Enforcing Strong Authentication & Multi-Factor Authentication: A Comprehensive Guide
Protecting sensitive data in the digital age demands robust security measures. This guide provides a detailed overview of enforcing strong authenticat...
152 posts in this category

Protecting sensitive data in the digital age demands robust security measures. This guide provides a detailed overview of enforcing strong authenticat...
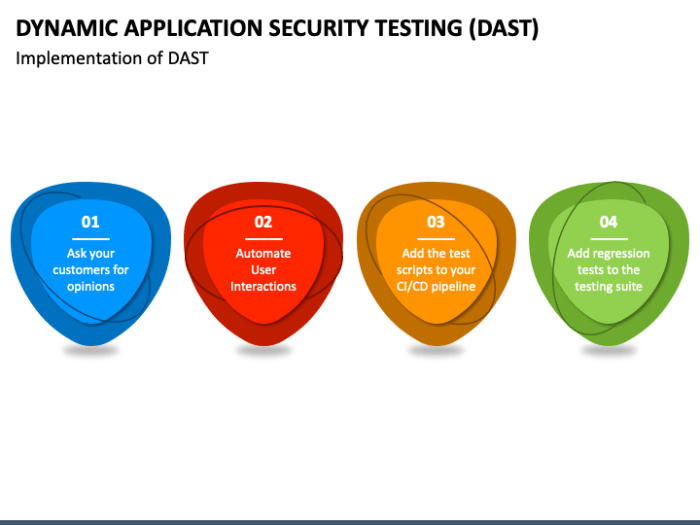
This comprehensive guide explores Dynamic Application Security Testing (DAST), providing a deep dive into its core concepts, functionality, and practi...
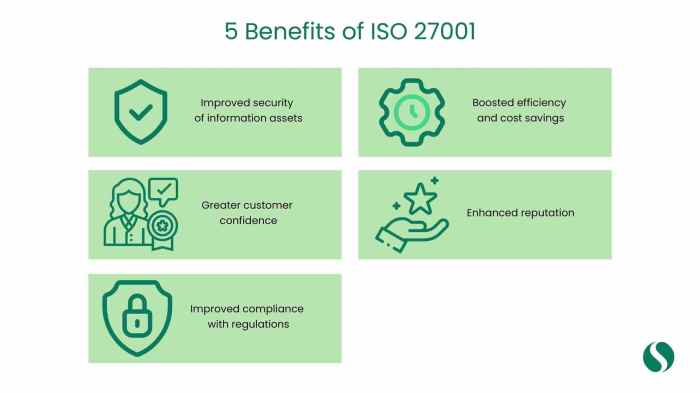
This comprehensive guide provides a detailed roadmap for achieving ISO 27001 certification, covering everything from understanding the core principles...

Organizations leveraging multi-cloud environments face a complex landscape of security risks, including data breaches, identity and access management...

This guide provides a comprehensive overview of how to launch a successful career in the dynamic field of cloud security. It offers practical advice a...
This article explores the vital integration of threat intelligence into cloud security operations, a crucial step in defending against modern cyber th...

Prepare for the future of cybersecurity with a comprehensive guide to Post-Quantum Cryptography (PQC). This article delves into the fundamental concep...

The cloud offers significant advantages, but it also presents new vulnerabilities to malware and ransomware attacks. This article outlines essential s...
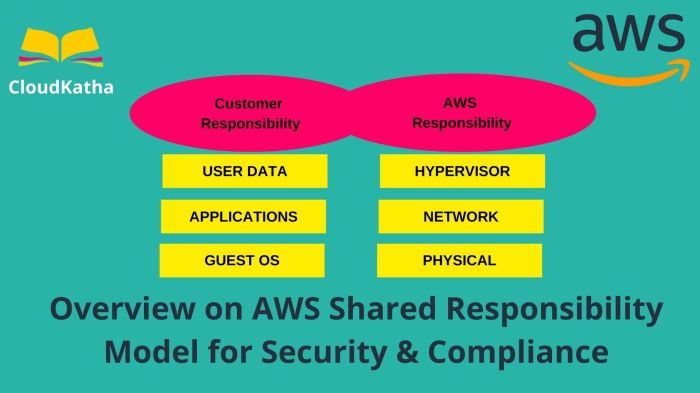
The shared responsibility model is a critical framework in cloud security, outlining the security obligations of both the cloud provider and the custo...
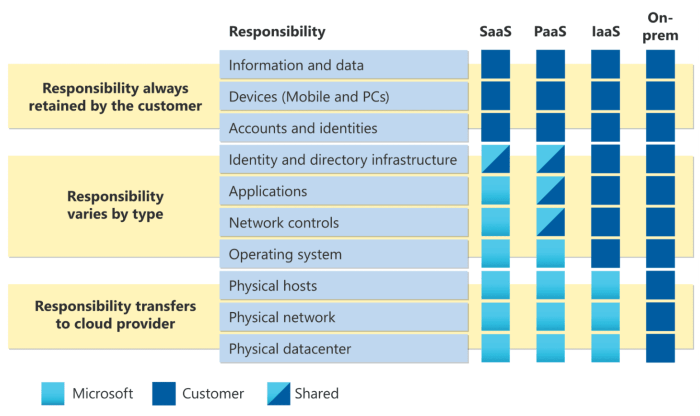
This article explores the critical need to protect "data in use," delving into the inherent security risks and challenges associated with active compu...
Navigating a cloud security audit can seem daunting, but this comprehensive guide provides a clear roadmap for preparation and success. The article me...
Managing security across a multi-cloud environment requires a strategic approach to avoid fragmentation and ensure consistent protection. This guide o...