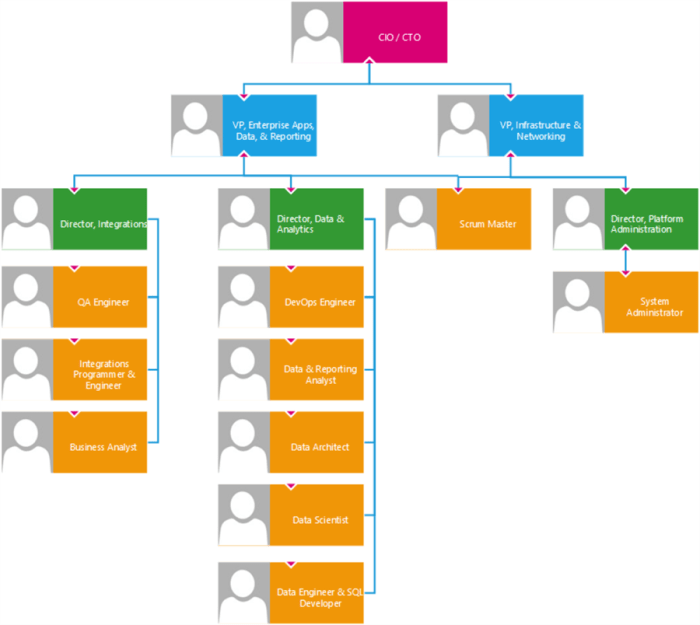
Cloud Access Roles & Responsibilities: A Guide to Clarity and Security
Cloud computing's scalability demands stringent security measures, making clear role and responsibility definitions for cloud access paramount. This a...
152 posts in this category

Cloud computing's scalability demands stringent security measures, making clear role and responsibility definitions for cloud access paramount. This a...
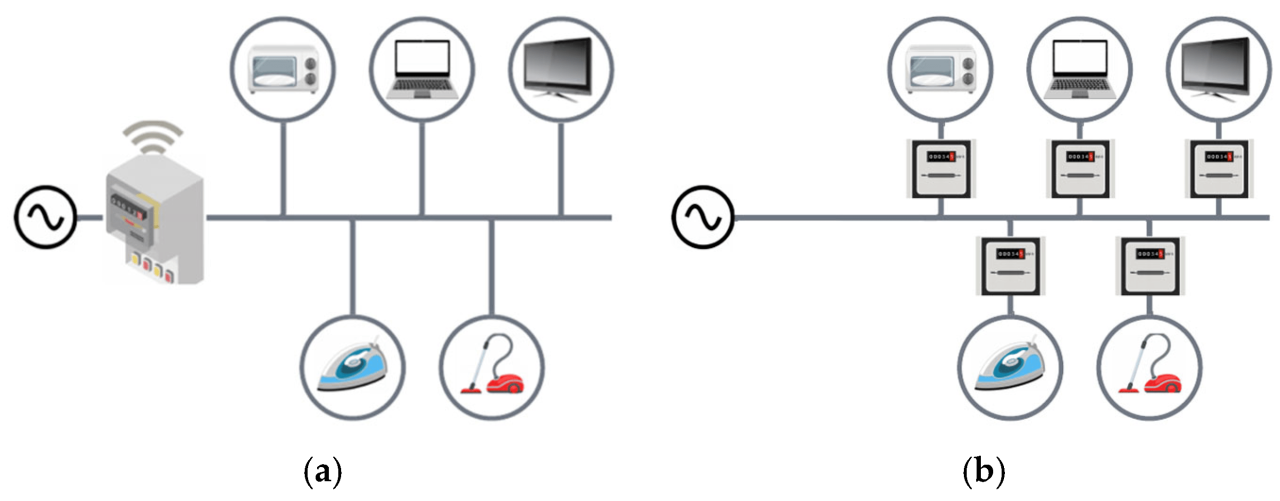
Facing an increasingly complex cyber threat landscape, security operations teams need efficient solutions. This article explores how Security Orchestr...

Digital Rights Management (DRM) is a critical component of the digital landscape, serving to protect intellectual property in the realm of content cre...

This article provides a comprehensive analysis of proactive versus reactive security strategies, detailing their core principles, advantages, and limi...
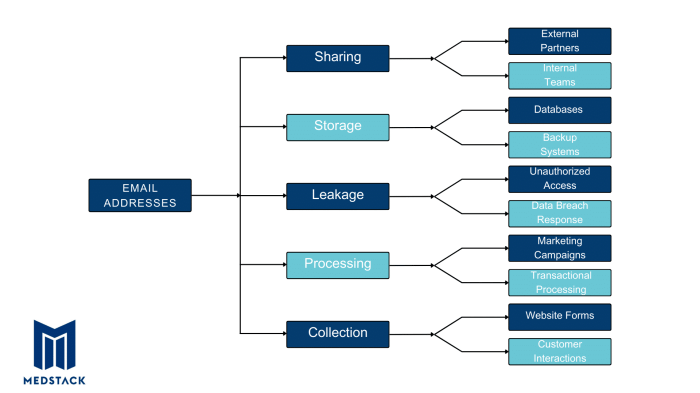
This article explores the critical technical controls necessary for organizations to comply with GDPR regulations concerning data residency and sovere...
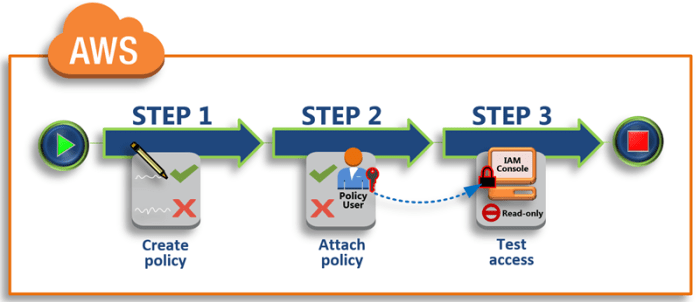
This comprehensive guide delves into the world of Identity and Access Management (IAM) policies, explaining their crucial role in securing access to y...

In the modern cloud-centric business environment, robust data and infrastructure security is critical. Security Information and Event Management (SIEM...
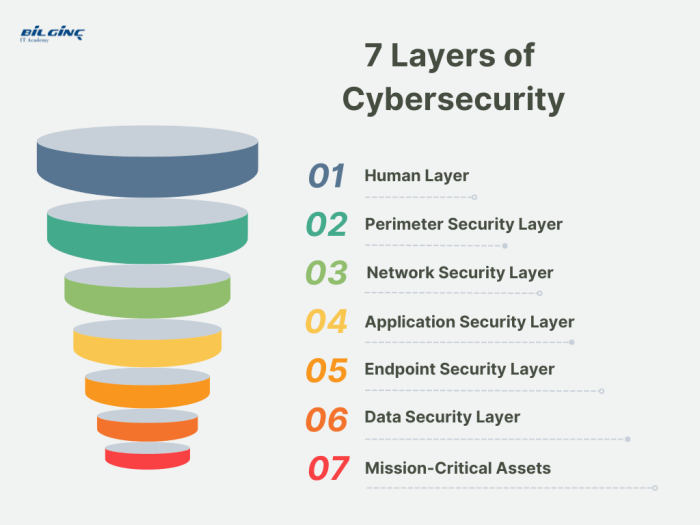
Defense in depth is a critical cybersecurity principle that emphasizes a layered approach to security, acknowledging that no single measure is impenet...
This comprehensive guide outlines the crucial steps for conducting regular cloud security risk assessments, ensuring the protection of your valuable a...
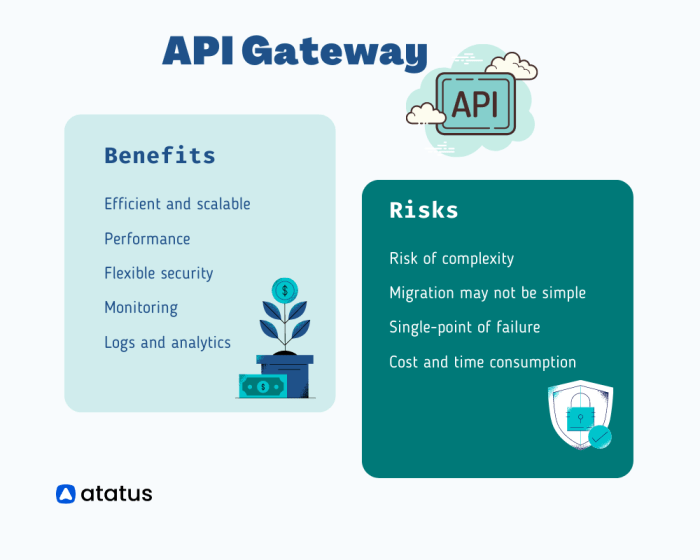
API gateways are vital components of modern application architectures, acting as the primary point of entry and security for all API traffic. Understa...
Want to strengthen your organization's digital defenses? This guide offers a comprehensive approach to conducting a security architecture review, prov...
Cybersecurity is a dynamic field, and bolstering your security posture requires a proactive, ongoing approach. This article outlines a strategic frame...