
Security Considerations for Big Data Platforms: A Comprehensive Guide
Protecting sensitive data within big data platforms demands a comprehensive approach encompassing encryption, access control, data governance, and rob...
152 posts in this category

Protecting sensitive data within big data platforms demands a comprehensive approach encompassing encryption, access control, data governance, and rob...
In an increasingly cloud-dependent business environment, establishing a strong cloud security team is crucial for protecting valuable data and applica...

Discover insights and practical tips in this comprehensive guide about What Are The Compliance Requirements For Data Breach Notifications.

In today's complex regulatory environment, establishing a robust data retention policy is crucial for compliance and minimizing potential risks. This...
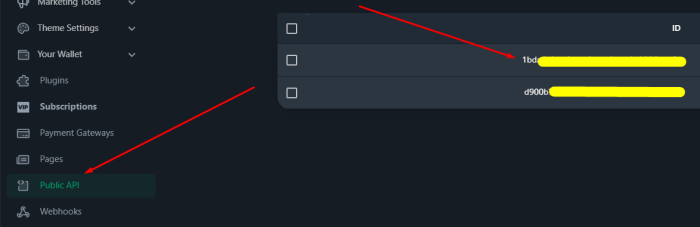
Protecting sensitive API keys and tokens is crucial for maintaining application security and preventing costly data breaches. This article provides a...

Effectively communicating cybersecurity risks to the board of directors is crucial for informed decision-making. This guide offers a comprehensive app...

Safeguarding a data lake environment requires a multi-faceted approach. This article provides a comprehensive guide to securing your data lake, coveri...
This article provides a comprehensive guide to implementing a Zero Trust security model within cloud environments, covering key principles, asset iden...

This comprehensive article delves into the emerging field of Confidential Computing, defining its core concepts, key technologies, and significant ben...

This article provides a comprehensive overview of Software Bill of Materials (SBOMs), explaining their definition, purpose, and benefits for various s...
Protecting sensitive information is paramount in today's data-driven world, and this comprehensive guide provides a deep dive into implementing effect...
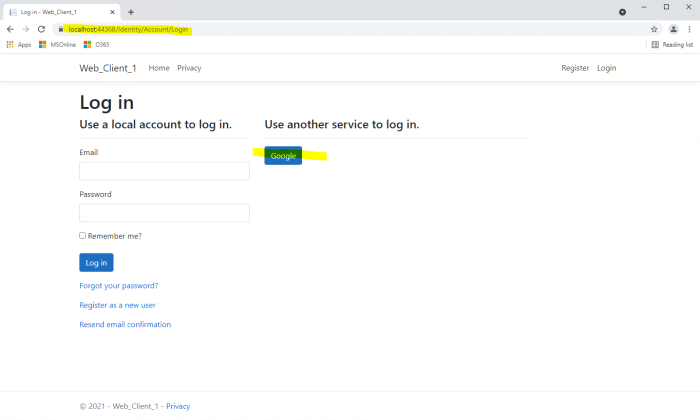
This comprehensive guide delves into the intricacies of OAuth 2.0 and OpenID Connect, explaining their roles in modern authentication and authorizatio...