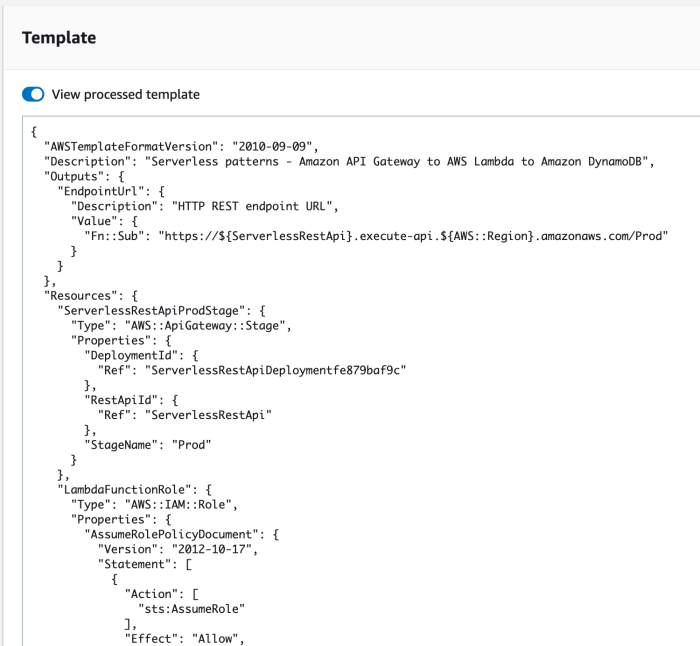
Defining serverless resources within a SAM (Serverless Application Model) template is a cornerstone of modern cloud application development. This process, critical for deploying and managing serverless applications on AWS, allows developers to define infrastructure as code, ensuring consistency, repeatability, and scalability. Understanding the nuances of defining resources like Lambda functions, API Gateways, DynamoDB tables, and S3 buckets is essential for building efficient and robust serverless architectures.
This guide will dissect the key components and best practices for effectively defining these resources within a SAM template.
The SAM template, built upon the foundation of AWS CloudFormation, offers a streamlined approach to defining and deploying serverless applications. It provides a declarative way to specify resources, their configurations, and their interdependencies. This contrasts with imperative approaches, which require manual configuration and scripting. Through the use of the SAM transform, developers can leverage shorthand notations and pre-defined resource types, simplifying the process of defining complex serverless patterns and reducing boilerplate code.
This leads to increased developer productivity and faster time-to-market.
Understanding SAM Templates and Serverless Resources
Serverless application development leverages cloud computing to execute code without the need for managing servers. AWS Serverless Application Model (SAM) simplifies the process of defining, deploying, and managing these serverless applications. SAM uses a declarative approach, allowing developers to define their application’s architecture in a template file, which is then used to provision the necessary AWS resources. This approach enhances efficiency and reduces operational overhead, focusing on business logic rather than infrastructure management.
Fundamental Components of a SAM Template
SAM templates are written in YAML or JSON and serve as blueprints for defining serverless applications. These templates describe the resources needed, their configurations, and their relationships. The core components are essential for orchestrating serverless applications effectively.The key components of a SAM template include:
- AWSTemplateFormatVersion: Specifies the version of the AWS CloudFormation template format. It’s a mandatory field and should be set to “2010-09-09” for SAM templates, indicating compatibility with CloudFormation.
- Transform: This section specifies the SAM transform, which processes the template and expands it into CloudFormation resources. The value is typically “AWS::Serverless-2016-10-31”, enabling SAM-specific resource types and features.
- Description: Provides a human-readable description of the application. This field helps document the purpose and functionality of the application.
- Resources: This is the most critical section, where all the AWS resources that comprise the serverless application are defined. These resources can include Lambda functions, API Gateway APIs, DynamoDB tables, S3 buckets, and more. Each resource definition specifies its type, properties, and configuration details.
- Parameters: Allows the definition of input parameters that can be customized during deployment. These parameters enable reusability and flexibility, allowing the same template to be used with different configurations.
- Outputs: Defines the outputs that are returned after the stack is created or updated. These outputs can include API endpoints, Lambda function ARNs, and other useful information.
A simple example of a SAM template for a Lambda function could look like this (YAML):“`yamlAWSTemplateFormatVersion: ‘2010-09-09’Transform: AWS::Serverless-2016-10-31Description: A simple Lambda functionResources: MyFunction: Type: AWS::Serverless::Function Properties: Handler: index.handler Runtime: nodejs18.x CodeUri: ./src Events: HelloWorld: Type: Api Properties: Path: /hello Method: getOutputs: MyApiEndpoint: Description: “API Gateway endpoint URL for Prod stage” Value: !Sub “https://$ServerlessRestApi.execute-api.$AWS::Region.amazonaws.com/Prod/hello”“`This template defines a Lambda function (“MyFunction”) triggered by an API Gateway (“HelloWorld” event) at the path “/hello”.
The `CodeUri` property specifies the location of the function’s code. The `Outputs` section defines an output for the API endpoint URL.
Serverless Resources Supported by SAM
SAM supports a wide array of serverless resources, allowing developers to build complex and scalable applications. These resources are designed to be managed with minimal operational overhead.The key serverless resources supported by SAM include:
- AWS Lambda: SAM supports the definition and configuration of Lambda functions. This includes specifying the function’s code, runtime, handler, memory allocation, timeout, and execution role. SAM simplifies the deployment of Lambda functions by packaging the code and dependencies.
- Amazon API Gateway: SAM enables the creation and management of API Gateway APIs. This includes defining API endpoints, methods, and integrations with Lambda functions. SAM simplifies the configuration of API Gateway by automatically generating the necessary resources.
- Amazon DynamoDB: SAM supports the definition of DynamoDB tables, including specifying the table’s primary key, attributes, and provisioned throughput. SAM also provides features for creating DynamoDB streams, which can trigger Lambda functions in response to data changes.
- Amazon Simple Storage Service (S3): SAM allows the creation and configuration of S3 buckets, including specifying access permissions and lifecycle policies. SAM simplifies the deployment of applications that store and retrieve data from S3.
- Amazon Simple Queue Service (SQS): SAM supports the creation and management of SQS queues. SAM also provides features for triggering Lambda functions in response to messages in SQS queues.
- Amazon EventBridge: SAM enables the configuration of EventBridge rules, allowing you to trigger Lambda functions in response to events from various AWS services. This allows for event-driven architectures.
- AWS Step Functions: SAM supports the definition of state machines using AWS Step Functions. This includes defining the state machine’s states, transitions, and input/output. Step Functions allows for the orchestration of complex workflows.
These resources can be combined to build a variety of serverless applications, such as web APIs, data processing pipelines, and event-driven systems. For instance, an API could be built using API Gateway to trigger a Lambda function that reads from or writes to a DynamoDB table.
Benefits of Using SAM for Serverless Application Development
SAM offers several benefits that streamline the development, deployment, and management of serverless applications. These benefits contribute to increased developer productivity and reduced operational costs.The advantages of utilizing SAM include:
- Simplified Resource Definition: SAM provides high-level resource types that abstract away the complexities of defining underlying CloudFormation resources. This allows developers to define serverless resources with less boilerplate code. For example, using `AWS::Serverless::Function` simplifies the configuration of a Lambda function compared to using the equivalent CloudFormation resource.
- Local Testing and Debugging: SAM CLI provides tools for locally testing and debugging serverless applications. This enables developers to iterate quickly and identify issues before deploying to the cloud. This local environment simulates the AWS environment, including Lambda function execution and API Gateway interactions.
- Automated Deployment: SAM CLI automates the deployment process, including packaging code, uploading artifacts to S3, and creating or updating CloudFormation stacks. This reduces the manual effort required to deploy applications.
- Infrastructure as Code: SAM promotes the Infrastructure as Code (IaC) approach, where infrastructure is defined in code (the SAM template). This enables version control, collaboration, and automated deployments, improving the reliability and maintainability of applications.
- Faster Development Cycles: By simplifying resource definition, providing local testing capabilities, and automating deployment, SAM accelerates the development cycle. Developers can focus on writing code rather than managing infrastructure.
- Cost Optimization: SAM helps optimize costs by enabling developers to define resources that scale automatically based on demand. This ensures that resources are only used when needed, minimizing unnecessary expenses.
For example, a team using SAM might develop and test a Lambda function locally using the SAM CLI. Once the function is tested, they can deploy it to AWS using the same CLI, which automatically packages the code, creates the necessary infrastructure, and configures the API Gateway. This streamlined process significantly reduces the time and effort required for each iteration of the application.
Defining AWS Lambda Functions in a SAM Template
Defining AWS Lambda functions within a SAM template is a core aspect of serverless application development. SAM templates provide a declarative way to define your Lambda functions, along with their associated resources and configurations. This approach offers benefits such as infrastructure-as-code, version control, and automated deployments. The following sections detail the syntax, configurations, and best practices for defining Lambda functions in a SAM template.
Syntax for Defining a Lambda Function
The syntax for defining a Lambda function in a SAM template utilizes the `AWS::Serverless::Function` resource type. This resource type simplifies the definition process compared to using the raw `AWS::Lambda::Function` resource, providing abstractions for common configurations. The `AWS::Serverless::Function` resource includes properties for specifying the function’s code location, runtime environment, handler, memory allocation, timeout settings, and IAM role. The core structure is based on the YAML or JSON format, following the standard AWS CloudFormation resource declaration.“`yamlResources: MyLambdaFunction: Type: AWS::Serverless::Function Properties: FunctionName: MyLambdaFunction CodeUri: ./src/ Handler: index.handler Runtime: nodejs18.x MemorySize: 128 Timeout: 30 Role: !GetAtt MyLambdaFunctionRole.Arn Events: ApiEvent: Type: Api Properties: Path: /hello Method: get“`This snippet illustrates the basic structure, where `MyLambdaFunction` is the logical ID of the function, and `AWS::Serverless::Function` is the resource type.
The `Properties` section then contains the specific configurations for the Lambda function.
Lambda Function Configurations
Different Lambda function configurations are supported, enabling developers to utilize a variety of programming languages and frameworks. The `Runtime` property within the `Properties` section determines the execution environment for the function.* Python: Python functions can be configured using the `python3.9`, `python3.10`, or `python3.11` runtimes, among others. The `CodeUri` property points to the directory containing the Python code, and the `Handler` property specifies the module and function name that Lambda invokes.
“`yaml MyPythonFunction: Type: AWS::Serverless::Function Properties: FunctionName: MyPythonFunction CodeUri: ./python_code/ Handler: main.handler Runtime: python3.11 MemorySize: 256 Timeout: 60 “`* Node.js: Node.js functions are configured with runtimes like `nodejs16.x` or `nodejs18.x`.
The `CodeUri` points to the directory containing the JavaScript or TypeScript code, and the `Handler` specifies the file and function. “`yaml MyNodeJsFunction: Type: AWS::Serverless::Function Properties: FunctionName: MyNodeJsFunction CodeUri: ./nodejs_code/ Handler: index.handler Runtime: nodejs18.x MemorySize: 128 Timeout: 15 “`* Java: Java functions require the use of Java runtime environments, such as `java11` or `java17`.
The `CodeUri` points to the compiled JAR file or the directory containing the compiled classes, and the `Handler` specifies the fully qualified class name and method. “`yaml MyJavaFunction: Type: AWS::Serverless::Function Properties: FunctionName: MyJavaFunction CodeUri: ./java_code/target/my-app-1.0-SNAPSHOT.jar Handler: com.example.MyHandler::handleRequest Runtime: java17 MemorySize: 512 Timeout: 30 “`These examples illustrate the fundamental differences in configuration based on the selected runtime.
The `Handler` property is critical, as it defines the entry point for the Lambda function’s execution.
Specifying Function Code, Runtime, Handler, and Memory/Timeout Settings
Defining function code, runtime, handler, and memory/timeout settings is a critical part of configuring the Lambda function. These configurations are defined within the `Properties` section of the `AWS::Serverless::Function` resource.* Code: The `CodeUri` property specifies the location of the function’s code. This can be a local directory, an Amazon S3 bucket, or a URL pointing to a code archive.
Using a local directory during development is common, whereas deploying to production typically involves using an S3 bucket. “`yaml CodeUri: ./src/ “`* Runtime: The `Runtime` property dictates the programming language and execution environment. It specifies the runtime environment supported by AWS Lambda, such as `python3.11`, `nodejs18.x`, or `java17`.
“`yaml Runtime: python3.11 “`* Handler: The `Handler` property specifies the entry point of the function, which is the module and function that Lambda invokes when the function is triggered. The format varies depending on the runtime. For Python, it’s the module and function name (`main.handler`); for Node.js, it’s the file and function name (`index.handler`); and for Java, it’s the fully qualified class name and method (`com.example.MyHandler::handleRequest`).
“`yaml Handler: main.handler “`* MemorySize: The `MemorySize` property controls the amount of memory allocated to the function in megabytes. Lambda functions’ performance is correlated with the memory allocated; increasing memory also increases the vCPU available. “`yaml MemorySize: 128 “`* Timeout: The `Timeout` property sets the maximum execution time for the function in seconds.
This prevents functions from running indefinitely and incurring unexpected costs. The default timeout is usually 3 seconds, but it can be increased as needed. “`yaml Timeout: 30 “`Properly configuring these settings is vital for the efficient and cost-effective operation of Lambda functions.
Attaching IAM Roles and Permissions
Attaching IAM roles and permissions is crucial for enabling Lambda functions to interact with other AWS services. The `Role` property within the `AWS::Serverless::Function` resource specifies the IAM role that the function will assume. The IAM role defines the permissions that the function has.* Defining the IAM Role: The IAM role is typically defined as a separate resource within the SAM template.
The role’s `AssumeRolePolicyDocument` specifies which entities can assume the role (in this case, the Lambda service), and the `Policies` section defines the permissions granted to the role. “`yaml MyLambdaFunctionRole: Type: AWS::IAM::Role Properties: AssumeRolePolicyDocument: Version: ‘2012-10-17’ Statement:
Effect
Allow Principal: Service: lambda.amazonaws.com Action: sts:AssumeRole Policies:
PolicyName
MyLambdaPolicy PolicyDocument: Version: ‘2012-10-17’ Statement:
Effect
Allow Action:
logs
CreateLogGroup
logs
CreateLogStream
logs
PutLogEvents Resource: arn:aws:logs:*:*:*
Effect
Allow Action:
s3
GetObject Resource: arn:aws:s3:::my-bucket/* “`* Attaching the Role to the Function: The `Role` property of the `AWS::Serverless::Function` resource is then set to the ARN of the IAM role, typically using the `!GetAtt` intrinsic function. “`yaml MyLambdaFunction: Type: AWS::Serverless::Function Properties: FunctionName: MyLambdaFunction CodeUri: ./src/ Handler: index.handler Runtime: nodejs18.x MemorySize: 128 Timeout: 30 Role: !GetAtt MyLambdaFunctionRole.Arn “`* Granular Permissions: Best practice is to grant only the necessary permissions to the function.
For example, if the function needs to read from an Amazon S3 bucket, the IAM role should only grant `s3:GetObject` permissions on the specific bucket and objects. This follows the principle of least privilege, enhancing security. Using managed policies provided by AWS (e.g., `AWSLambdaBasicExecutionRole`) can simplify initial setup, but custom policies should be used for production environments.The correct configuration of IAM roles and permissions is fundamental for secure and functional Lambda deployments.
Defining API Gateway Endpoints in a SAM Template
API Gateway serves as a crucial component in serverless architectures, providing a managed service for creating, publishing, maintaining, monitoring, and securing APIs at any scale. Within a SAM template, defining API Gateway endpoints allows for the seamless integration of serverless functions with the external world, enabling applications to expose their functionality through HTTP-based APIs. This section will delve into the specifics of defining and configuring API Gateway resources within a SAM template, providing practical examples and explanations to facilitate a comprehensive understanding.
Defining API Gateway Endpoints
Defining API Gateway endpoints in a SAM template involves specifying the API’s structure, including methods, paths, and integrations with backend services, such as Lambda functions. The `AWS::Serverless::Api` resource type is primarily used to define the API Gateway. Within this resource, various properties are configured to define the API’s behavior. For example, the `StageName` property specifies the deployment stage (e.g., “prod”, “dev”), the `DefinitionBody` property (or `DefinitionUri` for external OpenAPI definitions) defines the API’s structure, and the `Cors` property configures Cross-Origin Resource Sharing (CORS) settings.
Additionally, the `AWS::Serverless::HttpApi` resource type can be used to define HTTP APIs, which offer a simplified and cost-effective approach compared to REST APIs, especially for common use cases.The `DefinitionBody` property, when used, typically contains an OpenAPI (formerly known as Swagger) definition that describes the API’s structure. This definition Artikels the API’s paths, methods (e.g., GET, POST, PUT, DELETE), request and response models, and integration configurations.
When using `DefinitionUri`, the OpenAPI definition is stored externally, often in an Amazon S3 bucket. This approach promotes modularity and allows for easier management of the API definition.Here are examples demonstrating different API Gateway configurations within a SAM template, using an HTML table to showcase the methods, paths, and integrations.“`html
| Method | Path | Integration |
|---|---|---|
| GET | /hello | Lambda Function: `HelloWorldFunction` |
| POST | /items | Lambda Function: `CreateItemFunction` |
| GET | /items/id | Lambda Function: `GetItemFunction` |
“`The table illustrates the core components of an API definition. Each row represents an API endpoint. The “Method” column specifies the HTTP method (e.g., GET, POST) used for the request. The “Path” column defines the URL path for the endpoint. The “Integration” column indicates the backend service, which in this case is a Lambda function, that handles the request.
Integrating Lambda Functions with API Gateway Endpoints
Integrating Lambda functions with API Gateway endpoints is achieved through the `AWS::Serverless::Function` and `AWS::Serverless::Api` (or `AWS::Serverless::HttpApi`) resources within the SAM template. The `Events` property within the `AWS::Serverless::Function` resource is used to define the events that trigger the Lambda function’s execution. For API Gateway integrations, the `Api` event type is employed. This event type allows you to specify the API Gateway method, path, and API resource that triggers the function.The `AWS::Serverless::Api` resource defines the API Gateway itself, including the routes and integrations.
The `DefinitionBody` property (or `DefinitionUri`) contains the OpenAPI definition, which specifies the API’s structure and how requests are routed to the backend Lambda functions. Within the OpenAPI definition, each path and method are associated with an `x-amazon-apigateway-integration` extension that defines the integration with the Lambda function. This extension specifies the type of integration (e.g., AWS_PROXY for Lambda proxy integration), the Lambda function’s ARN, and other relevant settings.Here is an example of integrating a Lambda function with an API Gateway endpoint using the `Api` event type within the `AWS::Serverless::Function` resource:“`yamlResources: HelloWorldFunction: Type: AWS::Serverless::Function Properties: Handler: index.handler Runtime: nodejs18.x CodeUri: ./hello-world Events: HelloWorldApi: Type: Api Properties: Path: /hello Method: GET“`In this example, the `HelloWorldFunction` Lambda function is triggered by a GET request to the `/hello` path.
The `Type: Api` specifies that this event is related to API Gateway, and the `Properties` define the path and method associated with the event. The SAM CLI automatically creates the necessary API Gateway resources and integrations based on this configuration.
Defining API Gateway Methods, Paths, and Request/Response Models
Defining API Gateway methods, paths, and request/response models is done primarily through the OpenAPI definition provided in the `DefinitionBody` property (or through an external definition specified in `DefinitionUri`) of the `AWS::Serverless::Api` resource.The OpenAPI definition uses the `paths` section to define the API’s paths and methods. Each path is a key in the `paths` object, and its value is another object that defines the methods (e.g., GET, POST, PUT, DELETE) supported for that path.
Within each method, you specify the request and response models, which define the structure of the data that the API expects and returns.For example, consider a POST method for creating an item at the `/items` path. The OpenAPI definition might include:“`yamlpaths: /items: post: summary: Create a new item requestBody: required: true content: application/json: schema: $ref: ‘#/components/schemas/Item’ responses: ‘201’: description: Item created successfully content: application/json: schema: $ref: ‘#/components/schemas/Item’“`In this snippet, the `requestBody` section defines the expected request body for the POST method.
The `content` field specifies the media type (`application/json`), and the `schema` field references a schema definition (`#/components/schemas/Item`) that defines the structure of the item data. The `responses` section defines the possible responses, including their status codes and content. The example includes a `201` (Created) response, indicating a successful creation. The `content` field specifies the media type and the schema for the response body.The `components/schemas` section within the OpenAPI definition defines the data models used in the request and response bodies.
This section allows you to define the structure of objects, including their properties, data types, and other constraints.
Defining DynamoDB Tables in a SAM Template
DynamoDB is a key-value and document database that delivers single-digit millisecond performance at any scale. Defining DynamoDB tables within a SAM template allows for infrastructure-as-code, enabling automated provisioning and management of these resources alongside other serverless components. This approach ensures consistency, repeatability, and version control for database configurations.
Syntax for Defining DynamoDB Tables in a SAM Template
The syntax for defining a DynamoDB table in a SAM template utilizes the `AWS::DynamoDB::Table` resource type. This resource definition includes various properties that configure the table’s attributes, schema, provisioned capacity, and indexing. The core structure involves specifying the table’s attributes, which define the data model, and the primary key, which uniquely identifies each item.“`yamlResources: MyDynamoDBTable: Type: AWS::DynamoDB::Table Properties: TableName: MyTable AttributeDefinitions:
AttributeName
“Id” AttributeType: “S”
AttributeName
“SortKey” AttributeType: “N” KeySchema:
AttributeName
“Id” KeyType: “HASH”
AttributeName
“SortKey” KeyType: “RANGE” ProvisionedThroughput: ReadCapacityUnits: 5 WriteCapacityUnits: 5“`
Different DynamoDB Table Configurations
DynamoDB tables offer flexibility in their configuration, accommodating various data models and access patterns. Different configurations can be defined, and each is appropriate for different use cases.
- Primary Keys: A primary key uniquely identifies each item in a DynamoDB table. It can be a simple key (partition key/hash key) or a composite key (partition key and sort key/range key). The choice of primary key impacts query performance and data organization.
- Indexes: Indexes allow for efficient querying of data based on attributes other than the primary key. DynamoDB supports local secondary indexes (LSIs) and global secondary indexes (GSIs). LSIs are scoped to a single table, while GSIs are independent tables that can be queried across the entire table.
- Provisioned Capacity: Provisioned capacity defines the read and write capacity units (RCUs and WCUs) allocated to a table. Proper capacity planning is crucial to avoid throttling and ensure sufficient throughput for the application’s needs. Over-provisioning can lead to unnecessary costs.
Configuring Table Attributes, Read/Write Capacity, and Global Secondary Indexes (GSIs)
Configuration of these aspects is critical to the performance and cost-effectiveness of the DynamoDB table. Each configuration element impacts the operational characteristics of the table.
- Table Attributes: `AttributeDefinitions` within the SAM template define the attributes that will be stored in the table, including the attribute name and data type (e.g., String, Number, Boolean, Binary, etc.). The `KeySchema` defines the primary key, specifying the `AttributeName` and `KeyType` (HASH or RANGE). The `HASH` key serves as the partition key, and the `RANGE` key (if used) is the sort key.
- Read/Write Capacity: `ProvisionedThroughput` defines the table’s read and write capacity. `ReadCapacityUnits` (RCUs) determine the number of strongly consistent reads per second, while `WriteCapacityUnits` (WCUs) determine the number of writes per second. For on-demand capacity mode, this section is omitted, and DynamoDB automatically scales the capacity. Choosing the correct capacity mode is crucial to optimize costs and performance.
- Global Secondary Indexes (GSIs): GSIs are defined within the `GlobalSecondaryIndexes` property. Each GSI requires its own `IndexName`, `KeySchema`, `Projection`, and `ProvisionedThroughput` (or capacity mode). The `Projection` specifies which attributes from the base table are copied into the index. GSIs are invaluable for querying data based on attributes other than the primary key, enabling flexible data access patterns. For example:
“`yaml
GlobalSecondaryIndexes:-IndexName: “SecondaryIndex”
KeySchema:-AttributeName: “SecondaryKey”
KeyType: “HASH”
Projection:
ProjectionType: “ALL”
ProvisionedThroughput:
ReadCapacityUnits: 5
WriteCapacityUnits: 5
“`
Connecting Lambda Functions to DynamoDB Tables
Connecting Lambda functions to DynamoDB tables involves several steps, from granting permissions to configuring environment variables. This integration allows Lambda functions to interact with the database, enabling read and write operations.
- IAM Permissions: Grant the Lambda function the necessary IAM permissions to access the DynamoDB table. This is typically done using an IAM role attached to the Lambda function. The role must have the `dynamodb:GetItem`, `dynamodb:PutItem`, `dynamodb:UpdateItem`, `dynamodb:DeleteItem`, and `dynamodb:Scan` actions, or appropriate restricted permissions, on the specific DynamoDB table. For example:“`yaml MyLambdaFunction: Type: AWS::Serverless::Function Properties: FunctionName: MyLambdaFunction Handler: index.handler Runtime: nodejs18.x Role: !GetAtt MyLambdaFunctionRole.Arn Environment: Variables: TABLE_NAME: !Ref MyDynamoDBTable“““yaml MyLambdaFunctionRole: Type: AWS::IAM::Role Properties: AssumeRolePolicyDocument: Version: “2012-10-17” Statement:
Effect
“Allow” Principal: Service: “lambda.amazonaws.com” Action: “sts:AssumeRole” Policies:
PolicyName
“DynamoDBAccess” PolicyDocument: Version: “2012-10-17” Statement:
Effect
“Allow” Action:
“dynamodb
GetItem”
“dynamodb
PutItem”
“dynamodb
UpdateItem”
“dynamodb
DeleteItem”
“dynamodb
Scan” Resource: !GetAtt MyDynamoDBTable.Arn“`
- Environment Variables: Configure the Lambda function to know the name or ARN of the DynamoDB table. This is typically done using environment variables within the SAM template. This approach makes the table name easily accessible to the function code.
- Code Implementation: Within the Lambda function code (e.g., using the AWS SDK for JavaScript), use the environment variable to access the DynamoDB table. Create an instance of the DynamoDB client, and then use methods like `getItem`, `putItem`, `updateItem`, and `deleteItem` to interact with the table. Error handling and proper input validation are critical for robust code.
- Testing and Deployment: Deploy the SAM template and thoroughly test the integration. Verify that the Lambda function can successfully read from and write to the DynamoDB table. Use logging and monitoring to track function execution and identify any issues.
Defining S3 Buckets and Events in a SAM Template
This section details the configuration of Amazon Simple Storage Service (S3) buckets and their integration with AWS Lambda functions within a SAM template. Properly configuring S3 buckets and events is crucial for building serverless applications that can process data uploaded to S3, trigger workflows, and manage storage effectively. This includes defining bucket properties, access controls, lifecycle rules, and event notifications.
Defining S3 Buckets in a SAM Template
S3 buckets are defined in a SAM template using the `AWS::S3::Bucket` resource type. The definition allows specifying various properties that control the bucket’s behavior and characteristics. These properties are declared within the `Properties` section of the resource definition.To create an S3 bucket named “my-serverless-bucket”, the following SAM template snippet can be used:“`yamlResources: MyS3Bucket: Type: AWS::S3::Bucket Properties: BucketName: my-serverless-bucket“`This simple definition creates a bucket with the specified name.
However, more complex configurations are often required.
Examples of S3 Bucket Configurations
Configuring S3 buckets involves setting several properties to meet specific application requirements. The following examples illustrate various configurations.* Bucket Name: As demonstrated above, the `BucketName` property allows setting a custom name for the bucket. If this property is omitted, CloudFormation generates a unique name.* Access Control: Access control can be managed using the `AccessControl` property. This property accepts values such as “Private”, “PublicRead”, “PublicReadWrite”, “AuthenticatedRead”, and more.
Setting “Private” is generally recommended by default for security reasons.“`yamlResources: MyS3Bucket: Type: AWS::S3::Bucket Properties: BucketName: my-serverless-bucket AccessControl: Private“`* Lifecycle Rules: Lifecycle rules automatically manage object storage over time. They can be used to transition objects to different storage classes (e.g., from Standard to Infrequent Access or Glacier) or delete objects after a specified period.“`yamlResources: MyS3Bucket: Type: AWS::S3::Bucket Properties: BucketName: my-serverless-bucket LifecycleConfiguration: Rules:
Id
ExpireOldObjects Status: Enabled Expiration: Days: 365 Filter: Prefix: “logs/”“`This example defines a lifecycle rule that expires objects with the “logs/” prefix after 365 days.* Versioning: Bucket versioning enables the preservation of multiple versions of objects in a bucket, which protects against accidental deletion or modification.“`yamlResources: MyS3Bucket: Type: AWS::S3::Bucket Properties: BucketName: my-serverless-bucket VersioningConfiguration: Status: Enabled“`* Encryption: S3 buckets can be configured to encrypt objects using server-side encryption.“`yamlResources: MyS3Bucket: Type: AWS::S3::Bucket Properties: BucketName: my-serverless-bucket BucketEncryption: ServerSideEncryptionConfiguration:
ServerSideEncryptionByDefault
SSEAlgorithm: AES256“`This configuration uses AES256 encryption.
Configuring S3 Event Notifications to Trigger Lambda Functions
S3 event notifications enable Lambda functions to be triggered automatically when specific events occur in an S3 bucket, such as object creation, deletion, or modification. These events are configured using the `Events` property within the `AWS::S3::Bucket` resource, referencing the Lambda function using the `Target` property.“`yamlResources: MyS3Bucket: Type: AWS::S3::Bucket Properties: BucketName: my-serverless-bucket NotificationConfiguration: LambdaConfigurations:
Event
s3:ObjectCreated:* Function: !GetAtt MyLambdaFunction.Arn Filter: S3Key: Rules:
Name
prefix Value: “images/”“`In this example:* `NotificationConfiguration` defines the event triggers. `LambdaConfigurations` specifies a Lambda function trigger.
`Event
s3:ObjectCreated:*` triggers the Lambda function for all object creation events.
`Function
!GetAtt MyLambdaFunction.Arn` references the ARN of the Lambda function.
- `Filter` is used to filter the events based on the S3 key prefix (e.g., “images/”).
This configuration will trigger the specified Lambda function whenever a new object is created in the “images/” folder of the bucket.
Procedure for Defining S3 Bucket Policies
S3 bucket policies control access to the bucket and its contents. They define which principals (users, roles, or services) are allowed to perform specific actions on the bucket. Defining bucket policies is a critical security measure to ensure data confidentiality and integrity.To define an S3 bucket policy within a SAM template, the `AWS::S3::BucketPolicy` resource type is used. This resource takes a `Bucket` property, which specifies the bucket to which the policy applies, and a `PolicyDocument` property, which defines the policy itself.The following SAM template snippet illustrates the creation of a bucket policy:“`yamlResources: MyS3Bucket: Type: AWS::S3::Bucket Properties: BucketName: my-serverless-bucket MyS3BucketPolicy: Type: AWS::S3::BucketPolicy Properties: Bucket: !Ref MyS3Bucket PolicyDocument: Statement:
Effect
Allow Principal: AWS: !GetAtt MyLambdaFunction.Arn Action:
s3
GetObject Resource: !Join – “”
“arn
aws:s3:::”
!Ref MyS3Bucket
– “/*”“`In this example:* `MyS3BucketPolicy` defines the policy resource.
`Bucket
!Ref MyS3Bucket` links the policy to the `MyS3Bucket` resource. `PolicyDocument` contains the policy definition.
`Effect
Allow` specifies that the policy allows the action.
`Principal
AWS: !GetAtt MyLambdaFunction.Arn` grants access to the Lambda function’s ARN.
`Action
s3:GetObject` allows the principal to perform the `GetObject` action.
`Resource
!Join` specifies the resource the policy applies to (all objects in the bucket).
This policy grants the specified Lambda function permission to retrieve objects from the S3 bucket. Proper configuration of bucket policies is essential for securing S3 resources.
Defining EventBridge Rules in a SAM Template
Defining EventBridge rules within a SAM template allows for the creation of serverless event-driven architectures. This facilitates the decoupling of services and enables systems to react to events in real-time. SAM simplifies the process of defining these rules, their event patterns, and their targets, such as Lambda functions or other AWS services.
Defining EventBridge Rules
The process of defining EventBridge rules in a SAM template involves specifying the `AWS::Events::Rule` resource type. This resource defines the rule’s event pattern, which dictates the types of events that will trigger the rule, and the targets, which are the resources that will be invoked when the rule is triggered. Key properties to configure include `EventBusName`, `EventPattern`, `State`, and `Targets`.
The `EventBusName` property allows for the selection of a specific EventBridge event bus. The `EventPattern` property defines the structure and content of the events the rule should match. The `State` property enables or disables the rule. The `Targets` property lists the resources to be invoked when an event matches the pattern.
EventBridge Rule Configurations
EventBridge rules can be configured with various event patterns and targets. The following examples illustrate common configurations:
- Event Pattern: A rule that triggers on all S3 object creation events in a specific bucket. This is a common use case for triggering actions in response to file uploads.
EventPattern: source: -aws.s3 detail-type: -Object Created detail: bucket: name: -my-s3-bucket
- Target: A rule that triggers a Lambda function. This demonstrates the fundamental concept of event-driven architectures.
Targets: -Arn: !GetAtt MyLambdaFunction.Arn Id: MyLambdaFunctionTarget
- Event Pattern: A rule that triggers on specific CloudWatch alarm state changes. This enables automated responses to infrastructure health issues.
EventPattern: source: -aws.cloudwatch detail-type: -AWS CloudWatch Alarm State Change detail: alarmName: -MyHighCPUAlarm newStateValue: -ALARM
- Target: A rule that triggers an SNS topic. This enables notifications based on events.
Targets: -Arn: !Ref MySNSTopic Id: MySNSTopicTarget
Triggering Lambda Functions with EventBridge Events
Triggering Lambda functions based on EventBridge events involves configuring the `Targets` property of the `AWS::Events::Rule` resource to point to the Lambda function. The event data from the matched event is then passed to the Lambda function as input. Within the Lambda function, developers can parse the event data to extract relevant information and perform necessary actions. For example, a Lambda function triggered by an S3 object creation event would receive details about the created object, such as its key, bucket, and size.
This data can be used to process the object, such as resizing an image or extracting text from a document.
Configuring EventBridge Event Buses
EventBridge event buses are logical containers for events. There are two primary types: the default event bus and custom event buses. SAM templates can define custom event buses using the `AWS::Events::EventBus` resource. The `Name` property specifies the name of the event bus. Rules can then be configured to use a specific event bus via the `EventBusName` property of the `AWS::Events::Rule` resource.
This allows for organizing events into different categories or namespaces. This separation aids in modularity and security, allowing you to control access and permissions at the event bus level.
Defining IAM Roles and Policies in a SAM Template
IAM roles and policies are fundamental to securing serverless applications. They define the permissions that AWS resources, such as Lambda functions, have to access other AWS services. Properly configured IAM roles and policies are critical for the least privilege principle, enhancing security and preventing unauthorized access. SAM templates provide a declarative way to define and manage these IAM resources alongside other components of a serverless application.
Defining IAM Role and Policy Configurations for Lambda Functions
IAM roles and policies are defined within a SAM template using the `AWS::IAM::Role` and `AWS::IAM::Policy` resource types. The `AWS::IAM::Role` resource defines the role itself, including the trust relationship that specifies which entities are allowed to assume the role. The `AWS::IAM::Policy` resource defines the permissions granted to the role, specifying which actions the role can perform on which resources.
- IAM Role Definition: The `AWS::IAM::Role` resource requires properties such as `AssumeRolePolicyDocument`, `Policies`, and `ManagedPolicyArns`. The `AssumeRolePolicyDocument` specifies who can assume the role. The `Policies` property allows inline policy definitions, while `ManagedPolicyArns` allows the attachment of existing managed policies.
- IAM Policy Definition: IAM policies are defined using JSON documents that specify the allowed actions and resources. These policies are attached to IAM roles, granting the role the permissions defined in the policy. Policies are structured using `Version`, `Statement`, `Effect`, `Action`, and `Resource` elements.
- Example: A Lambda function that reads data from a DynamoDB table and logs to CloudWatch would require an IAM role with permissions for both. This can be achieved by defining an IAM role with an `AssumeRolePolicyDocument` that allows the Lambda service to assume the role, and policies granting access to DynamoDB and CloudWatch.
Consider a simple example. Suppose a Lambda function needs to access an S3 bucket named “my-s3-bucket”. The SAM template would define an IAM role for the Lambda function and attach a policy granting access to that bucket. The `AssumeRolePolicyDocument` would allow the Lambda service to assume the role. The policy would specify the `s3:GetObject` action for the “my-s3-bucket” bucket.
Granting Permissions to Access Other AWS Resources
Granting permissions to access other AWS resources involves defining IAM policies that allow specific actions on those resources. This is done by creating policy documents that specify the allowed actions (`Action`), the target resources (`Resource`), and the effect (`Effect`, typically “Allow”).
- Action Specification: The `Action` element specifies the API actions that the role is permitted to perform. This can be a single action (e.g., `s3:GetObject`) or a list of actions (e.g., `s3:*` for all S3 actions). Using specific actions is generally recommended for better security.
- Resource Specification: The `Resource` element specifies the AWS resources to which the actions apply. This can be a specific resource (e.g., `arn:aws:s3:::my-bucket/my-object.txt`) or a wildcard (e.g., `arn:aws:s3:::my-bucket/*`).
- Effect Specification: The `Effect` element specifies whether the permissions allow or deny access. The value is either “Allow” or “Deny”.
For example, a Lambda function that needs to write to a DynamoDB table would require a policy that allows the `dynamodb:PutItem` action on that table. Similarly, if the function needs to publish messages to an SNS topic, the policy would allow the `sns:Publish` action on the SNS topic’s ARN. When accessing resources across different AWS accounts, the policy must include the account ID in the resource ARN and the role’s `AssumeRolePolicyDocument` needs to be adjusted to allow the other account to assume the role.
Managing IAM Role Trust Relationships
Managing IAM role trust relationships is critical for controlling who can assume the role and, therefore, what permissions the role has. The `AssumeRolePolicyDocument` defines this trust relationship.
- `AssumeRolePolicyDocument` Structure: The `AssumeRolePolicyDocument` is a JSON document that specifies the principals (who) that are allowed to assume the role. It typically includes an `Effect` (“Allow” or “Deny”), `Principal` (the entities allowed to assume the role, such as AWS services or other AWS accounts), and `Action` (usually `sts:AssumeRole`).
- Service-Based Trust Relationships: For Lambda functions, the `Principal` usually specifies the `lambda.amazonaws.com` service. This allows the Lambda service to assume the role on behalf of the function.
- Account-Based Trust Relationships: To allow another AWS account to assume the role, the `Principal` would specify the account ID. This is useful for cross-account access.
- Best Practices: It’s essential to limit the scope of the trust relationship to the necessary entities and to regularly review and update trust policies to ensure they align with the principle of least privilege.
The `AssumeRolePolicyDocument` is crucial for security. Consider a scenario where a Lambda function needs to be triggered by an API Gateway. The `AssumeRolePolicyDocument` would specify that the API Gateway service (`apigateway.amazonaws.com`) is allowed to assume the role. This setup ensures that only the API Gateway can trigger the Lambda function, enhancing security. Conversely, if the Lambda function needs to be triggered by an EventBridge rule, the `Principal` would specify `events.amazonaws.com`.
Parameterizing SAM Templates for Reusability
Parameterizing AWS SAM templates is a critical practice for creating reusable and adaptable infrastructure-as-code. By defining parameters, you can customize deployments for different environments, use cases, or teams without modifying the core template. This approach promotes code reusability, reduces errors, and streamlines the deployment process. It allows for greater flexibility in managing serverless applications across various stages of development and operation.
Using Parameters in SAM Templates to Customize Deployments
Parameters enable you to provide values to your SAM template during deployment. This allows you to tailor the resources created to specific needs without changing the underlying template structure. The values supplied via parameters can affect various aspects of your serverless application, such as the resource names, memory allocation for Lambda functions, API Gateway stage names, and more. This modularity is fundamental to efficient infrastructure management.
Defining and Using Parameters for Different Resources
Parameters are defined within the `Parameters` section of a SAM template. Each parameter has a unique logical ID (name), type, and optional properties like a default value, allowed values, and description.“`yamlParameters: EnvironmentName: Type: String Default: dev AllowedValues: – dev – staging – prod Description: The environment to deploy to (dev, staging, prod) LambdaMemorySize: Type: Number Default: 128 MinValue: 128 MaxValue: 3008 Description: The memory allocated to the Lambda function in MB.“`This example defines two parameters: `EnvironmentName` and `LambdaMemorySize`.
The `EnvironmentName` parameter allows selection of the deployment environment, restricting choices to `dev`, `staging`, or `prod`. `LambdaMemorySize` allows the user to specify the memory allocation for a Lambda function, with constraints on minimum and maximum values.To use these parameters within your resource definitions, you use the `!Ref` intrinsic function to reference the parameter’s logical ID.“`yamlResources: MyLambdaFunction: Type: AWS::Serverless::Function Properties: FunctionName: !Sub “my-function-$EnvironmentName” MemorySize: !Ref LambdaMemorySize Handler: index.handler Runtime: nodejs18.x CodeUri: ./src“`In this example, the Lambda function’s name is dynamically generated using the `EnvironmentName` parameter, and the `MemorySize` property is set based on the value of the `LambdaMemorySize` parameter.
This ensures that resource names and configurations adapt to the environment and resource requirements specified during deployment.
Using Parameter Overrides During Deployment
Parameter overrides are provided when you deploy the SAM template using the AWS CLI or other deployment tools. You can override the default values or provide specific values for each parameter. This flexibility is crucial for tailoring the deployment to different scenarios.The AWS CLI command for deploying a SAM template with parameter overrides is:“`bashsam deploy –template-file template.yaml –stack-name my-serverless-app –parameter-overrides ParameterKey=EnvironmentName,ParameterValue=staging ParameterKey=LambdaMemorySize,ParameterValue=256“`In this command, `–parameter-overrides` specifies the parameters to override and their corresponding values.
The `ParameterKey` is the logical ID of the parameter defined in the template, and `ParameterValue` is the value to assign to that parameter during deployment. This example sets `EnvironmentName` to `staging` and `LambdaMemorySize` to `256` for the deployment.
Defining Parameter Types and Constraints
Defining the parameter types and constraints is essential for ensuring the integrity and usability of your SAM templates. SAM supports various parameter types, including `String`, `Number`, `List
- String: Represents a string value. You can use constraints like `AllowedValues` to restrict the accepted values or `MaxLength` and `MinLength` to limit the string’s length.
- Number: Represents a numerical value. Constraints like `MinValue` and `MaxValue` can be used to define the acceptable range.
- List<Number>: Represents a list of numerical values.
- CommaDelimitedList: Represents a list of comma-separated strings.
- AWS::SSM::Parameter::Value<String>: Retrieves a value from AWS Systems Manager Parameter Store. This is useful for securely storing sensitive information like database passwords or API keys.
“`yamlParameters: InstanceType: Type: String Default: t2.micro AllowedValues:
t2.micro
t2.small
t2.medium
Description: The EC2 instance type. DatabasePort: Type: Number Default: 3306 MinValue: 1 MaxValue: 65535 Description: The database port number.“`In this example, the `InstanceType` parameter uses `AllowedValues` to limit the available instance types, while `DatabasePort` uses `MinValue` and `MaxValue` to validate the port number.
These constraints ensure that only valid values are used during deployment, preventing misconfigurations and errors. Using `AWS::SSM::Parameter::Value
Defining and Using SAM Transform
The AWS Serverless Application Model (SAM) transform is a crucial component within a SAM template. Its primary function is to simplify the definition of serverless resources by providing shorthand syntax and abstractions over the underlying AWS CloudFormation resources. This simplifies template authoring, reduces boilerplate code, and promotes a more concise and readable approach to defining serverless applications.
Purpose of the SAM Transform
The SAM transform acts as a preprocessor for CloudFormation templates. When a template containing the SAM transform is deployed, CloudFormation uses the transform to expand the shorthand SAM resource definitions into their full CloudFormation equivalents. This process offers several benefits:* Abstraction: It hides the complexities of underlying CloudFormation resources, allowing developers to focus on the application logic.
Conciseness
It reduces the amount of code required to define serverless resources.
Readability
It makes templates easier to understand and maintain.
Validation
The transform validates the SAM-specific syntax, providing early feedback on potential errors.
Portability
SAM templates are more portable as they abstract away some of the underlying AWS resource specifics.
Examples of Simplification through SAM Transform
The SAM transform significantly simplifies resource definitions. For example, defining a Lambda function using CloudFormation directly requires specifying details like the handler, runtime, memory size, and execution role. SAM simplifies this considerably.Consider the following comparison:* CloudFormation (Direct): “`yaml Resources: MyFunction: Type: AWS::Lambda::Function Properties: FunctionName: MyFunction Handler: index.handler Runtime: nodejs18.x MemorySize: 128 Timeout: 30 Role: !GetAtt MyLambdaRole.Arn “`* SAM (with Transform): “`yaml Resources: MyFunction: Type: AWS::Serverless::Function Properties: FunctionName: MyFunction Handler: index.handler Runtime: nodejs18.x MemorySize: 128 Timeout: 30 “` Notice that the SAM template is more concise.
The `AWS::Serverless::Function` resource type automatically handles the creation of an execution role if one isn’t specified directly, simplifying the setup. Another example is the definition of an API Gateway endpoint. With CloudFormation, this involves defining multiple resources (API Gateway REST API, Resource, Method, Integration, etc.). SAM collapses this into a single `AWS::Serverless::Api` resource, streamlining the process. For instance:
CloudFormation (API Gateway)
This would involve several resources and configurations to set up a simple GET endpoint.
SAM (API Gateway)
SAM allows defining an API endpoint directly within the Lambda function’s definition using the `Events` property. “`yaml Resources: MyFunction: Type: AWS::Serverless::Function Properties: Handler: index.handler Runtime: nodejs18.x Events: MyApi: Type: Api Properties: Path: /hello Method: get “` This significantly reduces the complexity and lines of code required.
Handling Resource Shorthand with SAM Transform
The SAM transform utilizes a resource shorthand to reduce the amount of code required to define serverless resources. This shorthand is implemented through the use of custom resource types prefixed with `AWS::Serverless::`. When the transform encounters these types, it expands them into their corresponding CloudFormation resource equivalents.The process of expanding the shorthand can be broken down as follows:
1. Template Parsing
The CloudFormation service parses the SAM template.
2. Transform Detection
The `Transform: AWS::Serverless-2016-10-31` directive in the template header signals the use of the SAM transform.
3. Resource Type Identification
The transform identifies resources with types starting with `AWS::Serverless::`.
4. Expansion
The transform replaces these shorthand resource definitions with their expanded CloudFormation equivalents. This includes adding default values, creating implicit resources (like execution roles), and configuring integrations.
5. CloudFormation Processing
The expanded CloudFormation template is then processed by the CloudFormation service to create the serverless application stack.For example, when you define an `AWS::Serverless::Function` resource, the transform automatically creates an IAM role with the necessary permissions for the Lambda function to execute. It also sets up the necessary configurations for logging and monitoring. The SAM transform handles this expansion internally, abstracting these details from the developer.
Using the Transform for Simplifying Common Serverless Patterns
The SAM transform simplifies the implementation of common serverless patterns.* Lambda Function with API Gateway: The `AWS::Serverless::Function` resource, when used with the `Events` property of type `Api`, automatically creates an API Gateway endpoint and configures the necessary integration with the Lambda function. For example, you can define an API endpoint with the following: “`yaml Resources: MyFunction: Type: AWS::Serverless::Function Properties: Handler: index.handler Runtime: nodejs18.x Events: MyApi: Type: Api Properties: Path: /hello Method: get “`* Lambda Function Triggered by S3 Events: The `AWS::Serverless::Function` resource can be configured to trigger on S3 events using the `Events` property of type `S3`.
This simplifies the configuration of event triggers. “`yaml Resources: MyFunction: Type: AWS::Serverless::Function Properties: Handler: index.handler Runtime: nodejs18.x Events: MyS3Event: Type: S3 Properties: Bucket: !Ref MyBucket Events:
s3
ObjectCreated:* “`* DynamoDB Table with Lambda Triggers: SAM facilitates the creation of DynamoDB tables and the configuration of Lambda function triggers for various DynamoDB events. For example: “`yaml Resources: MyTable: Type: AWS::Serverless::SimpleTable Properties: PrimaryKey: Name: id Type: String TableName: MyTable MyFunction: Type: AWS::Serverless::Function Properties: Handler: index.handler Runtime: nodejs18.x Events: MyStreamEvent: Type: DynamoDB Properties: Stream: !GetAtt MyTable.StreamArn BatchSize: 100 “` This automatically configures the Lambda function to be invoked whenever data is created, updated, or deleted in the specified DynamoDB table.By utilizing these simplified resource definitions and the automatic configuration capabilities of the SAM transform, developers can rapidly prototype, deploy, and manage serverless applications without being bogged down in the complexities of low-level CloudFormation configurations.
This also helps to ensure consistency and reduces the likelihood of configuration errors.
Best Practices for Structuring SAM Templates
Organizing and structuring SAM templates effectively is crucial for readability, maintainability, and collaborative development. A well-structured template minimizes errors, simplifies debugging, and allows for easier updates and modifications as your serverless application evolves. Adhering to best practices ensures that your templates remain manageable, even as the complexity of your serverless infrastructure increases.
Logical IDs and Resource Naming Conventions
Consistent use of logical IDs and resource naming conventions is fundamental for template organization. Logical IDs, which are the identifiers used within the SAM template to reference resources, should be descriptive and easily understandable. Resource names, on the other hand, are the actual names assigned to AWS resources and are typically used for external identification and access.
- Descriptive Logical IDs: Logical IDs should clearly indicate the resource’s purpose. For example, instead of using `MyLambdaFunction`, use `ProcessOrdersLambdaFunction` or `UserDataIngestionLambdaFunction`. This immediately clarifies the function’s role within the application.
- Consistent Resource Naming: Establish a consistent naming scheme for your resources. This might involve prefixes and suffixes based on the resource type, environment, or application component. For example, `dev-orders-api-gateway` for an API Gateway in the development environment, or `prod-user-profile-dynamodb` for a DynamoDB table in production.
- Use of Parameters in Resource Names: Leverage SAM template parameters to create dynamic resource names. This allows you to customize resource names based on environment, application version, or other variables, making your templates more flexible. For instance:
Parameters:
Environment:
Type: String
Default: dev
AllowedValues: [dev, staging, prod]
Resource:
Type: AWS::Lambda::Function
Properties:
FunctionName: !Sub "$Environment-MyFunction"
In this example, the function name will be prefixed with the environment name (e.g., `dev-MyFunction`).
- Avoid Hardcoding Values: Minimize the use of hardcoded values in your template. Instead, utilize parameters and intrinsic functions like `!Sub` and `!Ref` to make your template more adaptable. This also prevents unintended side effects.
Modularizing SAM Templates with Nested Stacks
Nested stacks provide a powerful mechanism for modularizing SAM templates. This approach involves breaking down a large template into smaller, more manageable units, each representing a specific component or feature of your application. This improves code reusability, simplifies maintenance, and allows for independent deployments of specific parts of your infrastructure.
- Component-Based Architecture: Design your application using a component-based architecture. Each component, such as a user authentication system, an order processing service, or a data ingestion pipeline, can be represented by a separate nested stack.
- Template Reusability: Nested stacks enable template reusability. A stack defining a common component, like a VPC configuration or a logging setup, can be used across multiple applications.
- Simplified Maintenance: Smaller, focused templates are easier to understand, debug, and maintain. Changes to a specific component only affect its corresponding nested stack, minimizing the risk of unintended consequences.
- Independent Deployment: You can deploy or update individual nested stacks without affecting other parts of your application. This allows for faster iteration and more controlled deployments.
- Example of Nested Stacks: Consider a serverless e-commerce application. You might create the following nested stacks:
- `vpc-stack.yaml`: Defines the VPC, subnets, and security groups.
- `database-stack.yaml`: Creates the DynamoDB tables for products, orders, and users.
- `authentication-stack.yaml`: Configures Cognito user pools and API Gateway endpoints for user authentication.
- `orders-service-stack.yaml`: Defines the Lambda functions, API Gateway endpoints, and event rules related to order processing.
The main SAM template, `application.yaml`, would then reference these nested stacks using the `AWS::CloudFormation::Stack` resource type. The main template orchestrates the deployment of all nested stacks, forming the complete serverless application.
Resources:
VPCStack:
Type: AWS::CloudFormation::Stack
Properties:
TemplateURL: vpc-stack.yaml
Deploying and Testing Serverless Applications with SAM
Deploying and testing serverless applications are critical steps in the development lifecycle. These processes ensure that the application functions as expected and can be reliably deployed to production environments. The AWS Serverless Application Model (SAM) CLI provides tools to streamline these processes, offering features for deploying applications to AWS and testing them locally.
Deploying Serverless Applications with the AWS CLI and SAM
The deployment process involves packaging the application code and resources, then deploying them to the AWS cloud. The SAM CLI simplifies this by handling the underlying infrastructure provisioning through AWS CloudFormation.To deploy a serverless application, the following steps are typically followed:
- Packaging the Application: The first step involves packaging the application’s code and any dependent resources. The `sam package` command is used for this purpose. This command prepares the application for deployment by creating a deployment package that includes the application code, dependencies, and any necessary configuration files. This package is then uploaded to an Amazon S3 bucket.
- Deploying the Application: Once the application is packaged, the `sam deploy` command is used to deploy it to AWS. This command takes the packaged application and deploys it to the specified AWS account and region. It creates or updates the necessary AWS resources, such as Lambda functions, API Gateway endpoints, and DynamoDB tables, based on the configuration defined in the SAM template.
- Specifying Deployment Parameters: The `sam deploy` command supports various options for customizing the deployment process. These options allow developers to specify the AWS region, the S3 bucket where the packaged application is stored, the CloudFormation stack name, and any parameters required by the SAM template. For example, the `–stack-name` option allows developers to specify the name of the CloudFormation stack that will be created or updated during deployment.
The `–region` option specifies the AWS region where the application will be deployed.
- Deployment Options: The `sam deploy` command offers several deployment options to manage different scenarios.
- `–guided`: This interactive mode guides the user through the deployment process, prompting for input on required parameters. This is especially helpful for first-time deployments or when making significant changes.
- `–capabilities`: This option allows developers to specify the capabilities required by the CloudFormation stack. For example, the `CAPABILITY_IAM` capability is required when the SAM template creates IAM resources.
- `–confirm-changeset`: This option prompts the user to confirm the changes before deploying the application, providing an opportunity to review the changes that will be made to the AWS resources.
- `–no-fail-on-empty-changeset`: This option allows the deployment to succeed even if no changes are detected in the application.
Here’s an example of deploying a serverless application using the SAM CLI:“`bashsam package –output-template-file packaged.yaml –s3-bucket my-s3-bucketsam deploy –template-file packaged.yaml –stack-name my-serverless-app –capabilities CAPABILITY_IAM“`In this example:* `sam package` packages the application and uploads the code to an S3 bucket.
- `sam deploy` deploys the packaged application to AWS, creating or updating the CloudFormation stack.
- `–output-template-file` specifies the name of the output template file.
- `–s3-bucket` specifies the S3 bucket to upload the code to.
- `–template-file` specifies the path to the packaged template file.
- `–stack-name` specifies the name of the CloudFormation stack.
- `–capabilities` specifies the required capabilities, such as `CAPABILITY_IAM`.
Testing Lambda Functions and API Gateway Endpoints
Testing serverless applications involves verifying the functionality of Lambda functions and API Gateway endpoints. Various testing strategies can be employed to ensure the application behaves as expected.
- Unit Testing: Unit tests focus on individual components or functions. For Lambda functions, unit tests typically involve testing the function’s code logic by providing various input values and verifying the output. Tools like Jest, Mocha, or pytest can be used for unit testing.
- Integration Testing: Integration tests verify the interaction between different components of the application. For example, an integration test might verify that an API Gateway endpoint correctly invokes a Lambda function and that the Lambda function interacts with a DynamoDB table as expected.
- End-to-End Testing: End-to-end tests simulate the entire user flow of the application. These tests typically involve sending requests to the API Gateway endpoints and verifying the responses, including data retrieval and processing. Tools like Postman or Cypress can be used for end-to-end testing.
- Testing Lambda Functions:
- Local Invocation: The SAM CLI allows local invocation of Lambda functions using the `sam local invoke` command. This command simulates the Lambda execution environment, allowing developers to test the function locally without deploying it to AWS.
- Event Simulation: Developers can simulate different event sources by providing sample event payloads to the `sam local invoke` command. This allows testing how the function responds to different types of events, such as API Gateway requests, S3 object creations, or DynamoDB updates.
- Debugging: The SAM CLI supports debugging Lambda functions locally using debuggers like VS Code. This allows developers to step through the code, inspect variables, and identify and fix issues.
- Testing API Gateway Endpoints:
- Local Invocation: The SAM CLI allows local testing of API Gateway endpoints using the `sam local start-api` command. This command starts a local API Gateway emulator, allowing developers to send requests to the API endpoints and verify their behavior.
- Request Simulation: Developers can simulate different HTTP methods (GET, POST, PUT, DELETE) and request parameters to test various API scenarios.
- Response Verification: The responses from the API Gateway endpoints can be verified to ensure they return the expected data and status codes.
Here’s an example of testing a Lambda function locally using the SAM CLI:“`bashsam local invoke MyFunction –event event.json“`In this example:* `sam local invoke` invokes the Lambda function locally.
- `MyFunction` is the name of the Lambda function defined in the SAM template.
- `–event event.json` specifies the path to an event JSON file that simulates the input event.
Using the SAM CLI for Local Testing and Debugging
The SAM CLI provides several features for local testing and debugging, allowing developers to test and debug their serverless applications without deploying them to AWS.
- `sam local invoke`: This command allows developers to invoke Lambda functions locally, providing input events and viewing the output. This command is useful for testing the function’s logic and verifying its behavior with different event payloads.
- `sam local start-api`: This command starts a local API Gateway emulator, allowing developers to test API endpoints locally. Developers can send requests to the API endpoints and verify the responses. This command is helpful for testing the API’s functionality and ensuring that it correctly routes requests to the Lambda functions.
- `sam logs`: This command retrieves logs from Lambda functions, providing insights into the function’s execution. This command is useful for debugging issues and identifying errors.
- Debugging with IDEs: The SAM CLI integrates with popular IDEs like VS Code, allowing developers to debug Lambda functions locally. Developers can set breakpoints, step through the code, and inspect variables to identify and fix issues.
- Example Debugging Scenario: Consider a Lambda function that processes data from an S3 bucket. The developer can use `sam local invoke` with a sample S3 event to test the function’s logic. If an error occurs, they can use `sam logs` to view the logs and identify the cause of the error. Then, they can set breakpoints in the code using their IDE and debug the function locally to understand the issue and fix it.
The SAM CLI’s local testing and debugging capabilities significantly improve the developer experience by providing a fast and efficient way to test and debug serverless applications before deploying them to AWS. This reduces the feedback loop and accelerates the development process.
Ending Remarks
In summary, defining serverless resources within a SAM template is a powerful and efficient method for managing serverless applications on AWS. By understanding the syntax, configurations, and best practices Artikeld, developers can create robust, scalable, and maintainable serverless architectures. From defining Lambda functions and API Gateway endpoints to configuring DynamoDB tables and S3 buckets, SAM provides a comprehensive toolkit for building and deploying modern, event-driven applications.
Embracing these techniques ensures that serverless applications are not only easier to manage but also optimized for performance and cost-efficiency.
Expert Answers
What is the SAM transform, and why is it important?
The SAM transform is a CloudFormation macro that simplifies the definition of serverless resources. It allows developers to use shorthand notations and pre-defined resource types, reducing boilerplate code and making templates more readable and maintainable. This leads to faster development cycles and easier deployment of serverless applications.
How do I handle environment variables in a SAM template?
Environment variables are defined within the properties of a resource, such as a Lambda function. They can be static values or referenced from parameters defined in the template. This allows for flexible configuration of applications across different environments (e.g., development, staging, production).
How can I test my SAM template locally?
The SAM CLI provides a suite of tools for local testing and debugging. The `sam local invoke` command allows you to invoke Lambda functions locally, and `sam local start-api` allows you to simulate API Gateway endpoints. These tools significantly reduce the time and effort required to test and debug serverless applications.
What are nested stacks in SAM, and when should I use them?
Nested stacks are CloudFormation stacks defined within another stack. In SAM, they are used to modularize templates, promoting code reuse and making large applications easier to manage. They are particularly useful for complex applications with multiple components that can be deployed and managed independently.
How do I handle versioning and updates to my serverless application?
Versioning and updates are handled through CloudFormation’s update capabilities. When you deploy a new version of your SAM template, CloudFormation automatically updates the resources, often without downtime. Proper planning, including using aliases for Lambda functions and managing dependencies, is crucial for a smooth update process.