
- Step 1: Add the Jenkins repository configuration file.
- Step 2: Import the Jenkins GPG key.
- Step 3: Install Jenkins using the package manager.
- Step 4: Start the Jenkins service.
- Example:
sudo wget -O /etc/yum.repos.d/jenkins.repo https://pkg.jenkins.io/redhat-stable/jenkins.reposudo rpm --import https://pkg.jenkins.io/redhat-stable/jenkins.io.keysudo yum install jenkinssudo systemctl start jenkins
- Windows: Jenkins can be installed as a standalone application or as a service.
- Step 1: Download the Jenkins installer from the official website.
- Step 2: Run the installer and follow the on-screen instructions.
- Step 3: The installer will prompt for the Java installation path, if it cannot automatically detect it.
- Step 4: The installer will automatically set up Jenkins as a Windows service.
- macOS: Jenkins can be installed using Homebrew or by downloading the .war file and running it.
- Using Homebrew:
- Step 1: Install Homebrew if you don’t already have it.
- Step 2: Install Jenkins using Homebrew.
- Step 3: Start Jenkins using Homebrew services.
- Example:
brew install jenkinsbrew services start jenkins
- Using .war file:
- Step 1: Download the Jenkins .war file.
- Step 2: Open the terminal and navigate to the directory where you downloaded the .war file.
- Step 3: Run the command to start Jenkins using java.
- Example:
java -jar jenkins.war
- Using Homebrew:
Accessing the Jenkins Web Interface and Initial Configuration
After installation, accessing and configuring Jenkins is a straightforward process.
- Accessing the Web Interface:
- Open a web browser and navigate to the Jenkins URL, which is typically
http://localhost:8080(or the port you configured). - You will be prompted to unlock Jenkins using an initial administrator password.
- Retrieve the initial password from the location specified during installation (e.g., a file on the server).
- Open a web browser and navigate to the Jenkins URL, which is typically
- Initial Configuration:
- After unlocking Jenkins, you will be prompted to install suggested plugins or select specific plugins. The “Install suggested plugins” option is generally a good starting point.
- Create the first administrator user or use the default admin user with a new password.
- Configure the Jenkins URL (usually, this is automatically detected).
- Jenkins is now ready to use.
Comparison of Jenkins Installation Methods
Different installation methods offer varying advantages and disadvantages. This table summarizes the pros and cons of the most common approaches.
| Installation Method | Pros | Cons |
|---|---|---|
| Package Manager (e.g., apt, yum, brew) |
|
|
| Standalone (.war file) |
|
|
| Docker |
|
|
Jenkins User Interface and Configuration
The Jenkins user interface is the primary point of interaction for managing and monitoring your continuous integration and continuous delivery (CI/CD) pipelines. Understanding the layout and configuration options is crucial for effectively utilizing Jenkins. This section details the key components of the Jenkins UI and explains how to customize it for your specific needs.
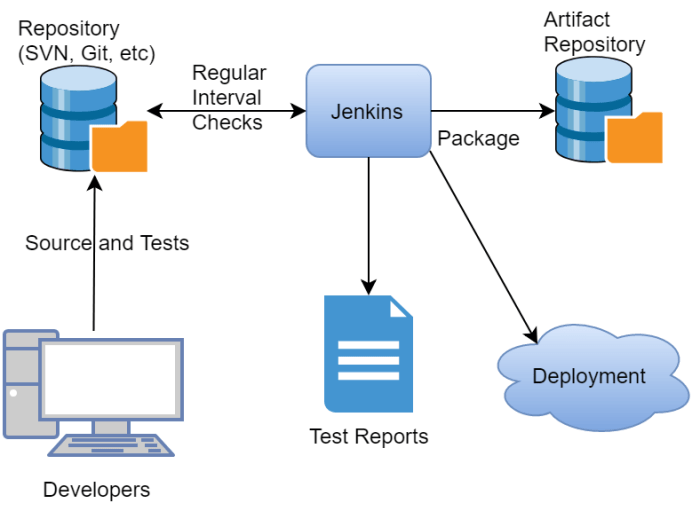
Jenkins Dashboard Sections
The Jenkins dashboard provides a central overview of your projects and system status. Several key sections contribute to its functionality:* Build Queue: This section displays builds that are waiting to be executed. Builds are added to the queue when a trigger condition is met, and a Jenkins agent is available to execute the build. The queue helps visualize the pending tasks and their order of execution.
Build Executor Status
This section shows the status of the executors (workers) that are currently running builds. It indicates the number of executors available, the jobs they are running, and their progress. This section helps monitor the load on your Jenkins infrastructure and identify potential bottlenecks.
Job Views
The dashboard allows for the creation of custom views. These views can filter and organize jobs based on criteria such as project, status (success, failure, unstable), or user-defined tags. Views enable users to focus on relevant information and improve navigation.
Job Lists
The main area of the dashboard lists all the jobs (pipelines or freestyle projects) configured in Jenkins. Each job entry displays information such as the job name, status (e.g., success, failure, in progress), last build result, and a link to the job’s detailed view.
System Messages
This section displays important system-level messages, warnings, and notifications. These messages can relate to plugin updates, security vulnerabilities, or system configuration issues. Monitoring this section is crucial for maintaining the health of your Jenkins instance.
Creating and Managing Jenkins Users and Roles
Effective user management is essential for controlling access to your Jenkins instance and ensuring security. Jenkins provides mechanisms for creating users and assigning them specific roles with defined permissions.* User Creation: Users can be created directly within Jenkins or integrated with external authentication providers such as LDAP or Active Directory. To create a user within Jenkins, navigate to “Manage Jenkins” -> “Manage Users” -> “Create User.” You will need to provide a username, password, full name, and email address.
Role-Based Access Control (RBAC)
Jenkins uses RBAC to define permissions for users and groups. This allows administrators to control which users can perform specific actions, such as building jobs, configuring the system, or viewing logs.
Role Assignment
Once users and roles are created, you can assign roles to users or groups. This can be done through the “Manage Jenkins” -> “Configure Global Security” section. Here, you can select a security realm (e.g., Jenkins’ own user database, LDAP) and define authorization strategies. Common authorization strategies include “Matrix-based security” or “Project-based Matrix Authorization Strategy,” which allows granular control over job-level permissions.
Example
Suppose you want to create a role called “Developers” and grant it permission to build and view all jobs. You can create the “Developers” role and assign it the necessary permissions through the RBAC configuration. Then, you assign individual users or groups to the “Developers” role.
Configuring Global Settings: Plugins and Security
Global settings configure the overall behavior of your Jenkins instance. These settings include plugin management, security configurations, and system-wide preferences.* Plugin Management: Plugins extend Jenkins’ functionality. You can install, update, and uninstall plugins through the “Manage Jenkins” -> “Manage Plugins” section. The “Available” tab lists plugins that can be installed. The “Installed” tab shows currently installed plugins, and the “Updates” tab shows plugins that have updates available.
Security Configuration
Security settings are crucial for protecting your Jenkins instance. You can configure security realms, authorization strategies, and global security settings through “Manage Jenkins” -> “Configure Global Security.”
It is highly recommended to enable security and configure appropriate authentication and authorization strategies. Failing to do so can leave your Jenkins instance vulnerable to unauthorized access and malicious attacks.
System Configuration
Global settings such as the Jenkins URL, email configuration, and build executors are configured through “Manage Jenkins” -> “Configure System.” This is where you set up the base URL for your Jenkins instance, configure email notifications, and manage the number of executors available to run builds.
Essential Plugins and Functionalities
Plugins greatly expand Jenkins’ capabilities. Here is a list of essential plugins and their functionalities:* Git Plugin: Integrates Jenkins with Git repositories, enabling the pulling of code and triggering builds on code changes. This is a fundamental plugin for most CI/CD pipelines.
Maven Integration Plugin
Provides support for building Maven projects, including dependency management and artifact publishing.
Pipeline (formerly Workflow) Plugin
Enables the creation of pipelines as code using a Groovy-based DSL. This allows for defining complex build and deployment processes in a declarative and version-controlled manner.
Email Extension Plugin
Extends the default email notification functionality, allowing for more customizable email notifications, including conditional notifications and detailed build reports.
SSH Agent Plugin
Enables the use of SSH keys for secure access to remote servers during build and deployment processes.
Publish Over SSH Plugin
Allows publishing artifacts and executing commands on remote servers over SSH. This is useful for deploying applications to production or staging environments.
SonarQube Scanner Plugin
Integrates Jenkins with SonarQube for code quality analysis, providing reports on code quality metrics and potential issues.
Docker Plugin
Integrates Jenkins with Docker, allowing for building, testing, and deploying applications in Docker containers. This is useful for containerizing applications and creating consistent build environments.
Creating and Configuring a Jenkins Job
Setting up a Jenkins job is the core activity in automating your software development lifecycle. This section guides you through the process of creating and configuring different job types, integrating source code management, and setting up build triggers. This ensures that your builds are automatically triggered and your code is continuously integrated.
Creating Different Types of Jenkins Jobs
Jenkins offers several job types, each designed to cater to different build and deployment scenarios. The most common types are Freestyle projects and Pipelines. Understanding the differences between them is crucial for choosing the right job type for your needs.
- Freestyle Project: Freestyle projects are the most basic and flexible job type. They are suitable for simple build processes, providing a user-friendly interface for configuring various build steps. They are ideal for straightforward tasks, such as compiling code, running tests, and deploying applications.
- Pipeline: Pipelines, also known as Jenkinsfiles, offer a more advanced and structured approach to continuous integration and continuous delivery (CI/CD). They allow you to define your entire build process as code, using a Groovy-based Domain-Specific Language (DSL). Pipelines support more complex workflows, including branching, parallel execution, and advanced deployment strategies. They are better suited for projects that require sophisticated automation and version control of the build process.
Configuring Source Code Management (SCM) Settings
Integrating your source code repository with Jenkins is a fundamental step in continuous integration. This enables Jenkins to automatically fetch the latest code changes and trigger builds whenever changes are pushed to the repository.
- Selecting SCM: In the job configuration, you will find the “Source Code Management” section. Here, you select the type of source code repository you are using, such as Git or Subversion.
- Configuring Git: If you choose Git, you’ll need to provide the repository URL and the branch to build. You may also need to specify credentials if the repository requires authentication. You can select credentials from a dropdown menu if you have already configured them in Jenkins’ global settings.
- Configuring Subversion: For Subversion, you’ll provide the repository URL, the module directory, and, if required, credentials. Similar to Git, you can select credentials from the available options.
- Polling for Changes: After configuring the SCM settings, you can configure Jenkins to poll the repository periodically for changes. This is done by setting a schedule in the “Build Triggers” section, using a cron-like syntax. For example, setting the schedule to “*
- ” will cause Jenkins to check for changes every minute.
Setting Up Build Triggers
Build triggers determine when a Jenkins job will be executed. Jenkins supports various triggers, allowing you to automate the build process based on different events.
- Polling SCM: This trigger instructs Jenkins to periodically check the source code repository for changes. If changes are detected, a new build is triggered. This is useful for ensuring that builds are triggered regularly.
- Webhooks: Webhooks provide a more immediate trigger mechanism. When a change is pushed to the repository, the repository sends a notification (webhook) to Jenkins, triggering a build immediately. This is more efficient than polling.
- Other Triggers: Other triggers include building after other projects are built, or periodically.
Step-by-Step Procedure for Creating a Basic Freestyle Project
Here’s a step-by-step guide to creating a basic Freestyle project. This example will demonstrate how to create a simple job that builds a “Hello World” application.
- Access Jenkins Dashboard: Open your web browser and navigate to your Jenkins instance (e.g., `http://localhost:8080/`). Log in with your credentials.
- Create a New Item: On the Jenkins dashboard, click “Create a job” or “New Item.”
- Enter Job Name: Enter a name for your job (e.g., “HelloWorldProject”) in the “Enter an item name” field.
- Select Freestyle Project: Choose “Freestyle project” as the job type and click “OK.”
- Configure General Settings: In the job configuration, you can provide a description for the project and configure other general settings.
- Configure Source Code Management (SCM): In the “Source Code Management” section, select “None” if you are not integrating with a repository for this simple example. If you were integrating with a repository, you would select the appropriate SCM system (e.g., Git) and provide the repository URL.
- Configure Build Triggers: For this example, we will use no build triggers. You can add triggers like “Poll SCM” to poll the repository for changes or set up webhooks.
- Configure Build Steps: In the “Build” section, click “Add build step” and select “Execute shell.” This will allow you to execute shell commands.
- Enter Shell Commands: In the “Command” field, enter the following command to print “Hello, World!” to the console:
echo "Hello, World!" - Save the Job: Click “Save” to save the job configuration.
- Build the Job: On the job’s page, click “Build Now” to trigger a build.
- View Build Output: After the build completes, click on the build number (e.g., #1) to view the build details. Click “Console Output” to see the output of the build, which should include “Hello, World!”.
This procedure provides a foundation for creating more complex jobs. You can add more build steps, integrate with source code repositories, and configure various build triggers to automate your software development processes effectively.
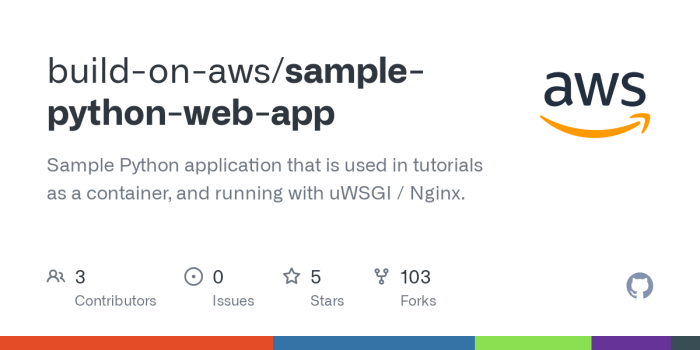
Building and Testing Code with Jenkins
After successfully setting up your Jenkins instance and creating a job, the next crucial step is configuring the build process. This involves defining the steps Jenkins will execute to compile, test, and analyze your codebase. Proper configuration ensures that every code change is thoroughly validated, leading to higher quality software and faster feedback cycles. This section details how to configure build steps for various programming languages, integrate unit tests and code quality checks, and interpret build logs.
Configuring Build Steps for Various Programming Languages
The build steps are the heart of a Jenkins job, specifying the commands and actions to be performed during the build process. Jenkins supports a wide array of build steps, allowing integration with various build tools and languages. The configuration varies depending on the programming language used in the project.Here are some common examples:
- Java: For Java projects, you’ll typically use tools like Maven or Gradle for building and managing dependencies. Jenkins provides dedicated plugins and build steps for these tools, simplifying the build process.
- Python: Python projects often utilize tools like `pip` and `pytest`. Jenkins can execute shell scripts or invoke Python directly to run these tools.
- JavaScript: JavaScript projects often employ build tools such as npm, yarn, or Grunt/Gulp. Jenkins can execute these tools through shell commands or by utilizing specific plugins.
Integrating Unit Tests and Code Quality Checks
Integrating unit tests and code quality checks is essential for maintaining code quality and identifying issues early in the development cycle. Jenkins facilitates this integration through various plugins and build steps.
- Unit Tests: Unit tests are small, isolated tests that verify the functionality of individual units of code. Jenkins can execute these tests and report the results. For example, in Java, you might use JUnit or TestNG. In Python, you can use `pytest` or `unittest`. The results of these tests can be displayed within Jenkins.
- Code Quality Checks: Code quality checks analyze the codebase for potential issues such as style violations, code smells, and security vulnerabilities. Tools like SonarQube, ESLint (for JavaScript), and Pylint (for Python) can be integrated into Jenkins. Jenkins can then display the results of these checks, highlighting areas that need attention.
Viewing Build Logs and Identifying Errors
Build logs are the primary source of information about the build process. They provide detailed information about each step executed, including any errors or warnings encountered. Understanding how to interpret build logs is crucial for troubleshooting build failures.
- Accessing Build Logs: Within a Jenkins job, you can access the build logs by clicking on a specific build number. The logs are displayed in real-time as the build progresses.
- Identifying Errors: Errors are typically highlighted in the logs. Look for s like “ERROR,” “FAIL,” or “exception.” These s indicate a problem that needs to be addressed. The log messages will provide information about the cause of the error and the location in the code where it occurred.
- Analyzing Warnings: Warnings indicate potential issues that may not necessarily cause the build to fail but should be investigated. Warnings can point to code style violations, potential bugs, or other areas that could be improved.
- Filtering and Searching Logs: Jenkins provides features for filtering and searching build logs. This allows you to quickly locate specific messages or errors within the log.
Build Step Configurations for Common Programming Languages
The following table provides examples of build step configurations for common programming languages. These are general examples and may need to be adjusted based on the specific project and requirements.
| Language | Build Tool | Build Step Configuration | Example Command |
|---|---|---|---|
| Java | Maven | Invoke top-level Maven targets | clean install |
| Python | pip | Execute shell | pip install -r requirements.txt && pytest |
| JavaScript | npm | Execute shell | npm install && npm test |
| C# | MSBuild | Build a Visual Studio project or solution using MSBuild | msbuild MyProject.sln /p:Configuration=Release |
Implementing Pipelines with Jenkins

Pipelines are a core feature of Jenkins, enabling the automation of complex build, test, and deployment processes. They provide a robust and flexible way to implement Continuous Integration and Continuous Delivery (CI/CD) practices, streamlining the software development lifecycle. This section delves into the implementation of Pipelines, exploring their benefits, different types, and practical examples.
Benefits of Using Pipelines for CI/CD
Pipelines offer several advantages over traditional Jenkins jobs, particularly in the context of CI/CD. They improve efficiency, reliability, and collaboration within development teams.
- Automation and Orchestration: Pipelines automate the entire software delivery process, from code commit to deployment. This reduces manual intervention, minimizes errors, and accelerates the release cycle.
- Version Control: Pipeline definitions are typically stored in source control (e.g., Git), allowing for versioning, collaboration, and auditability. This ensures that the build process is reproducible and tracks changes over time.
- Reproducibility: By defining the entire build process in code, Pipelines ensure that builds are consistent and reproducible across different environments. This eliminates “works on my machine” scenarios and promotes predictable results.
- Scalability and Flexibility: Pipelines can be easily scaled to accommodate complex projects and evolving requirements. They support various stages, steps, and integrations, allowing for customization to meet specific needs.
- Improved Visibility and Monitoring: Pipelines provide a clear view of the build process, including progress, status, and logs. This facilitates monitoring, troubleshooting, and performance optimization.
- Enhanced Collaboration: Storing pipeline definitions in source control fosters collaboration among development, operations, and QA teams. All team members can contribute to and understand the build process.
Declarative vs. Scripted Pipelines
Jenkins Pipelines can be defined using two primary approaches: declarative and scripted. Each approach has its strengths and weaknesses.
- Declarative Pipelines: Declarative Pipelines offer a simplified and structured syntax for defining pipelines. They use a pre-defined set of s and a more constrained structure, making them easier to read and understand, especially for beginners. This approach is generally recommended for most use cases due to its clarity and maintainability.
- Scripted Pipelines: Scripted Pipelines provide greater flexibility and control. They use a Groovy-based scripting language, allowing for more complex logic and customization. While more powerful, scripted pipelines can be more challenging to write and maintain, requiring a deeper understanding of Groovy and the Jenkins Pipeline API.
Examples of Pipeline Scripts for Common CI/CD Tasks
The following examples illustrate how to define Pipelines for common CI/CD tasks using both declarative and scripted approaches. These examples demonstrate the basic structure and syntax, and can be adapted to specific project requirements.
Declarative Pipeline Example (Simple Build and Test)
This example defines a declarative Pipeline that checks out code from a Git repository, builds a Java application using Maven, and runs unit tests.
pipeline agent any stages stage('Checkout') steps git 'https://github.com/your-repository.git' stage('Build') steps sh 'mvn clean install' stage('Test') steps sh 'mvn test' post success echo 'Build successful!' failure echo 'Build failed!' Scripted Pipeline Example (Deploying to a Staging Environment)
This example shows a scripted Pipeline that deploys a web application to a staging environment after successful build and test.
node stage('Checkout') git 'https://github.com/your-repository.git' stage('Build') sh 'mvn clean install' stage('Test') sh 'mvn test' stage('Deploy to Staging') // Replace with your deployment logic sh 'scp target/*.war user@staging-server:/var/www/staging' post always echo 'Pipeline finished.' Defining Stages, Steps, and Post-Build Actions in a Pipeline
Pipelines are structured around stages, steps, and post-build actions, which define the workflow of the CI/CD process.
- Stages: Stages represent logical groupings of tasks, such as “Checkout,” “Build,” “Test,” and “Deploy.” They provide a high-level view of the pipeline’s progress. Each stage can contain multiple steps.
- Steps: Steps are the individual actions performed within a stage. They can include executing shell commands, running build tools, deploying artifacts, and more. Steps are the building blocks of the pipeline’s functionality.
- Post-Build Actions: Post-build actions are executed after the completion of a stage or the entire pipeline. They can be used to send notifications, archive artifacts, or perform cleanup tasks. Post-build actions provide a mechanism for handling success, failure, or other pipeline outcomes.
The structure of these elements varies slightly between declarative and scripted pipelines, but the underlying concepts remain the same. In declarative pipelines, stages, steps, and post-build actions are defined using specific s and syntax within the pipeline block. In scripted pipelines, these elements are defined using Groovy code and the Jenkins Pipeline API.
For example, a stage in a declarative pipeline is defined using the stage , followed by a name and a block containing the steps to be executed. A step is typically a simple shell command executed using the sh . Post-build actions are defined using the post section, which specifies actions to be performed based on the pipeline’s status (e.g., success, failure, always).
In a scripted pipeline, stages are often defined using the stage function, and steps are executed using Groovy code. Post-build actions are handled using the post block, similar to declarative pipelines, but with more flexibility in terms of the actions that can be performed.
Integrating Jenkins with Version Control Systems
Integrating Jenkins with version control systems is a cornerstone of continuous integration. It allows Jenkins to automatically detect changes in your codebase, trigger builds, and provide rapid feedback to developers. This integration streamlines the development process, reduces the time it takes to identify and fix errors, and ultimately improves software quality.
Integrating Jenkins with Git and Other Version Control Systems
Jenkins seamlessly integrates with various version control systems, with Git being the most popular. Other supported systems include Subversion (SVN), Mercurial, and others via plugins. The process involves configuring a Jenkins job to connect to a repository and specify how Jenkins should retrieve the source code.To integrate with Git, the following steps are typically involved:
- Installing the Git Plugin: Ensure the Git plugin is installed in Jenkins. This plugin provides the necessary functionality for interacting with Git repositories.
- Configuring the Job: Within a Jenkins job, you specify the Git repository URL, the branch to build, and credentials for accessing the repository (if required).
- Specifying Credentials: If the repository requires authentication, you’ll need to provide the appropriate credentials, such as a username and password or an SSH key. Jenkins securely stores these credentials.
- Polling for Changes: Jenkins can poll the repository at regular intervals to check for changes. This is a basic method for triggering builds.
- Choosing the Right SCM: In the job configuration, select the appropriate SCM (Source Code Management) system, such as Git, and fill in the required details.
For Subversion (SVN), the process is similar, but you’ll configure the SVN repository URL and credentials instead. Jenkins uses the SVN plugin to communicate with the SVN server. Mercurial integration follows a similar pattern, requiring the installation of the Mercurial plugin and configuration of the repository details.
Configuring Webhooks to Trigger Builds Automatically
Webhooks offer a more efficient and responsive way to trigger builds compared to polling. When a change is pushed to the version control system, a webhook sends a notification to Jenkins, which then immediately starts a build. This ensures builds are triggered promptly and reduces unnecessary polling.To configure webhooks:
- Configure Webhook in Version Control System: In your Git repository (e.g., GitHub, GitLab, Bitbucket), you configure a webhook. The webhook URL points to your Jenkins instance, specifically to the endpoint that handles webhook notifications.
- Configure Jenkins to Receive Webhooks: Within the Jenkins job configuration, you’ll enable the option to trigger builds from webhooks. This often involves selecting the appropriate option in the “Build Triggers” section, such as “GitHub hook trigger for Git SCM polling.”
- Security Considerations: It’s crucial to secure your webhook endpoint to prevent unauthorized access. This can involve using secret tokens or other authentication mechanisms.
- Testing the Integration: After configuration, test the webhook by pushing a change to the repository and verifying that the build is triggered automatically.
For example, in GitHub, you’d navigate to the “Settings” tab of your repository, then to “Webhooks.” You’d add a new webhook, providing the Jenkins URL and a payload format (usually `application/json`). In Jenkins, you’d configure the job to listen for GitHub webhook events. When a push event occurs, GitHub sends a payload to Jenkins, triggering the build.
Managing Branches and Pull Requests within Jenkins
Jenkins can be configured to handle different branches and pull requests effectively, supporting parallel development and code review processes. This allows developers to work on separate features without interfering with the main codebase and to integrate their changes after review.Here’s how Jenkins manages branches and pull requests:
- Branch Building: You can configure Jenkins to build specific branches. This is usually done by specifying the branch name (e.g., `main`, `develop`, or a feature branch) in the job configuration.
- Pull Request Integration: Jenkins can integrate with pull requests. When a pull request is created, Jenkins can automatically trigger a build to test the changes in the pull request. This allows for early detection of integration issues.
- Using Plugins: Plugins such as the “GitHub Pull Request Builder” or “GitLab Merge Request Builder” simplify the process of integrating with pull requests. These plugins automatically detect pull requests and trigger builds.
- Setting up the Plugin: Install and configure the plugin in Jenkins, providing the necessary credentials and repository information.
- Configuring Triggers: Configure the plugin to trigger builds based on pull request events, such as the creation of a new pull request or updates to an existing one.
- Reporting Results: The plugin can report build results back to the pull request, providing developers with immediate feedback on their changes. This is often displayed directly in the pull request interface (e.g., GitHub, GitLab).
For example, using the “GitHub Pull Request Builder” plugin, Jenkins will automatically build pull requests submitted to a GitHub repository. The build results (success or failure) are then reported back to the GitHub pull request page, allowing developers to see if their changes have introduced any issues. This automated process streamlines code reviews and helps ensure that only tested code is merged into the main branch.
Best Practices for Version Control Integration with Jenkins
Integrating version control with Jenkins requires careful planning and execution.
- Use a dedicated service account: Avoid using personal credentials for accessing the version control system. Create a dedicated service account with limited permissions for Jenkins.
- Secure your credentials: Never hardcode credentials in your Jenkins job configuration. Use Jenkins’ credential management system to store and manage credentials securely.
- Implement automated testing: Ensure that every build includes automated tests. This helps catch integration issues early in the development cycle.
- Use webhooks for responsiveness: Webhooks provide a more immediate response to code changes than polling.
- Automate branch management: Use Jenkins to automate the creation, building, and merging of branches.
- Monitor build results: Regularly monitor build results and address any failures promptly.
- Keep plugins updated: Regularly update Jenkins plugins to benefit from bug fixes, security patches, and new features.
- Consider parallel builds: If your build process is time-consuming, consider using parallel builds to speed up the feedback loop.
Notifications and Reporting in Jenkins
Jenkins’s effectiveness extends beyond simply automating builds; it provides robust mechanisms for keeping teams informed and tracking the health of projects. Notifications and reporting are crucial components, ensuring that developers, testers, and stakeholders receive timely updates on build status, test results, and code quality metrics. This proactive approach fosters collaboration, accelerates issue resolution, and contributes to overall software quality.
Configuring Email Notifications for Build Results
Email notifications are a fundamental aspect of effective continuous integration. They alert team members to build successes, failures, and other important events, allowing for immediate action when necessary.To configure email notifications:
- Access Jenkins Configuration: Navigate to the Jenkins dashboard and access the “Configure System” section under “Manage Jenkins.”
- Configure Email Settings: Within the “Configure System” page, locate the “Email Notification” section. Here, you’ll configure the SMTP server details, including the host, port, and authentication credentials. This section is crucial for establishing a connection to your email server.
- Configure Default Sender: Specify the default sender address that will be used for sending notifications. This helps recipients recognize the source of the emails.
- Configure Email Notifications for Jobs: Within the configuration of each Jenkins job, find the “Post-build Actions” section. Select “Email Notifications.”
- Specify Recipients: Add the email addresses of the recipients who should receive notifications. You can specify individual addresses, distribution lists, or use variables.
- Customize Email Content: Jenkins allows for customizing the email content. You can include details like the build number, build status, console output, and any relevant test results.
- Test the Configuration: After configuring the email settings, it is essential to test them to ensure they are working correctly. Jenkins provides a test feature within the “Configure System” section.
Detailed Illustration: Email Notification Setup Process with JenkinsThe following describes the process of setting up email notifications in Jenkins, using a visual representation of the key steps:
Step 1: Accessing the Configuration (Conceptual Image: A simplified illustration of the Jenkins dashboard with the “Manage Jenkins” option highlighted and pointing towards “Configure System.”)
This initial step involves logging into the Jenkins dashboard and navigating to the “Manage Jenkins” section. From there, you select “Configure System.” This is the starting point for setting up global email settings.
Step 2: Global Email Configuration (Conceptual Image: A screenshot or illustration of the “Configure System” page, with the “Email Notification” section highlighted. Key fields like “SMTP server,” “SMTP port,” “User Name,” and “Password” are clearly visible.)
This image focuses on the “Email Notification” section within the “Configure System” page.
Here, you input the details of your SMTP server, including the server address, port number (typically 25, 465, or 587), and authentication credentials (username and password). The “Default User E-mail Suffix” is also shown.
Step 3: Job-Specific Email Configuration (Conceptual Image: A screenshot or illustration of the configuration page for a specific Jenkins job. The “Post-build Actions” section is highlighted, with “Email Notification” selected.)
This image depicts the configuration page for an individual Jenkins job. In the “Post-build Actions” section, the “Email Notification” option is selected. Below this, fields for specifying the recipients’ email addresses and customizing the email content are displayed.
Step 4: Recipient and Content Configuration (Conceptual Image: A close-up of the email notification settings within a Jenkins job configuration. Fields for entering recipients (e.g., “Recipients List”) and customizing the email subject and body are visible.)
This image zooms in on the specific settings within the job configuration. You can see the field for specifying recipients (e.g., email addresses), and options for customizing the email subject and body. This allows for tailoring the notification to the specific needs of the project.
Step 5: Test and Save (Conceptual Image: A screenshot or illustration showing the “Test configuration” button in the “Configure System” page or the “Save” button in the job configuration. A successful test result is displayed, indicating the email configuration is working.)
This image emphasizes the final steps. It shows the “Test configuration” button, allowing you to verify the email settings.
It also includes a “Save” button to save the configuration. A successful test result confirms the email configuration is working correctly.
Integrating with Reporting Tools for Test Results and Code Quality Metrics
Integrating with reporting tools is critical for visualizing test results and code quality metrics. Jenkins supports various integrations, enabling comprehensive analysis and actionable insights.
To integrate with reporting tools:
- Test Results Reporting: Jenkins supports several plugins for publishing test results, such as JUnit, TestNG, and xUnit. These plugins parse test result files (e.g., XML reports) and display the results in a user-friendly format within the Jenkins job.
- Code Quality Metrics: Integrate with code analysis tools like SonarQube, PMD, FindBugs, and Checkstyle. These tools analyze the codebase and provide metrics on code quality, potential bugs, and adherence to coding standards. Jenkins plugins allow you to display these metrics within the job and track trends over time.
- Plugin Installation: Install the necessary plugins through the Jenkins plugin manager. Search for the specific plugin you need (e.g., “SonarQube Scanner,” “JUnit”).
- Tool Configuration: Configure the tools by providing the necessary settings, such as the location of the test result files or the SonarQube server address. This usually involves specifying file paths or server URLs within the Jenkins job configuration.
- Post-Build Actions: Configure the post-build actions in your Jenkins job to publish the test results or code quality metrics. This involves selecting the appropriate plugin and specifying the necessary parameters.
- Result Visualization: After the build completes, Jenkins will display the test results and code quality metrics on the job page. You can view the number of tests passed, failed, and skipped, as well as code quality scores, violations, and trends.
Setting Up Dashboards for Visualizing Build Status and Performance
Dashboards are essential for providing a high-level overview of build status and performance. They allow teams to quickly identify issues and monitor the overall health of the CI/CD pipeline.To set up dashboards:
- Install the Dashboard View Plugin: The “Dashboard View” plugin is a popular choice for creating custom dashboards in Jenkins. Install it through the plugin manager.
- Create a Dashboard View: Navigate to the Jenkins dashboard and create a new view. Select “Dashboard View” as the view type.
- Add Jobs to the Dashboard: Configure the dashboard by adding the jobs you want to monitor. You can filter jobs based on various criteria, such as job name, regular expressions, or labels.
- Customize the Dashboard Layout: Arrange the jobs on the dashboard to suit your needs. You can choose different layouts, such as list views, grid views, or even tabbed views.
- Add Widgets (Optional): Enhance the dashboard with widgets to display additional information, such as build statistics, code quality metrics, or even external data. Several plugins offer widgets for visualizing various aspects of the build process.
- Monitor and Maintain: Regularly monitor the dashboard to identify any issues. Update the dashboard configuration as needed to reflect changes in your CI/CD pipeline.
Advanced Jenkins Features and Techniques
Jenkins offers a wealth of advanced features that go beyond basic continuous integration, enabling sophisticated automation and orchestration of your software development lifecycle. These techniques empower teams to build, test, and deploy applications with greater efficiency, scalability, and security. This section delves into some of these powerful capabilities.
Using Jenkins Plugins for Advanced Features
Jenkins’ extensibility is one of its greatest strengths. Through plugins, you can integrate Jenkins with a vast ecosystem of tools and technologies. These plugins automate tasks, add functionalities, and streamline complex workflows.The use of plugins significantly expands Jenkins’ capabilities.* Docker Integration: The Docker plugin allows you to build, test, and deploy applications within Docker containers. This facilitates consistent environments across development, testing, and production.
For instance, you can define a Jenkins job that builds a Docker image, pushes it to a registry, and then deploys it to a Kubernetes cluster.
Example
A Java application can be packaged into a Docker image. The Jenkins job utilizes the Docker plugin to build the image from a Dockerfile, tagging it with the build number, and then pushing it to a Docker registry like Docker Hub or a private registry.
Kubernetes Deployment
Plugins like the Kubernetes plugin simplify deploying applications to Kubernetes clusters. They enable you to manage deployments, scaling, and rollbacks directly from Jenkins.
Example
You can configure a Jenkins pipeline to automatically deploy a new version of a microservice to a Kubernetes cluster after successful testing. The pipeline can update the deployment configuration, triggering a rolling update without manual intervention.
Cloud Provider Integration
Plugins are available for various cloud providers, such as AWS, Google Cloud, and Azure. These plugins allow you to interact with cloud services, such as launching virtual machines, creating databases, and deploying applications to cloud environments.
Example
An AWS plugin could be used to provision an EC2 instance for running integration tests. Once the tests are complete, the instance can be terminated, optimizing resource utilization.
SonarQube Integration
Plugins like SonarQube integration enable static code analysis directly within Jenkins. This allows you to track code quality metrics, identify potential issues, and enforce coding standards as part of the CI/CD pipeline.
Example
A Jenkins job can be configured to run SonarQube analysis after a code build. The results are then displayed in the Jenkins interface, providing insights into code quality, such as code smells, bugs, and vulnerabilities.
Implementing Parallel Builds and Distributed Builds
Parallel and distributed builds are critical for accelerating the build and test processes, especially for large projects. They allow you to leverage multiple resources simultaneously, reducing the overall execution time.* Parallel Builds: Jenkins can execute multiple build steps concurrently within a single job. This is particularly useful for running tests in parallel.
Example
A Jenkins job that runs unit tests can be configured to execute tests across multiple threads or processes. This significantly reduces the time required to complete the testing phase. The configuration typically involves using build steps or pipeline stages that support parallel execution.
Distributed Builds
Distributed builds involve using multiple Jenkins agents (slaves or nodes) to distribute the workload. This allows you to scale your build infrastructure and run builds on different operating systems, architectures, or environments.
Example
You can set up a Jenkins master and multiple agent nodes, each with a different operating system. A Jenkins job can then be configured to run tests on each of these nodes, ensuring compatibility across different platforms. The Jenkins master manages the distribution of the build tasks to the available agents.
Examples of Using Environment Variables and Secrets Management within Jenkins
Environment variables and secrets management are crucial for configuring and securing your Jenkins jobs. They allow you to pass configuration information and sensitive data without hardcoding them in your build scripts.* Environment Variables: Environment variables store configuration values that can be accessed by build steps and scripts.
Example
You can define an environment variable `DATABASE_URL` to store the connection string for your database. This variable can then be used in your application’s build process, allowing you to easily switch between different database environments (e.g., development, testing, production) without modifying the build scripts.
Secrets Management
Secrets management involves securely storing and accessing sensitive data, such as passwords, API keys, and SSH keys.
Example
Jenkins provides a “Credentials” management system where you can securely store secrets. You can create credentials for your AWS access keys and then use these credentials in your Jenkins jobs to authenticate with AWS services.
Example of a pipeline using credentials
“`groovy pipeline agent any stages stage(‘Deploy to AWS’) steps withAWS(credentials: ‘aws-credentials’) sh ‘aws s3 sync ./dist s3://my-bucket’ “` In this example, `aws-credentials` is the ID of the credentials configured in Jenkins.
The `withAWS` step uses these credentials to authenticate with AWS.
Key Jenkins Plugins for Advanced CI/CD Tasks
A well-chosen set of plugins can significantly enhance your Jenkins CI/CD capabilities. The following is a list of plugins that can be particularly helpful for advanced CI/CD tasks:* Docker Plugin: Facilitates building, testing, and deploying applications within Docker containers.
Kubernetes Plugin
Simplifies deploying applications to Kubernetes clusters.
AWS, Azure, and Google Cloud Plugins
Enable integration with various cloud providers.
SonarQube Scanner
Integrates static code analysis into your build process.
Pipeline
GitHub/GitLab/Bitbucket Integration: Integrates with popular version control systems to trigger builds and manage pull requests.
SSH Agents
Allows secure access to remote servers and devices.
Credentials Binding Plugin
Allows secure access to secrets.
Publish Over SSH
Allows publishing build artifacts to remote servers over SSH.
Ansible Plugin
Enables automated configuration management and application deployment using Ansible.
Slack/Microsoft Teams/Email Notifications
Enables integration with communication platforms for build notifications.
Troubleshooting and Best Practices for Jenkins
Effectively managing a Jenkins environment requires not only understanding its functionalities but also the ability to diagnose and resolve issues that may arise. This section focuses on troubleshooting common problems, implementing security best practices, and ensuring the resilience of your Jenkins instance through backup and recovery procedures. By following these guidelines, you can maintain a stable and secure CI/CD pipeline.
Common Troubleshooting Tips for Jenkins Builds
Jenkins builds can encounter various issues, ranging from configuration errors to infrastructure problems. Understanding how to diagnose and resolve these issues is crucial for maintaining a smooth CI/CD process.
- Check the Build Console Output: The console output is the primary source of information when a build fails. It provides detailed logs, including error messages, stack traces, and system information. Carefully review the output to identify the root cause of the problem. Look for specific error codes, file paths, and any unusual behavior.
- Examine Jenkins Logs: Jenkins logs provide valuable insights into the server’s operation. These logs can help identify issues related to plugins, configuration changes, or server performance. Access the logs through the Jenkins web interface (Manage Jenkins -> System Log) or by directly accessing the log files on the server.
- Verify Plugin Compatibility: Ensure that all installed plugins are compatible with the Jenkins version you are using. Incompatible plugins can cause builds to fail or the Jenkins server to become unstable. Check the Jenkins plugin manager for updates and compatibility information.
- Review Configuration Settings: Incorrect configuration settings can lead to build failures. Double-check the job configuration, global configuration, and any relevant plugin settings. Pay close attention to parameters such as SCM URLs, build triggers, and environment variables.
- Test with a Minimal Configuration: If a build fails, try simplifying the job configuration to isolate the problem. For example, disable plugins, remove steps, or use a simpler SCM repository. This approach can help pinpoint the specific component causing the issue.
- Check Network Connectivity: Network issues can prevent Jenkins from accessing repositories, build tools, or other resources. Verify network connectivity between the Jenkins server and all necessary endpoints. Use tools like ping or traceroute to diagnose network problems.
- Monitor Disk Space and Resources: Ensure that the Jenkins server has sufficient disk space and system resources (CPU, memory). Insufficient resources can lead to build failures or server instability. Monitor resource usage using system monitoring tools.
- Restart Jenkins: Sometimes, simply restarting Jenkins can resolve temporary issues or clear up cached data. Restart Jenkins through the web interface (Manage Jenkins -> Restart) or by restarting the server process.
- Consult the Jenkins Documentation and Community: The Jenkins documentation and community forums are excellent resources for troubleshooting. Search for error messages, read articles, and ask questions to get help from experienced users.
Best Practices for Securing Jenkins Instances
Securing your Jenkins instance is crucial to protect your CI/CD pipeline and sensitive data. Implementing these best practices can significantly reduce the risk of security breaches.
- Use Strong Authentication: Implement strong authentication mechanisms to protect access to your Jenkins instance.
- Enable Security: Go to Manage Jenkins -> Configure Global Security and enable security.
- Choose an Authentication Realm: Select an appropriate authentication realm, such as Jenkins’ own user database, LDAP, or Active Directory.
- Enforce Strong Passwords: Enforce strong password policies to prevent unauthorized access.
- Implement Role-Based Access Control (RBAC): RBAC allows you to define user roles and permissions, limiting access to sensitive resources.
- Assign Roles: Create roles with specific permissions, such as read, write, and admin.
- Assign Users to Roles: Assign users to appropriate roles based on their responsibilities.
- Regularly Review Permissions: Periodically review and update user permissions to ensure they remain appropriate.
- Regularly Update Jenkins and Plugins: Keeping Jenkins and its plugins up-to-date is essential to patch security vulnerabilities.
- Enable Automatic Updates: Configure Jenkins to automatically check for and install updates.
- Test Updates in a Staging Environment: Test updates in a staging environment before deploying them to production.
- Monitor Security Advisories: Stay informed about security advisories related to Jenkins and its plugins.
- Use HTTPS: Enable HTTPS to encrypt all communication between users and the Jenkins server.
- Obtain an SSL/TLS Certificate: Obtain a valid SSL/TLS certificate from a trusted certificate authority.
- Configure Jenkins to Use HTTPS: Configure Jenkins to use HTTPS, including specifying the certificate and key files.
- Enforce HTTPS Redirects: Configure the web server to redirect all HTTP traffic to HTTPS.
- Restrict Access to Jenkins: Limit access to the Jenkins server to authorized users and networks.
- Firewall Rules: Configure firewall rules to restrict access to the Jenkins server’s ports.
- Network Segmentation: Segment the network to isolate the Jenkins server from other sensitive systems.
- Use a Reverse Proxy: Use a reverse proxy to provide an additional layer of security and control access.
- Audit Jenkins Configuration and Logs: Regularly audit Jenkins configuration and logs to identify any security breaches or suspicious activities.
- Monitor User Activity: Monitor user logins, configuration changes, and build activities.
- Review Security Logs: Review security logs for any unauthorized access attempts or suspicious events.
- Regularly Review Configurations: Review Jenkins configuration settings to ensure they are secure and up-to-date.
- Protect Sensitive Data: Secure sensitive data, such as credentials, API keys, and secrets, used in your Jenkins jobs.
- Use Credentials Management: Utilize Jenkins’ built-in credential management system to store and manage credentials securely.
- Encrypt Sensitive Information: Encrypt sensitive information stored in Jenkins jobs or configuration files.
- Avoid Hardcoding Credentials: Avoid hardcoding credentials directly in your build scripts or configuration files.
- Implement Regular Backups: Regularly back up your Jenkins configuration and data to protect against data loss.
Backing Up and Restoring Jenkins Configurations
Protecting your Jenkins configuration is vital for disaster recovery and maintaining the integrity of your CI/CD pipeline. Implementing a reliable backup and restore strategy ensures that you can recover your Jenkins instance in case of data loss or corruption.
- Backup Strategies:
- Full Backup: This involves backing up the entire Jenkins home directory, which contains all configuration files, job definitions, build artifacts, and plugin data. This is the most comprehensive backup method.
- Configuration Backup: This focuses on backing up only the configuration files, excluding build artifacts and other data. This method is faster and suitable if you can rebuild artifacts.
- Incremental Backup: This involves backing up only the changes made since the last backup. This is useful for reducing backup time and storage space.
- Backup Process:
- Stop Jenkins: It is recommended to stop Jenkins before performing a backup to ensure data consistency.
- Locate the Jenkins Home Directory: The Jenkins home directory contains all configuration data. Its location depends on the installation method and operating system.
- Create a Backup: Use a suitable backup tool (e.g., rsync, tar, or your operating system’s backup utility) to create a copy of the Jenkins home directory or specific configuration files.
- Store Backups Securely: Store backups in a secure location, such as a separate server, cloud storage, or offsite storage, to protect them from data loss.
- Restore Process:
- Stop Jenkins: Stop the Jenkins service before restoring the backup.
- Erase or Rename the Existing Jenkins Home Directory: Before restoring the backup, it is necessary to clear the current Jenkins configuration. Rename or delete the existing Jenkins home directory.
- Restore the Backup: Use the backup tool to restore the Jenkins home directory or the configuration files from the backup location.
- Start Jenkins: Start the Jenkins service, and verify that the restored configuration is working correctly.
- Post-Restore Verification: Verify the functionality of Jenkins, including jobs, plugins, and configurations, after the restore process.
- Backup and Restore Automation:
- Automated Scripts: Create scripts to automate the backup and restore processes. This reduces the risk of human error and ensures consistent backups.
- Jenkins Plugins: Utilize Jenkins plugins designed for backup and restore, such as the “thinBackup” plugin. These plugins simplify the process and offer additional features.
- Scheduling: Schedule backups to run automatically on a regular basis (e.g., daily, weekly) to ensure data protection.
Common Jenkins Errors and Solutions
Understanding common Jenkins errors and their solutions can significantly reduce downtime and improve the efficiency of your CI/CD pipeline. The following table provides a summary of common errors and how to address them.
| Error | Description | Possible Causes | Solutions |
|---|---|---|---|
| Build Failure: SCM Checkout Failed | The build failed because Jenkins could not check out the source code from the version control system (e.g., Git, Subversion). |
|
|
| Build Failure: Java.lang.OutOfMemoryError | The build failed due to insufficient memory allocated to the Java Virtual Machine (JVM). |
|
|
| Build Failure: Plugin Compatibility Issues | The build failed because of compatibility issues with installed plugins. |
|
|
| Build Failure: Permission Denied | The build failed due to insufficient permissions to access resources, execute commands, or write files. |
|
|
Final Conclusion
In conclusion, mastering Jenkins empowers developers to automate their build, test, and deployment processes, leading to faster release cycles, improved code quality, and enhanced collaboration. From the initial setup to advanced pipeline configurations, this guide has provided a comprehensive overview of Jenkins, equipping you with the knowledge and tools to revolutionize your software development workflow. Embrace the power of automation and watch your projects thrive with the efficiency and reliability that Jenkins brings.
Top FAQs
What is Continuous Integration (CI)?
Continuous Integration is a software development practice where developers frequently merge code changes into a central repository, after which automated builds and tests are run to detect integration errors early.
What are the main benefits of using Jenkins?
Jenkins automates the build, test, and deployment processes, reduces manual effort, detects errors early, improves code quality, and accelerates software delivery cycles.
How often should I commit code changes to the repository?
The best practice is to commit code changes frequently, ideally multiple times a day. This allows for faster feedback and easier identification of issues.
What are the system requirements for running Jenkins?
The system requirements for Jenkins depend on the project size and complexity. Generally, a system with a multi-core processor, sufficient RAM (at least 2GB), and adequate disk space is recommended.
What are some common Jenkins plugins?
Essential plugins include Git, Maven Integration, JUnit, and various plugins for integrating with cloud providers, code quality tools, and notification systems.