Implementing Single Sign-On (SSO) for Enterprise Applications: A Practical Guide
This comprehensive guide provides a detailed roadmap for implementing Single Sign-On (SSO) across your enterprise applications. From understanding the...
152 posts in this category
This comprehensive guide provides a detailed roadmap for implementing Single Sign-On (SSO) across your enterprise applications. From understanding the...

This comprehensive article explores the evolving landscape of cloud security, addressing current threats and vulnerabilities while examining the impac...
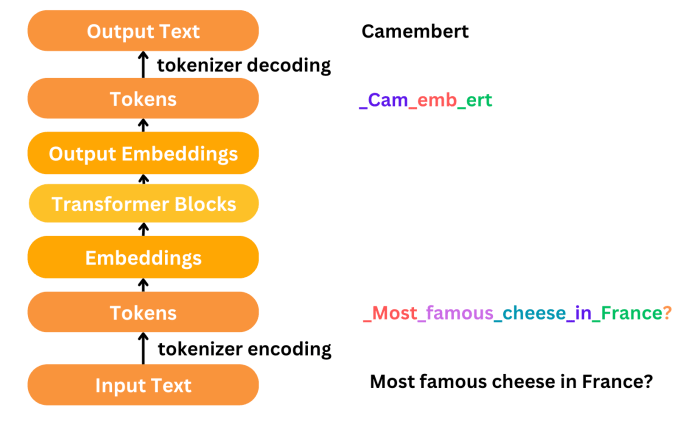
This comprehensive article delves into the critical role of tokenization in modern data security, exploring its core concepts, operational mechanisms,...
Securing remote access to cloud environments is paramount in today's interconnected landscape, yet presents significant security challenges. This guid...

This comprehensive guide delves into the MITRE ATT&CK framework, providing a roadmap for understanding its structure and leveraging its capabilities t...
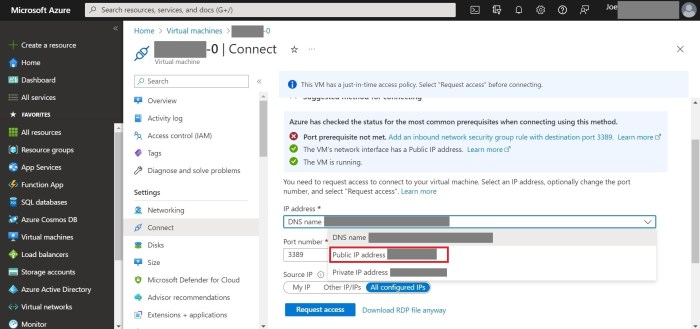
This article delves into the critical concept of Just-in-Time (JIT) access for cloud resources, exploring its core principles and the significant secu...
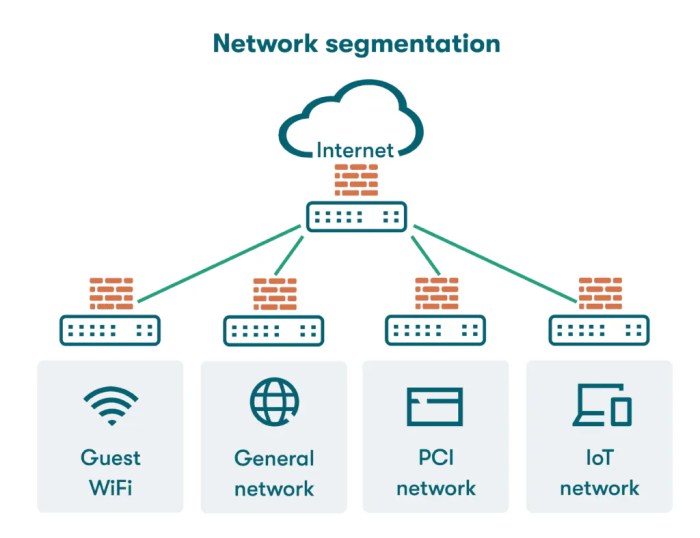
This comprehensive guide provides a deep dive into network segmentation, a crucial strategy for bolstering your organization's security posture. From...
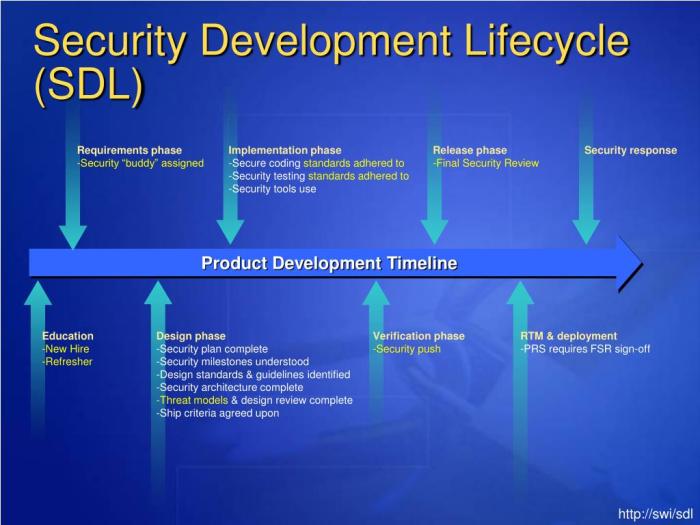
"Shifting security left" is a critical strategy for modern software development, emphasizing the integration of security practices early in the develo...

Securing your critical digital assets starts with effective Privileged Access Management (PAM). This article provides a comprehensive, practical guide...
This article provides a comprehensive overview of Secure Boot processes within virtual machines, detailing its critical role in securing a VM's boot p...
In today's dynamic digital environment, automating security policy enforcement is paramount. This guide provides a comprehensive overview, covering es...

In today's digital environment, understanding the financial ramifications of a data breach is essential for any organization. This comprehensive guide...