
Understanding Security Maturity Models: A Deep Dive into CMMC and Beyond
This article provides a comprehensive overview of security maturity models, essential frameworks for enhancing an organization's cybersecurity posture...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This article provides a comprehensive overview of security maturity models, essential frameworks for enhancing an organization's cybersecurity posture...

Effectively presenting FinOps results to leadership involves more than just data; it's about crafting a narrative that highlights the strategic value...
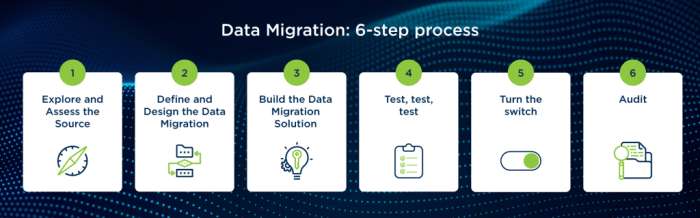
Migrating a CRM system is a complex undertaking, requiring careful planning and execution to ensure a successful transition. This comprehensive guide...

Containerizing legacy applications, with their inherent complexities and technical debt, requires a strategic approach. This process begins with under...

Building an Internal Developer Platform (IDP) can significantly streamline your software development lifecycle and empower your teams. This comprehens...

To significantly improve application performance and user experience, consider implementing a Content Delivery Network (CDN). This guide provides a co...

This article delves into the world of serverless stream processing, exploring its core components, benefits, and real-world applications. Readers wil...
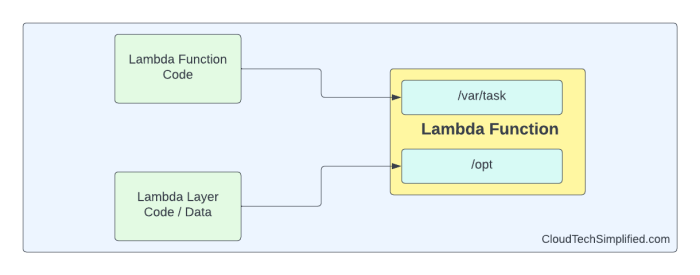
This article delves into Lambda Layers, a powerful feature for optimizing serverless applications by enabling code sharing and reusability across mult...

This article provides a comprehensive overview of designing scalable machine learning architectures, essential for handling large datasets and complex...
This article delves into the often-overlooked cost implications of serverless cold starts, a crucial factor in optimizing application performance and...

In today's digital environment, understanding the financial ramifications of a data breach is essential for any organization. This comprehensive guide...

Privacy-preserving computation offers a groundbreaking approach to data security, enabling the processing of encrypted data without the need for decry...