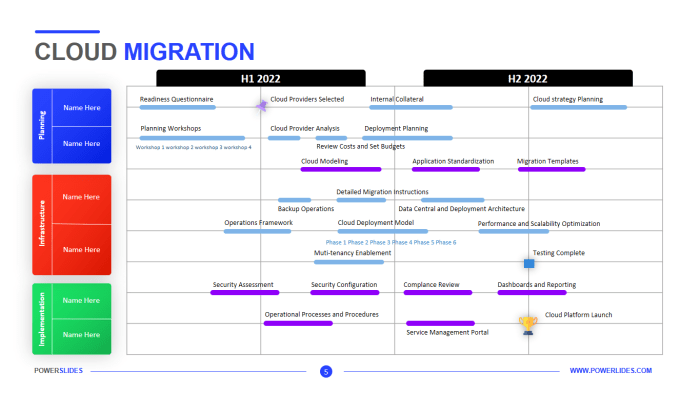
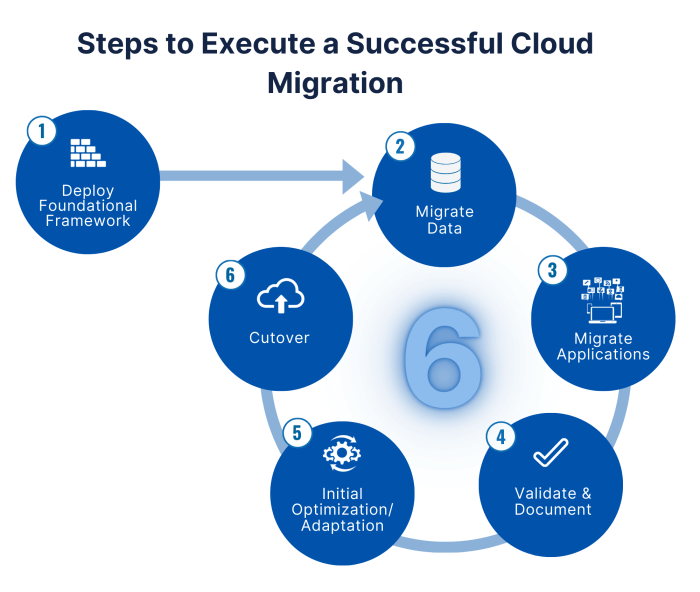
Cloud migration presents significant opportunities for enhanced scalability, cost efficiency, and innovation; however, it simultaneously introduces a complex landscape of potential risks that must be meticulously managed. This analysis will dissect the multifaceted challenges inherent in cloud migration projects, examining technical, financial, operational, and compliance-related vulnerabilities. The objective is to provide a structured framework for identifying, assessing, mitigating, and monitoring these risks, thereby enabling organizations to successfully navigate the transition to the cloud.
The scope encompasses a detailed examination of various risk categories, including data security breaches, vendor lock-in, performance degradation, and cost overruns. Furthermore, it will delve into the application of established risk assessment methodologies, outlining procedures for probability and impact analysis. This will be complemented by practical mitigation strategies, such as data encryption, vendor diversification, and performance testing, and tailored approaches for specific cloud platforms like AWS, Azure, and GCP.
Risk Identification in Cloud Migration
Identifying and understanding potential risks is a critical first step in any successful cloud migration strategy. A proactive approach to risk management allows organizations to anticipate challenges, develop mitigation strategies, and ultimately minimize disruptions and costs associated with transitioning to the cloud. This process involves a comprehensive assessment of various risk categories, potential threats, and the development of effective detection and response mechanisms.
Common Risk Categories in Cloud Migration
Cloud migration projects encompass a broad spectrum of risks, which can be broadly categorized into technical, financial, and operational areas. Each category presents unique challenges that must be addressed to ensure a smooth and successful transition. Ignoring any of these categories can lead to significant setbacks, including project delays, cost overruns, and security breaches.
- Technical Risks: These risks relate to the technical aspects of the migration process, including compatibility issues, data integrity, performance bottlenecks, and integration challenges. They often stem from complexities in the existing IT infrastructure, the chosen cloud platform, and the migration approach.
- Financial Risks: Financial risks involve the potential for unexpected costs, such as those related to data transfer, storage, compute resources, and vendor lock-in. Inadequate cost planning, fluctuating cloud pricing models, and inefficient resource utilization can lead to significant financial burdens.
- Operational Risks: Operational risks concern the impact of the migration on business operations, including service disruptions, downtime, and the need for new skillsets and training. Changes to existing processes, security vulnerabilities, and the complexities of managing a distributed cloud environment can all contribute to operational risks.
Potential Risks in Cloud Migration
A detailed understanding of potential risks is crucial for developing effective mitigation strategies. The following list provides a comprehensive overview of specific risks that organizations may encounter during cloud migration, covering technical, financial, and operational aspects:
- Data Breaches: The risk of unauthorized access, disclosure, alteration, or destruction of sensitive data. This can occur due to misconfigured security settings, vulnerabilities in cloud platform services, or malicious attacks.
- Vendor Lock-in: Dependence on a specific cloud provider, making it difficult and costly to switch to another provider or repatriate data. This can limit flexibility and negotiating power.
- Performance Issues: Degradation in application performance due to network latency, insufficient compute resources, or inefficient application design. This can lead to a poor user experience.
- Downtime and Service Disruptions: Unplanned outages or interruptions in service availability. This can result from infrastructure failures, configuration errors, or denial-of-service attacks.
- Compliance and Regulatory Issues: Failure to meet industry-specific regulations or compliance requirements, such as GDPR or HIPAA. This can lead to legal penalties and reputational damage.
- Data Loss or Corruption: Loss or corruption of data during the migration process or due to unforeseen events. This can have severe consequences for business operations.
- Cost Overruns: Exceeding the planned budget due to inaccurate cost estimations, inefficient resource utilization, or unexpected charges.
- Security Vulnerabilities: Weaknesses in the security posture of the cloud environment, making it susceptible to attacks.
- Integration Challenges: Difficulties in integrating cloud-based applications with existing on-premises systems.
- Lack of Skills and Expertise: Insufficient in-house skills or reliance on external consultants, which can lead to delays and increased costs.
- Network Connectivity Issues: Problems with network connectivity between on-premises systems and the cloud environment.
- Application Compatibility Issues: Incompatibilities between existing applications and the cloud platform.
- Unexpected Migration Delays: Delays in the migration process due to unforeseen technical challenges or resource constraints.
- Inefficient Resource Utilization: Over-provisioning or under-provisioning of cloud resources, leading to wasted resources or performance bottlenecks.
Risk Identification Specific to Cloud Platforms
Different cloud platforms (e.g., AWS, Azure, GCP) have their unique features, services, and security models, which introduce platform-specific risks. Identifying these risks requires a deep understanding of the chosen platform’s architecture, services, and security best practices. The following table provides an overview of potential risks, specific to the chosen cloud platform, along with their detection methods:
| Risk Category | Specific Risk | Detection Method |
|---|---|---|
| Data Security (AWS) | Unencrypted data at rest in S3 buckets. | Regular audits using AWS Config and AWS Trusted Advisor to identify unencrypted S3 buckets. Implement automated alerts for new buckets. |
| Cost Optimization (Azure) | Over-provisioned virtual machines. | Utilize Azure Advisor to identify underutilized VMs and suggest resizing or shutting them down. Monitor resource utilization metrics. |
| Performance (GCP) | Network latency between regions affecting application performance. | Use Cloud Monitoring to track network latency metrics between different regions. Conduct performance testing and load testing. |
| Identity and Access Management (AWS) | Excessive permissions granted to IAM users and roles. | Implement and regularly review the least privilege principle. Use IAM Access Analyzer to identify over-permissive policies. |
| Compliance (Azure) | Failure to meet compliance requirements for data residency. | Use Azure Policy to enforce data residency rules and ensure compliance with regulatory requirements. |
| Data Loss (GCP) | Accidental deletion of data in Cloud Storage. | Implement object versioning and lifecycle management for Cloud Storage buckets. Regularly back up data to another region or a different storage class. |
| Vendor Lock-in (AWS, Azure, GCP) | Reliance on proprietary services and features. | Adopt a multi-cloud strategy where possible. Use open-source or platform-agnostic tools and technologies. Design applications for portability. |
| Operational (AWS) | Misconfigured security groups allowing unauthorized access. | Regularly review security group rules. Utilize AWS Security Hub to identify misconfigurations. |
| Financial (Azure) | Unexpected costs from reserved instances not being fully utilized. | Monitor reserved instance utilization through Azure Cost Management. Optimize VM sizing to maximize resource usage. |
| Technical (GCP) | Application compatibility issues with Google Kubernetes Engine (GKE). | Thoroughly test applications in GKE environments before migration. Address compatibility issues with containerization and Kubernetes configurations. |
Risk Assessment Methodologies
Risk assessment is a critical component of cloud migration projects, serving as the systematic process of identifying, analyzing, and evaluating potential risks that could impact project success. Employing appropriate methodologies allows organizations to proactively mitigate threats, allocate resources effectively, and make informed decisions. This section explores various risk assessment methodologies suitable for cloud migration initiatives, comparing and contrasting their strengths and weaknesses.
Qualitative and Quantitative Risk Assessment Techniques
Risk assessment techniques are broadly categorized into qualitative and quantitative approaches. Qualitative risk assessment relies on subjective judgment and descriptive analysis, while quantitative risk assessment uses numerical data and statistical analysis to evaluate risks. The choice between these techniques depends on factors such as the project’s complexity, the availability of data, and the desired level of detail.
- Qualitative Risk Assessment: This approach uses descriptive scales (e.g., High, Medium, Low) to assess the probability and impact of risks. It relies on expert opinions, brainstorming sessions, and interviews to identify and prioritize risks.
- Pros:
- Simple and cost-effective to implement, requiring less time and resources.
- Provides a quick overview of the risk landscape.
- Suitable for projects with limited data availability.
- Cons:
- Subjective and prone to bias due to reliance on expert opinions.
- Lacks precision and may not provide a detailed understanding of risk magnitudes.
- Difficult to compare risks objectively.
- Pros:
- Quantitative Risk Assessment: This approach uses numerical data and statistical analysis to quantify the probability and impact of risks. Techniques such as Monte Carlo simulations, decision tree analysis, and sensitivity analysis are employed.
- Pros:
- Provides a more precise and objective assessment of risks.
- Allows for detailed analysis of risk impacts on project costs, schedules, and performance.
- Facilitates data-driven decision-making.
- Cons:
- More complex and time-consuming to implement.
- Requires reliable data, which may not always be available.
- Can be expensive, requiring specialized software and expertise.
- Pros:
Step-by-Step Procedure for Conducting Risk Assessment
A structured approach to risk assessment is crucial for ensuring its effectiveness. This procedure involves several key steps, which should be followed iteratively throughout the cloud migration project lifecycle.
- Risk Identification: The initial step involves identifying potential risks that could affect the cloud migration project. This process leverages various techniques, including brainstorming, checklists, interviews with stakeholders, and reviewing historical data from similar projects. Examples of identified risks could include data breaches, service downtime, cost overruns, and vendor lock-in.
- Risk Analysis: This step analyzes the identified risks to understand their potential impact and likelihood. Both qualitative and quantitative techniques can be employed. Qualitative analysis might involve assigning risk scores based on probability and impact, using a risk matrix. Quantitative analysis could involve estimating the financial impact of potential risks, such as the cost of data recovery after a security incident.
- Probability and Impact Analysis: This is a core element of risk assessment, focusing on determining the likelihood of each risk occurring (probability) and the severity of its consequences (impact).
- Probability Assessment: Assessing the probability of a risk event occurring involves determining the likelihood of each identified risk. This can be done using qualitative scales (e.g., Very Likely, Likely, Possible, Unlikely, Very Unlikely) or quantitative methods (e.g., assigning a percentage or frequency of occurrence).
For instance, the probability of a data breach might be assessed based on factors like the security posture of the current infrastructure, the security measures implemented in the cloud environment, and the threat landscape.
- Impact Assessment: Evaluating the impact of a risk event involves determining the potential consequences if the risk occurs. This includes assessing the impact on project objectives, such as cost, schedule, scope, and quality. Impact can be measured using qualitative scales (e.g., High, Medium, Low) or quantitative metrics (e.g., financial losses, downtime duration). For example, the impact of a service outage could be measured in terms of lost revenue, damage to reputation, and the cost of restoring service.
- Risk Matrix: A risk matrix is a common tool used to visually represent the probability and impact of risks. The matrix typically has two axes: probability (e.g., Low to High) and impact (e.g., Low to High). Each risk is plotted on the matrix based on its assessed probability and impact, allowing for prioritization of risks based on their severity. Risks falling into the “High” risk category (high probability and high impact) require immediate attention and mitigation strategies.
- Probability Assessment: Assessing the probability of a risk event occurring involves determining the likelihood of each identified risk. This can be done using qualitative scales (e.g., Very Likely, Likely, Possible, Unlikely, Very Unlikely) or quantitative methods (e.g., assigning a percentage or frequency of occurrence).
- Risk Prioritization: Based on the risk analysis, risks are prioritized according to their severity. This involves ranking risks based on their probability and impact scores. High-priority risks require immediate attention and the development of mitigation plans. Medium-priority risks should be monitored and managed, while low-priority risks may be accepted or monitored. A risk register is often used to document the prioritized risks, along with their associated mitigation plans.
- Risk Response Planning: Developing strategies to address the identified risks. These strategies include risk avoidance, risk transfer, risk mitigation, and risk acceptance.
- Risk Avoidance: Eliminating the risk altogether by avoiding the activity or situation that could cause it. For example, if a specific cloud service poses a significant security risk, the project team might choose to avoid using that service.
- Risk Transfer: Shifting the risk to a third party, such as through insurance or outsourcing. For instance, a company might purchase cyber liability insurance to protect against the financial impact of a data breach.
- Risk Mitigation: Reducing the likelihood or impact of a risk. This involves implementing controls and measures to minimize the potential damage. Examples include implementing security controls, conducting regular backups, and developing disaster recovery plans.
- Risk Acceptance: Accepting the risk and taking no action to avoid or mitigate it. This is typically done for low-priority risks where the cost of mitigation outweighs the potential impact.
- Risk Monitoring and Control: Continuously monitoring the identified risks, tracking the effectiveness of mitigation plans, and making adjustments as needed. This includes regularly reviewing the risk register, monitoring key risk indicators (KRIs), and conducting periodic risk assessments. The cloud environment and the threat landscape are dynamic, requiring continuous vigilance and adaptation.
Risk Mitigation Strategies
Effective risk mitigation is crucial for a successful cloud migration. It involves proactively implementing strategies to minimize the impact of identified risks. This proactive approach reduces the likelihood of issues arising during the migration process, ensuring business continuity and data integrity. The selection of appropriate mitigation strategies depends on the specific risks identified during the risk assessment phase.
Data Encryption
Data encryption is a fundamental security measure to protect sensitive information during cloud migration. Implementing encryption safeguards data both in transit and at rest, rendering it unreadable to unauthorized parties. This is especially critical for organizations handling confidential data such as Personally Identifiable Information (PII) or financial records.
| Risk | Mitigation Strategy | Implementation Steps | Expected Outcome |
|---|---|---|---|
| Data Breach During Migration | Data Encryption (at rest and in transit) |
| Reduced risk of data compromise, compliance with data privacy regulations (e.g., GDPR, HIPAA). |
Vendor Diversification
Vendor diversification is a strategy that mitigates the risk of vendor lock-in and service disruptions. Relying on a single cloud provider can create vulnerabilities, such as price increases, service outages, or lack of innovation. Employing multiple cloud providers allows organizations to leverage the strengths of each, maintain competitive pricing, and ensure business continuity.
| Risk | Mitigation Strategy | Implementation Steps | Expected Outcome |
|---|---|---|---|
| Vendor Lock-in | Vendor Diversification (Multi-cloud Strategy) |
| Reduced dependence on a single vendor, improved flexibility and negotiating power, enhanced business continuity. |
Performance Testing
Performance testing is a critical mitigation strategy to ensure application performance and stability after cloud migration. It involves simulating real-world user traffic to identify and address potential performance bottlenecks before the migration is complete. This proactive approach prevents performance degradation and ensures a smooth user experience.
| Risk | Mitigation Strategy | Implementation Steps | Expected Outcome |
|---|---|---|---|
| Performance Degradation After Migration | Performance Testing (Load Testing, Stress Testing) |
| Improved application performance, ensured user satisfaction, minimized downtime. |
Data Security Risks and Mitigation
Migrating data to the cloud introduces a unique set of data security risks that must be carefully considered and addressed. Failure to do so can result in data breaches, compliance violations, and reputational damage. This section explores the specific security challenges inherent in cloud migration and provides detailed strategies to mitigate these risks.
Data Security Risks in Cloud Migration
Several specific data security risks are amplified or newly introduced during cloud migration. Understanding these risks is the first step toward effective mitigation.
- Data Breaches: Cloud environments, while offering robust security features, are still susceptible to data breaches. These breaches can occur due to misconfigurations, vulnerabilities in cloud provider infrastructure, or compromised user credentials. According to the 2023 Verizon Data Breach Investigations Report (DBIR), misconfiguration continues to be a significant contributor to data breaches.
- Data Loss: Data loss can result from various factors, including accidental deletion, hardware failures, and natural disasters. In the cloud, data loss can also be caused by failures within the cloud provider’s infrastructure or, less frequently, by malicious attacks.
- Insider Threats: Malicious or negligent insiders, whether they are employees or third-party contractors, pose a significant risk. These individuals may have access to sensitive data and could intentionally or unintentionally compromise its security. The 2023 Insider Threat Report by SANS Institute indicates a rise in insider threats, emphasizing the need for robust access controls and monitoring.
- Compliance Violations: Cloud migration can introduce complexities in meeting regulatory compliance requirements, such as GDPR, HIPAA, and PCI DSS. Failure to comply with these regulations can lead to substantial fines and legal ramifications.
- Lack of Visibility and Control: Migrating to the cloud can sometimes lead to a loss of visibility and control over data. This is particularly true if organizations are not fully aware of the security features offered by their cloud provider or if they fail to implement appropriate monitoring tools.
Encryption Strategies
Encryption is a fundamental component of data security in the cloud, protecting data both in transit and at rest. Different encryption strategies are employed depending on the specific needs of the data and the cloud environment.
- Encryption at Rest: This involves encrypting data stored within the cloud infrastructure. The encryption keys can be managed by the cloud provider or by the organization itself.
- Server-Side Encryption (SSE): The cloud provider manages the encryption and decryption of data. This is typically the easiest to implement.
- Client-Side Encryption (CSE): The data is encrypted before it is sent to the cloud provider, and the organization retains control of the encryption keys. This offers greater control but requires more management overhead.
- Encryption in Transit: Data is encrypted as it moves between the user’s device, the cloud provider’s servers, and other locations. This typically involves using protocols like Transport Layer Security (TLS) or Secure Sockets Layer (SSL).
- TLS/SSL protects data from eavesdropping and tampering.
- Protocols like HTTPS ensure secure communication over the internet.
- Key Management: Secure key management is crucial for effective encryption. This includes generating, storing, and rotating encryption keys securely. Cloud providers offer key management services (KMS), but organizations can also implement their own KMS solutions.
A strong encryption strategy combines encryption at rest and in transit, coupled with robust key management practices.
Access Control Strategies
Effective access control is critical for preventing unauthorized access to sensitive data in the cloud. This involves implementing various mechanisms to verify and authorize user access.
- Identity and Access Management (IAM): IAM systems manage user identities, authentication, and authorization. They ensure that only authorized users have access to specific resources.
- Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of verification.
- Role-Based Access Control (RBAC) assigns permissions based on user roles, ensuring that users only have access to the resources they need.
- Least Privilege Principle: Users should be granted only the minimum necessary access to perform their tasks. This reduces the potential damage from compromised accounts.
- Regular Auditing and Monitoring: Regularly auditing access logs and monitoring user activity can help detect and prevent unauthorized access attempts.
- Network Segmentation: Dividing the cloud environment into isolated segments can limit the impact of a security breach. If one segment is compromised, the attacker’s access is restricted.
Data Loss Prevention (DLP) Strategies
Data loss prevention (DLP) strategies are designed to identify and prevent sensitive data from leaving the organization’s control, whether intentionally or unintentionally.
- Data Classification: Classifying data based on its sensitivity level allows organizations to apply appropriate security controls.
- Data Loss Prevention Tools: DLP tools monitor data in transit, at rest, and in use, and can automatically detect and block unauthorized data transfers.
- Data Masking and Tokenization: These techniques protect sensitive data by replacing it with substitute values or tokens, making the data less valuable to attackers.
- Regular Data Backups: Regularly backing up data ensures that a copy is available in case of data loss due to any unforeseen events. Backups should be stored securely and tested regularly to ensure they can be restored successfully.
Secure Data Migration Process Diagram
The following diagram illustrates a secure data migration process, encompassing key steps and technologies.
Diagram Description: The diagram Artikels a secure data migration process with the following stages, connected sequentially by arrows, and uses cloud-based services.
Stage 1: Planning and Assessment.
Action
Data inventory and classification, security risk assessment, and defining the migration scope.
Technologies
Data discovery tools, security assessment tools, compliance checklists.
Stage 2: Pre-Migration Security Preparation.
Action
Implementing access controls (IAM, RBAC, MFA), configuring encryption (at rest and in transit), establishing DLP policies, and preparing for data masking.
Technologies
IAM systems, KMS, DLP solutions, data masking tools, and firewall configurations.
Stage 3: Data Migration.
Action
Transferring data using secure methods, such as encrypted network connections (HTTPS, VPN), and using cloud provider’s migration tools or third-party migration services.
Technologies
Cloud provider’s migration tools, secure file transfer protocols (SFTP), and data replication services.
Stage 4: Post-Migration Validation and Verification.
Action
Data integrity checks, validating access controls, and ensuring encryption is correctly implemented.
Technologies
Data validation tools, access control logs, and encryption verification tools.
Stage 5: Ongoing Security and Monitoring.
Action
Continuous monitoring of security logs, vulnerability scanning, regular security audits, and incident response planning.
Technologies
Security Information and Event Management (SIEM) systems, vulnerability scanners, and audit logs.
Key Features and Considerations:
- Encryption Throughout: Data is encrypted at rest and in transit.
- Access Control: Strict IAM and RBAC policies are enforced.
- Data Loss Prevention: DLP policies are implemented to prevent data leakage.
- Continuous Monitoring: Security logs are monitored continuously.
- Compliance: The entire process adheres to relevant compliance regulations.
This diagram represents a proactive approach to secure data migration, incorporating the best practices and technologies.
Compliance and Regulatory Risks
Cloud migration projects introduce new complexities regarding compliance and regulatory adherence. Organizations must proactively address these challenges to avoid legal repercussions, financial penalties, and reputational damage. Failing to comply with relevant regulations can lead to significant business disruptions and loss of customer trust. This section provides an overview of compliance risks, procedural steps for ensuring compliance, and a method for assessing the impact of regulatory requirements on the migration plan.
Common Regulatory Frameworks
Organizations must navigate a complex landscape of regulations when migrating to the cloud. Compliance requirements vary depending on the industry, the location of data processing, and the nature of the data itself. Several key regulatory frameworks frequently impact cloud migration projects.
- General Data Protection Regulation (GDPR): The GDPR, enacted by the European Union, sets stringent standards for the collection, processing, and storage of personal data of individuals within the EU. Compliance necessitates careful consideration of data residency, data access controls, and the right to be forgotten. For instance, a company migrating customer data to a cloud provider must ensure that the provider adheres to GDPR principles, including data minimization and security.
Failure to comply can result in fines of up to 4% of annual global turnover or €20 million, whichever is higher.
- Health Insurance Portability and Accountability Act (HIPAA): HIPAA in the United States regulates the handling of protected health information (PHI). Cloud migration involving PHI requires robust security measures, including encryption, access controls, and audit trails, to protect patient privacy. Cloud providers must sign Business Associate Agreements (BAAs) to ensure they are responsible for the security of PH information. For example, a healthcare provider migrating patient records to the cloud must ensure the cloud provider is HIPAA-compliant and has a BAA in place.
Non-compliance can lead to significant financial penalties and legal actions.
- Payment Card Industry Data Security Standard (PCI DSS): PCI DSS is a set of security standards designed to protect cardholder data. Organizations that process, store, or transmit cardholder data must comply with PCI DSS. Cloud migration necessitates ensuring the cloud environment and provider meet these standards, including secure network configurations, data encryption, and regular security assessments. A retailer migrating its e-commerce platform to the cloud must ensure the cloud provider maintains PCI DSS compliance to protect customer payment information.
Non-compliance can lead to fines, loss of the ability to process payments, and damage to reputation.
- Other Relevant Regulations: Beyond GDPR, HIPAA, and PCI DSS, organizations may need to comply with other industry-specific or country-specific regulations. These may include regulations related to financial services (e.g., SOX), government data (e.g., FedRAMP), or specific data privacy laws in various countries.
Procedure for Ensuring Compliance During Cloud Migration
A structured approach is essential to ensure compliance during cloud migration. The following steps provide a procedure for organizations to follow.
- Identify Applicable Regulations: Begin by identifying all relevant regulations based on the organization’s industry, geographic locations, and the type of data being migrated. This may involve legal counsel and compliance experts.
- Assess Current Compliance Posture: Conduct a thorough assessment of the current IT infrastructure’s compliance with the identified regulations. This includes reviewing existing security controls, policies, and procedures.
- Select a Compliant Cloud Provider: Choose a cloud provider that demonstrates compliance with the relevant regulations. This includes verifying certifications, such as ISO 27001, and reviewing the provider’s security practices and compliance documentation. Look for providers with specific certifications, such as a HIPAA-compliant cloud or a PCI DSS-compliant environment.
- Develop a Compliance Plan: Create a detailed plan that Artikels the steps needed to achieve and maintain compliance in the cloud environment. This plan should include timelines, responsibilities, and specific controls.
- Implement Security Controls: Implement the necessary security controls in the cloud environment, such as encryption, access controls, and intrusion detection systems. Ensure that these controls align with the requirements of the identified regulations.
- Establish Data Governance Policies: Develop and implement data governance policies that define how data is managed, accessed, and protected in the cloud. This includes policies for data retention, data deletion, and data access.
- Conduct Regular Audits and Monitoring: Establish a program of regular audits and monitoring to ensure ongoing compliance. This includes internal audits, vulnerability assessments, and penetration testing.
- Train Employees: Provide training to employees on compliance requirements and security best practices. This training should be ongoing and updated as regulations and the cloud environment evolve.
- Document Everything: Maintain comprehensive documentation of all compliance activities, including assessments, plans, controls, and audit results. This documentation is crucial for demonstrating compliance to regulators and auditors.
- Review and Update Regularly: Continuously review and update the compliance plan and security controls to adapt to changes in regulations, technology, and the cloud environment.
Assessing the Impact of Regulatory Requirements on the Migration Plan
The impact of regulatory requirements on the cloud migration plan should be assessed thoroughly to ensure a successful and compliant migration. The following considerations are crucial.
- Data Residency Requirements: Determine where data must be stored based on regulatory requirements. Some regulations, like GDPR, may mandate that data of EU citizens be stored within the EU. This impacts cloud provider selection and data migration strategies. For example, a company must select a cloud provider with data centers in the EU if it processes personal data of EU citizens.
- Data Security Controls: Identify the specific security controls required by each regulation, such as encryption, access controls, and intrusion detection systems. Ensure that the migration plan includes these controls in the cloud environment. For example, if the organization is subject to HIPAA, the migration plan must include encryption of PHI both in transit and at rest.
- Data Access and Control Requirements: Assess the requirements for data access, including who can access data and under what conditions. Ensure that the migration plan includes appropriate access controls and audit trails to meet these requirements.
- Data Retention and Disposal Policies: Understand the requirements for data retention and disposal, including how long data must be stored and how it must be securely deleted. Incorporate these requirements into the migration plan. For example, if an organization must comply with PCI DSS, it must securely dispose of cardholder data when it is no longer needed.
- Audit and Reporting Requirements: Determine the audit and reporting requirements, including the frequency of audits and the types of reports that must be generated. Ensure that the migration plan supports these requirements. For instance, a financial institution migrating to the cloud may need to generate regular reports to demonstrate compliance with regulatory requirements, which should be automated to improve efficiency.
- Compliance Costs: Estimate the costs associated with achieving and maintaining compliance, including the cost of security controls, audits, and training. Factor these costs into the overall migration budget.
- Impact on Migration Timeline: Assess how regulatory requirements will impact the migration timeline. Compliance activities may add time to the migration process. For example, implementing robust security controls and data encryption can take time, which should be considered in the migration plan.
- Risk Assessment: Perform a risk assessment to identify potential compliance risks and develop mitigation strategies. This assessment should consider the likelihood and impact of non-compliance.
Performance and Availability Risks
Migrating to the cloud presents numerous opportunities for enhanced performance and availability, but it also introduces new challenges. Understanding and mitigating these risks is crucial for a successful cloud migration strategy. Failure to address these potential issues can lead to service disruptions, performance bottlenecks, and ultimately, a negative impact on business operations.
Risks Associated with Cloud Performance and Availability During Migration
Cloud migration projects can be significantly impacted by performance and availability risks. These risks can manifest in several ways, often stemming from inadequate planning, misconfigured infrastructure, or unexpected dependencies.
- Network Latency and Bandwidth Limitations: Migrating applications to the cloud can introduce network latency, especially if the cloud provider’s data centers are geographically distant from the users or other connected systems. Insufficient bandwidth can further exacerbate performance issues, particularly during data transfers and peak usage periods. This is especially relevant for applications that are latency-sensitive, such as real-time financial trading platforms or online gaming.
- Resource Provisioning and Scalability Challenges: Incorrectly estimating resource requirements (CPU, memory, storage) during migration can lead to performance bottlenecks. Under-provisioning can cause applications to slow down or become unresponsive, while over-provisioning results in unnecessary costs. Moreover, the ability to automatically scale resources up or down based on demand is critical for maintaining optimal performance and availability, and improper configuration can hinder this process.
- Application Compatibility Issues: Not all applications are inherently cloud-ready. Legacy applications, in particular, may not be optimized for cloud environments and could experience performance degradation. Compatibility issues can arise from dependencies on specific operating systems, libraries, or hardware configurations that are not readily available in the cloud.
- Data Transfer Bottlenecks: The initial migration of large datasets can be time-consuming and resource-intensive. The transfer speed depends on the network connection, the size of the data, and the cloud provider’s data ingress/egress policies. If not properly planned, data transfer can become a significant bottleneck, delaying the migration process and impacting application performance after migration.
- Service Disruptions and Outages: Cloud providers, despite their robust infrastructure, are not immune to service disruptions. These can be caused by hardware failures, software bugs, network outages, or human error. The impact of an outage can range from minor performance degradation to complete service unavailability, leading to financial losses and reputational damage.
- Monitoring and Management Complexity: Managing performance and availability in the cloud requires sophisticated monitoring and management tools. Without proper monitoring, it can be difficult to identify and resolve performance issues quickly. Furthermore, the distributed nature of cloud environments can make it challenging to troubleshoot problems and ensure high availability.
Strategies for Optimizing Performance and Ensuring High Availability
Mitigating performance and availability risks requires a proactive and multi-faceted approach. Several strategies can be employed to optimize performance and ensure high availability throughout the cloud migration process and beyond.
- Thorough Planning and Assessment: A comprehensive assessment of existing applications, infrastructure, and data is essential before migrating to the cloud. This includes identifying performance bottlenecks, resource requirements, and potential compatibility issues. This assessment should inform the cloud migration strategy, including the selection of cloud services and the design of the target architecture.
- Choosing the Right Cloud Services: Selecting the appropriate cloud services is crucial for optimizing performance and availability. This includes choosing the right instance types, storage options, and networking configurations. For example, using a Content Delivery Network (CDN) can significantly improve performance for applications that serve content to users worldwide.
- Optimizing Application Code and Architecture: Reviewing and optimizing application code can significantly improve performance. This might involve refactoring code, optimizing database queries, and caching frequently accessed data. Furthermore, adopting a cloud-native architecture, such as microservices, can improve scalability, resilience, and overall performance.
- Implementing Robust Monitoring and Alerting: Implementing comprehensive monitoring and alerting systems is crucial for proactively identifying and resolving performance issues. This includes monitoring key metrics such as CPU utilization, memory usage, network latency, and error rates. Automated alerts should be configured to notify the operations team of any potential problems, enabling them to take corrective action quickly.
- Leveraging Automation and Infrastructure-as-Code: Automating infrastructure provisioning, configuration, and deployment can improve efficiency and reduce the risk of human error. Infrastructure-as-Code (IaC) tools allow you to define your infrastructure as code, enabling version control, repeatability, and automated deployment.
- Implementing Disaster Recovery and Business Continuity Plans: A well-defined disaster recovery (DR) and business continuity (BC) plan is essential for ensuring high availability. This includes replicating data to a secondary region or availability zone, implementing automated failover mechanisms, and regularly testing the DR plan.
- Load Testing and Performance Tuning: Conducting thorough load testing before and after migration helps identify performance bottlenecks and ensure the application can handle peak loads. Performance tuning involves adjusting system configurations and application settings to optimize performance under different load conditions.
Comparison of Cloud Deployment Models
The choice of cloud deployment model (IaaS, PaaS, or SaaS) significantly impacts performance and availability characteristics. Each model offers a different level of control, responsibility, and operational overhead, which affects how performance and availability are managed.
| Cloud Deployment Model | Performance Characteristics | Availability Characteristics |
|---|---|---|
| IaaS (Infrastructure as a Service) |
|
|
| PaaS (Platform as a Service) |
|
|
| SaaS (Software as a Service) |
|
|
Cost Management Risks
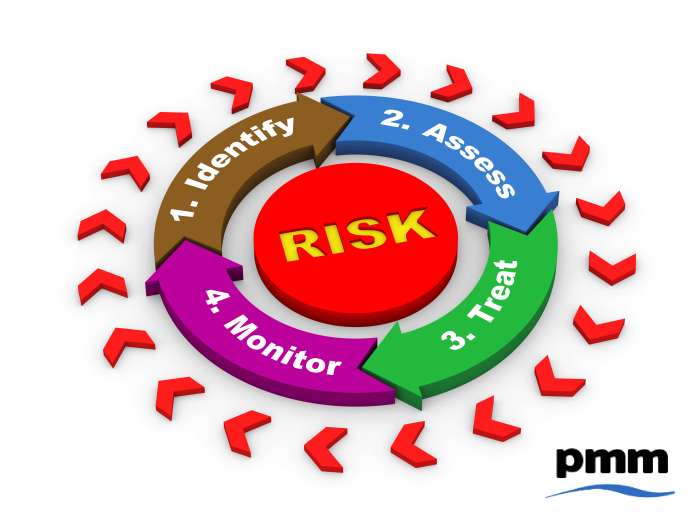
Cloud migration, while offering significant benefits, introduces several financial risks that must be proactively managed. Unexpected costs and budget overruns are common pitfalls if cost management strategies are not rigorously implemented. Failure to control costs can erode the return on investment (ROI) and potentially jeopardize the entire migration project.
Financial Risks in Cloud Migration
The financial risks associated with cloud migration are multifaceted, extending beyond the initial infrastructure costs. Understanding these risks is crucial for effective cost management.
- Unexpected Infrastructure Costs: The “pay-as-you-go” model of cloud computing can lead to unanticipated charges. Over-provisioning resources, leaving idle instances running, or failing to optimize storage can rapidly inflate costs. For example, a company might initially underestimate the storage requirements for its data migration, leading to higher-than-expected storage bills.
- Hidden Costs: Various ancillary services and features, such as data transfer fees, monitoring tools, and support contracts, can contribute to unexpected expenses. These costs are often overlooked during the initial planning phase.
- Budget Overruns: Inaccurate estimations of resource consumption, lack of cost control mechanisms, and changes in project scope can result in budget overruns. A common example is a project that expands its scope to include additional features, leading to a need for more cloud resources than originally planned.
- Vendor Lock-in: While not a direct cost, vendor lock-in can indirectly affect costs. Switching cloud providers can be expensive and complex, potentially limiting negotiating power and forcing organizations to accept price increases.
- Operational Costs: The ongoing operational expenses of managing and maintaining cloud infrastructure, including staffing and training, can be substantial.
Methods for Controlling Cloud Costs
Proactive cost management involves a combination of strategies to optimize resource utilization, monitor spending, and enforce budgetary controls.
- Resource Optimization: Right-sizing instances, eliminating idle resources, and utilizing auto-scaling features are key to optimizing resource usage. Right-sizing involves selecting the appropriate instance size based on actual workload requirements, preventing over-provisioning. Auto-scaling automatically adjusts resources based on demand, ensuring optimal performance while minimizing costs.
- Cost Monitoring and Analysis: Implementing robust cost monitoring tools provides real-time visibility into cloud spending. These tools allow for identifying cost drivers, detecting anomalies, and generating reports. Detailed analysis of spending patterns helps in making informed decisions.
- Budgeting and Forecasting: Establishing clear budgets and forecasts is crucial for controlling costs. Setting up budget alerts and notifications helps to proactively identify potential overspending. Regular forecasting allows for anticipating future cost trends and adjusting resource allocation accordingly.
- Automation: Automating tasks such as instance provisioning, decommissioning, and patching can significantly reduce operational costs and human error. Automation also facilitates consistent application of cost optimization policies.
- Reserved Instances and Savings Plans: Utilizing reserved instances or savings plans, where available, can significantly reduce the cost of compute resources. These options provide discounts in exchange for committing to a specific level of resource usage over a defined period.
- Tagging and Allocation: Tagging cloud resources with relevant metadata (e.g., project, department, application) enables accurate cost allocation and chargeback reporting. This allows for understanding where costs are originating within the organization.
Cost-Optimization Plan Flowchart
The following flowchart illustrates the key steps and decision points in a cost-optimization plan. This visual guide helps in the systematic implementation of cost-saving measures.
Start -> Assess Current Cloud Usage and Costs -> ( Gather Data: Identify current spending, resource utilization, and existing configurations.) -> Analyze Data -> ( Identify Cost Drivers: Determine which resources and services are consuming the most budget.) -> Implement Optimization Strategies -> ( Right-Sizing, Auto-Scaling, Reserved Instances, Savings Plans, Resource Tagging) -> Monitor and Track Costs -> ( Use Cloud Provider Tools, Implement Cost Management Tools) -> Analyze Results -> ( Compare Actual Costs to Budget, Identify Areas for Further Optimization) -> Refine and Iterate -> ( Adjust Optimization Strategies, Repeat the Process) -> End
This flowchart provides a structured approach to cloud cost optimization, ensuring that cost management is an ongoing process. It highlights the iterative nature of cost optimization, emphasizing the need for continuous monitoring, analysis, and refinement of strategies. The cycle ensures that costs are continuously managed and optimized over time.
Vendor Lock-in Risks
Vendor lock-in represents a significant risk in cloud migration, potentially limiting flexibility, increasing costs, and hindering innovation. It occurs when a business becomes overly reliant on a specific cloud provider’s services, making it difficult and expensive to switch to another provider or bring services back on-premises. Understanding and mitigating these risks is crucial for successful cloud adoption and long-term strategic planning.
Identifying Risks Associated with Vendor Lock-in
Vendor lock-in presents several potential challenges that can negatively impact a cloud migration strategy. These risks manifest in various forms, impacting both operational and financial aspects.
- High Switching Costs: Migrating from one cloud provider to another can be extremely costly and time-consuming. This is often due to the need to rewrite applications, reconfigure infrastructure, and retrain personnel on new platforms. The more complex the architecture and the greater the reliance on proprietary services, the higher the switching costs. For example, consider a company that has heavily integrated its applications with a specific cloud provider’s database services.
Switching to a different database technology from another provider would necessitate significant code modifications, data migration efforts, and potential downtime, leading to considerable expense and disruption.
- Limited Innovation: Being locked into a single vendor can restrict access to the latest technologies and innovations. Cloud providers constantly evolve their offerings, and if a company is locked in, it may be limited to the provider’s pace of innovation, potentially missing out on superior solutions or features offered by competitors. This can stifle the company’s ability to adapt to changing market demands and maintain a competitive edge.
- Pricing Instability: Cloud providers can alter their pricing models, and a company locked into a single vendor has limited negotiating power. Price increases can significantly impact operational budgets, and there’s no easy way to avoid them. The company may be forced to accept higher costs or reduce services to stay within budget. A practical example is the price increase experienced by some customers of a major cloud provider for certain storage services, leading to significant financial repercussions for those heavily reliant on that provider.
- Compliance and Security Concerns: Vendor lock-in can complicate compliance efforts and increase security risks. If a company’s data and applications are tied to a single provider, it becomes vulnerable to that provider’s security breaches or compliance failures. Moreover, migrating to a different provider to address a compliance issue can be a complex and costly process. For instance, a company operating in a regulated industry might find itself non-compliant with specific regulations if its cloud provider’s infrastructure doesn’t meet the required standards, necessitating a costly migration to a compliant provider.
- Vendor Dependence: Over-reliance on a single vendor creates a dependency that can impact business continuity. If the provider experiences outages, service disruptions, or other issues, the company’s operations can be severely affected. The inability to quickly shift workloads to an alternative provider during an outage can result in significant downtime and loss of revenue.
Strategies to Avoid or Mitigate Vendor Lock-in
Several strategies can be employed to mitigate the risks of vendor lock-in, ensuring greater flexibility and control over cloud resources. These strategies require careful planning and execution but can significantly improve a company’s cloud migration strategy.
- Multi-Cloud Strategy: A multi-cloud strategy involves using services from multiple cloud providers. This approach provides several benefits, including reducing vendor lock-in, improving resilience, and increasing flexibility. By distributing workloads across different providers, a company can avoid being overly dependent on a single vendor. It also enables the company to leverage the strengths of each provider and choose the best services for its specific needs.
- Hybrid Cloud Approach: A hybrid cloud strategy combines public cloud services with on-premises infrastructure or private cloud services. This approach allows companies to retain control over sensitive data and applications while leveraging the scalability and cost-effectiveness of public cloud services. By maintaining some workloads on-premises, companies can reduce their dependence on any single cloud provider.
- Open Source Technologies: Utilizing open-source technologies and platforms reduces vendor lock-in. Open-source solutions are often portable and can be deployed on various cloud platforms. This allows companies to switch providers more easily without significant code changes or retraining efforts. Examples include using containerization technologies like Docker and orchestration tools like Kubernetes, which can run on multiple cloud platforms.
- Standardization and Abstraction: Standardizing infrastructure and using abstraction layers can help to decouple applications from specific cloud provider services. Abstraction layers, such as APIs and middleware, create a layer of insulation between the application and the underlying cloud infrastructure. This makes it easier to migrate applications between different providers without extensive modifications.
- Vendor Selection and Negotiation: Carefully selecting cloud providers and negotiating favorable contracts can help mitigate vendor lock-in risks. Companies should evaluate providers based on factors such as pricing, service level agreements (SLAs), portability options, and support for open standards. Negotiating contracts that include provisions for data portability, interoperability, and exit strategies can also provide greater flexibility.
- Regular Assessment and Monitoring: Regularly assessing the cloud environment and monitoring the usage of cloud services can help identify potential vendor lock-in risks. This includes tracking the use of proprietary services, monitoring pricing trends, and evaluating the portability of applications. By proactively monitoring the environment, companies can identify and address potential lock-in issues before they become critical.
Comparison of Different Vendor Lock-in Scenarios
Vendor lock-in scenarios vary depending on the level of reliance on a specific cloud provider’s services. The following table provides a comparison of different vendor lock-in scenarios.
| Scenario | Description | Impact | Mitigation Strategies |
|---|---|---|---|
| Basic Lock-in | Using a cloud provider for infrastructure services (e.g., compute, storage) with standard technologies. | Moderate switching costs; some dependence on provider’s service availability. | Use open standards; plan for data portability; negotiate service level agreements (SLAs). |
| Intermediate Lock-in | Leveraging cloud provider’s managed services (e.g., databases, message queues) with some vendor-specific configurations. | Higher switching costs; increased dependence on provider’s service offerings; potential for pricing volatility. | Use abstraction layers; design for multi-cloud portability; consider hybrid cloud options. |
| Advanced Lock-in | Extensive use of cloud provider’s proprietary services, custom APIs, and platform-specific features. | High switching costs; significant dependence on provider’s roadmap; potential for limited innovation; significant compliance and security challenges. | Prioritize multi-cloud strategies; invest in platform-agnostic development; establish robust vendor management processes; focus on data portability and interoperability. |
Project Management Risks
Cloud migration projects, inherently complex and multifaceted, are susceptible to a range of project management risks. These risks, if not proactively addressed, can significantly impact project timelines, budgets, and overall success. Effective project management is therefore critical to navigate the inherent uncertainties and complexities of cloud adoption.
Scope Creep and Mitigation
Scope creep, the uncontrolled expansion of a project’s scope after it has begun, is a common project management risk during cloud migration. It manifests as the addition of new features, functionalities, or requirements that were not initially part of the project plan. This can lead to schedule delays, budget overruns, and resource allocation challenges.To mitigate scope creep:
- Establish a clearly defined scope at the outset of the project, including detailed requirements, acceptance criteria, and deliverables.
- Implement a robust change management process that requires formal approval for any scope changes. This process should include impact assessment of the change on the project’s timeline, budget, and resources.
- Regularly review and validate the project scope with stakeholders to ensure alignment and identify potential scope changes early.
- Utilize a phased approach to cloud migration, such as a pilot project, to validate assumptions and refine requirements before a full-scale migration.
Schedule Delays and Management
Schedule delays are another significant project management risk in cloud migration. These delays can stem from various factors, including unforeseen technical challenges, resource constraints, vendor dependencies, and inadequate planning.To address schedule delays:
- Develop a detailed project schedule with realistic timelines, considering potential risks and dependencies.
- Regularly monitor project progress against the schedule and proactively identify potential delays.
- Implement a risk management plan to identify and mitigate potential risks that could impact the schedule.
- Establish clear communication channels and reporting mechanisms to keep stakeholders informed of project progress and any potential delays.
- Employ agile methodologies, which allow for iterative development and flexible response to changing requirements, potentially minimizing the impact of delays.
Resource Management Challenges
Cloud migration projects often require specialized skills and expertise in areas such as cloud architecture, security, and data migration. Resource constraints, including the availability of skilled personnel, can significantly impact project timelines and quality.Strategies for effective resource management include:
- Accurately assess resource needs at the beginning of the project, including both internal and external resources.
- Develop a resource plan that Artikels roles, responsibilities, and required skills.
- Secure resources early in the project lifecycle, considering potential lead times for hiring or vendor selection.
- Provide adequate training and support to project team members to enhance their skills and knowledge.
- Utilize cloud service providers’ expertise and support to augment internal resources.
Communication Breakdown and Mitigation
Effective communication is crucial for the success of any project, and cloud migration is no exception. Communication breakdowns can lead to misunderstandings, delays, and conflicts.Strategies to ensure effective communication:
- Establish a communication plan that defines communication channels, frequency, and target audiences.
- Hold regular project status meetings to keep stakeholders informed of progress, risks, and issues.
- Use clear and concise language to avoid misunderstandings.
- Document all project decisions, changes, and issues.
- Encourage open communication and feedback from all stakeholders.
Project Timeline with Key Milestones and Risk Mitigation
A well-defined project timeline, incorporating key milestones and risk mitigation activities, is essential for managing project management risks.
Phase 1: Assessment and Planning (2-4 weeks)
- Milestone: Cloud migration strategy and detailed project plan finalized.
- Risk Mitigation: Conduct a thorough assessment of existing IT infrastructure and applications. Define clear project scope, objectives, and success criteria.
Phase 2: Proof of Concept (PoC) and Pilot (4-8 weeks)
- Milestone: Successful PoC and Pilot deployment in the cloud environment.
- Risk Mitigation: Select a representative application or workload for the PoC. Address technical challenges. Validate cloud environment performance. Refine migration strategy.
Phase 3: Migration and Implementation (Variable, based on scope)
- Milestone: Completion of data migration and application deployment.
- Risk Mitigation: Employ a phased migration approach. Implement robust data validation and testing procedures. Monitor application performance and address any issues.
Phase 4: Optimization and Governance (Ongoing)
- Milestone: Cloud environment optimized for performance, security, and cost.
- Risk Mitigation: Implement cost optimization strategies. Establish ongoing monitoring and performance management processes. Ensure compliance with regulatory requirements.
Monitoring and Reporting
Continuous monitoring and comprehensive reporting are critical components of a successful cloud migration strategy. They provide real-time insights into the migration process, enabling proactive identification and resolution of risks, ensuring adherence to performance and security standards, and facilitating informed decision-making throughout the lifecycle of cloud operations. Robust monitoring and reporting frameworks allow organizations to maintain control, optimize resource utilization, and demonstrate compliance with relevant regulations.
Importance of Continuous Monitoring and Reporting
The dynamic nature of cloud environments necessitates continuous monitoring and reporting. This approach allows for immediate detection of anomalies, performance bottlenecks, and security vulnerabilities. By analyzing data collected in real-time, organizations can promptly address issues, minimize downtime, and maintain optimal performance. Regular reporting provides stakeholders with a clear understanding of the migration’s progress, risk status, and overall effectiveness. It also supports compliance efforts and facilitates audits.
Key Performance Indicators (KPIs) to Monitor
Monitoring the right KPIs is crucial for evaluating the success of a cloud migration. These metrics should be selected based on the specific goals and objectives of the migration project. A well-defined set of KPIs provides a comprehensive view of performance, security, and cost-effectiveness.
- Performance KPIs: These metrics assess the responsiveness and efficiency of applications and infrastructure.
- Application Response Time: Measures the time taken for an application to respond to user requests. For example, a sudden increase in response time could indicate a performance bottleneck.
- Server CPU Utilization: Tracks the percentage of CPU resources being used by servers. High utilization might necessitate scaling up or optimizing resource allocation.
- Network Latency: Measures the delay in data transmission across the network. High latency can negatively impact application performance.
- Transaction Throughput: Represents the number of transactions processed within a specific timeframe. Monitoring throughput helps identify performance limitations.
- Error Rates: Tracks the frequency of errors within applications and infrastructure. Increased error rates can point to underlying issues.
- Security KPIs: These metrics evaluate the security posture of the cloud environment.
- Number of Security Incidents: Tracks the number of security breaches or incidents. Any increase should trigger investigation and mitigation.
- Vulnerability Scan Results: Monitors the results of vulnerability scans to identify and remediate security flaws.
- Compliance Status: Assesses adherence to security policies and regulatory requirements.
- Unauthorized Access Attempts: Measures the frequency of unauthorized attempts to access resources.
- Data Encryption Status: Tracks the status of data encryption both in transit and at rest.
- Cost KPIs: These metrics monitor cloud spending and resource utilization.
- Cloud Spend: Tracks overall cloud costs.
- Resource Utilization: Monitors the usage of cloud resources, such as compute, storage, and networking.
- Cost per Transaction: Calculates the cost associated with each transaction.
- Cost Optimization Savings: Measures savings achieved through cost optimization efforts.
- Reserved Instance Coverage: Measures the percentage of compute resources covered by reserved instances.
Template for a Risk Report
A well-structured risk report provides a concise overview of identified risks, their assessment, mitigation strategies, and ongoing monitoring activities. The report should be updated regularly to reflect the evolving risk landscape.
| Section | Description | Example |
|---|---|---|
| Risk Identification | Identifies potential risks associated with the cloud migration project. | Risk: Data breach during migration. |
| Risk Assessment | Assesses the likelihood and impact of each identified risk. | Likelihood: Medium, Impact: High, Risk Score: 6 (Likelihood x Impact). |
| Risk Mitigation Strategies | Artikels the planned actions to reduce or eliminate the impact of identified risks. | Implement strong encryption protocols; conduct regular security audits. |
| Mitigation Status | Tracks the progress of implementing the mitigation strategies. | Encryption protocols implemented (100% complete); first security audit scheduled for next week. |
| Monitoring Plan | Defines the specific monitoring activities to track the effectiveness of mitigation strategies. | Monitor for unauthorized access attempts; review audit logs daily. |
| Monitoring Results | Presents the results of the monitoring activities. | No unauthorized access attempts detected in the last week; audit logs reviewed and no anomalies found. |
| Risk Status | Provides an overall assessment of the risk, including its current status (e.g., open, mitigated, closed). | Risk status: Mitigated. |
| Escalation Plan | Defines the escalation process for risks that require immediate attention. | Escalate to the Project Manager and Security Officer immediately. |
| Review Date | Specifies the date of the last review and the date for the next review. | Last review: 2024-03-08; Next review: 2024-03-15. |
Wrap-Up
In conclusion, successful cloud migration hinges on a proactive and comprehensive risk management strategy. By systematically identifying potential threats, employing robust assessment techniques, and implementing targeted mitigation measures, organizations can minimize disruptions, optimize resource utilization, and ensure compliance. The ability to continuously monitor and report on risks is paramount, providing critical insights that enable ongoing optimization and facilitate informed decision-making throughout the cloud migration lifecycle.
Ultimately, a well-executed risk management plan is not merely a safeguard but a catalyst for realizing the full potential of cloud adoption.
FAQ Compilation
What is the most common cause of project delays in cloud migration?
Inadequate planning and scope creep are frequently cited as the primary contributors to project delays. Insufficient upfront assessment of dependencies, resource requirements, and technical complexities often lead to unforeseen challenges and timeline extensions.
How can vendor lock-in be effectively mitigated?
Mitigation strategies include employing multi-cloud strategies, utilizing open-source technologies, and ensuring data portability. Selecting cloud services that adhere to open standards and avoiding proprietary solutions can also reduce the risk.
What are the key considerations for data security during cloud migration?
Data security requires a multi-layered approach, including data encryption both in transit and at rest, robust access controls and identity management, and comprehensive data loss prevention (DLP) measures. Regular security audits and vulnerability assessments are also essential.
How often should risk assessments be conducted during a cloud migration project?
Risk assessments should be conducted at multiple stages of the project lifecycle, including the initial planning phase, before major migration steps, and post-migration to monitor ongoing risks and ensure the effectiveness of mitigation strategies. Continuous monitoring and regular reviews are crucial.