
Kubernetes Services vs. Ingress: Key Differences and When to Use Each
This comprehensive guide delves into the core concepts of Kubernetes Services and Ingress, essential components for managing application networking wi...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This comprehensive guide delves into the core concepts of Kubernetes Services and Ingress, essential components for managing application networking wi...

Serverless applications, despite their scalability benefits, require robust strategies for managing sensitive data like API keys and database credenti...

Managing cloud costs effectively is crucial for optimizing cloud investments. This guide, "How to Create a FinOps Playbook for Your Organization," pro...

This article explores the critical role of the circuit breaker pattern in building resilient microservices. Learn how circuit breakers safeguard your...
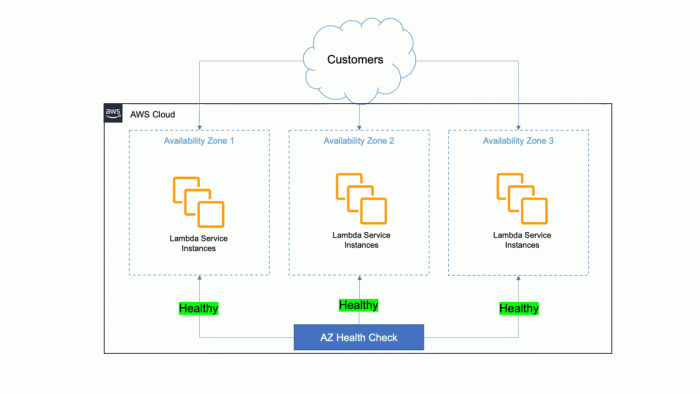
This comprehensive article delves into the distinctions between AWS Lambda and Fargate, two prominent serverless computing options. Through detailed a...
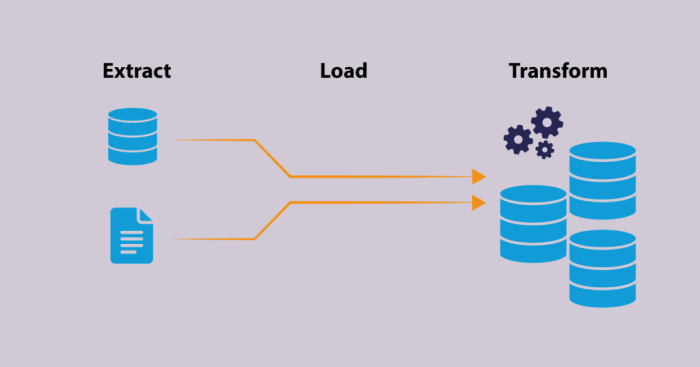
This article explores the transformative shift towards serverless ETL (Extract, Transform, Load) processes, detailing their core concepts, architectur...
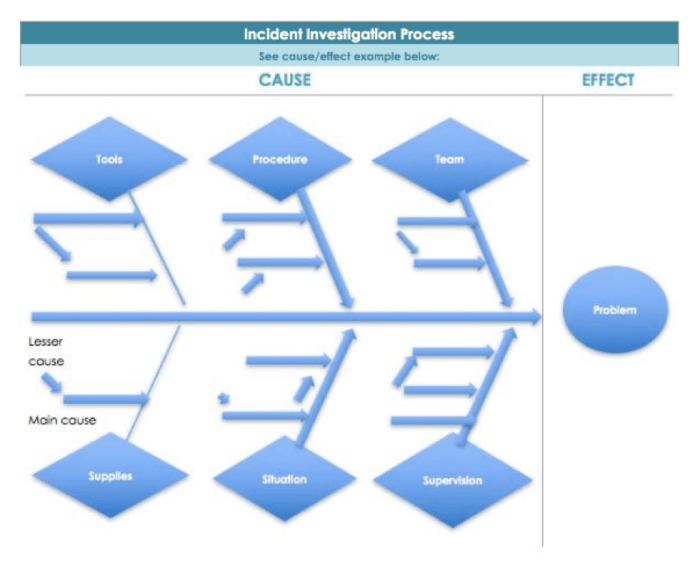
This article provides a comprehensive guide to performing a Root Cause Analysis (RCA) following a security incident, a crucial skill in today's digita...
Integrating FinOps with your financial systems is essential for maximizing cloud spending efficiency and strategic decision-making. This alignment all...

Navigating the complexities of distributed systems requires a critical understanding of the trade-off between availability and consistency. This artic...
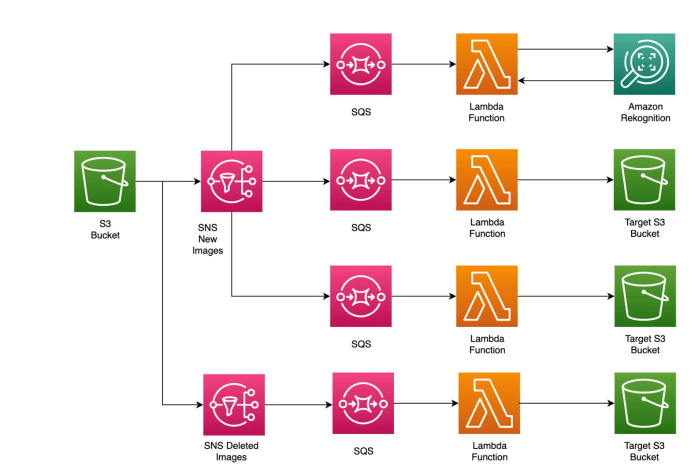
This article provides a comprehensive guide to implementing the fan-out pattern using serverless technologies, exploring its advantages and practical...
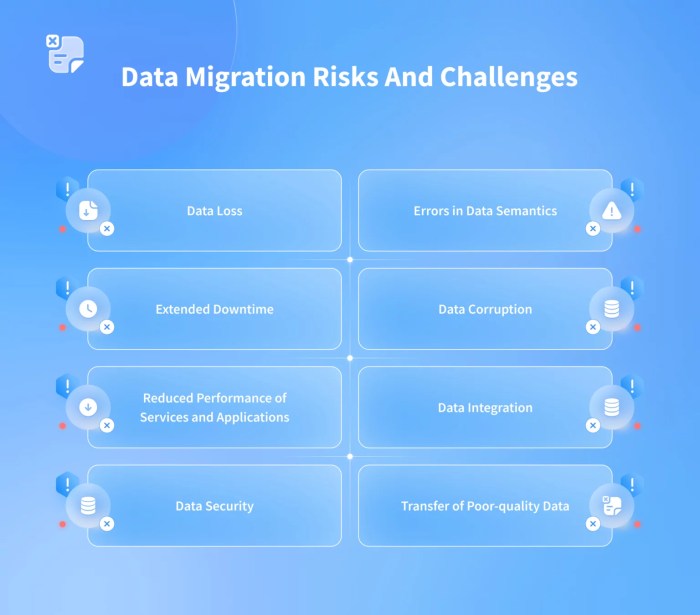
Data migration, the process of moving data across different systems, introduces significant security challenges that must be addressed. This article e...

This comprehensive guide explores Interactive Application Security Testing (IAST), detailing its fundamental principles, advantages, and practical imp...