Enhancing Your Security Posture: A Guide to Continuous Improvement
Cybersecurity is a dynamic field, and bolstering your security posture requires a proactive, ongoing approach. This article outlines a strategic frame...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Cybersecurity is a dynamic field, and bolstering your security posture requires a proactive, ongoing approach. This article outlines a strategic frame...

Migrating to the cloud offers substantial benefits, but necessitates careful consideration of data privacy regulations, especially GDPR. This article...

Organizations leveraging multi-cloud environments face a complex landscape of security risks, including data breaches, identity and access management...
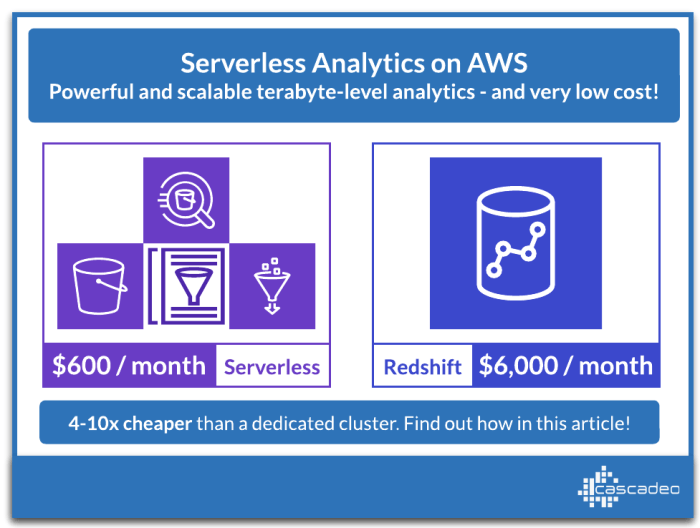
Serverless analytics provides significant advantages in scalability and cost-efficiency, but achieving peak performance requires targeted optimization...
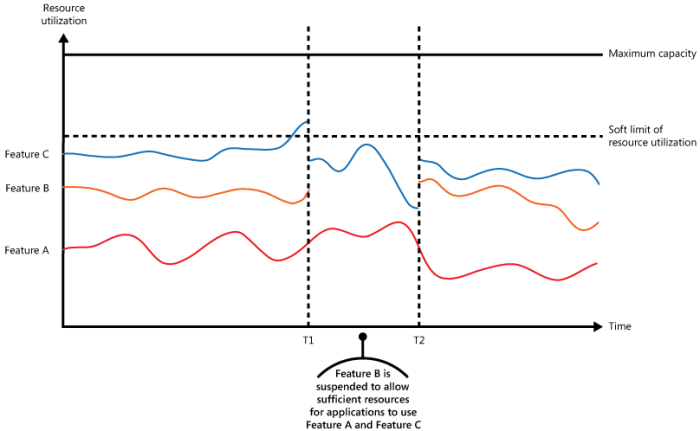
This comprehensive guide delves into the critical concept of throttling, exploring its mechanisms, patterns, and implementation strategies. From defin...

This guide provides a comprehensive overview of how to launch a successful career in the dynamic field of cloud security. It offers practical advice a...

This comprehensive guide delves into the essential practices of effective code reviews, highlighting their crucial role in enhancing software quality...

Achieving system robustness hinges on the efficient execution of startup and shutdown processes, a key aspect of Factor IX. This article explores stra...

This comprehensive article delves into the emerging field of Confidential Computing, defining its core concepts, key technologies, and significant ben...
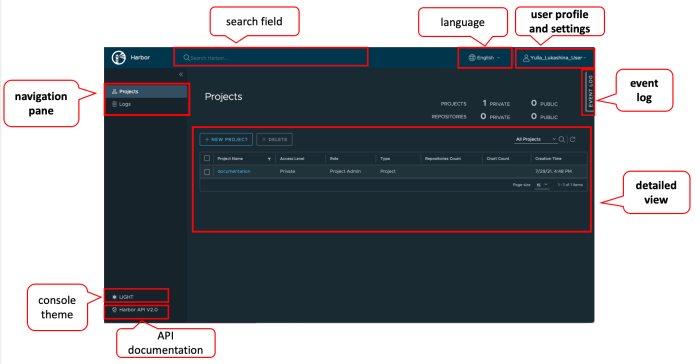
In the dynamic world of software development, container registries play a crucial, yet often overlooked, role. Serving as a secure and organized repos...

This article provides a comprehensive cost-benefit analysis of serverless query processing, examining its core concepts, advantages, and real-world ap...

This comprehensive guide provides a detailed overview of securing the Kubernetes control plane, covering essential aspects from authentication and aut...