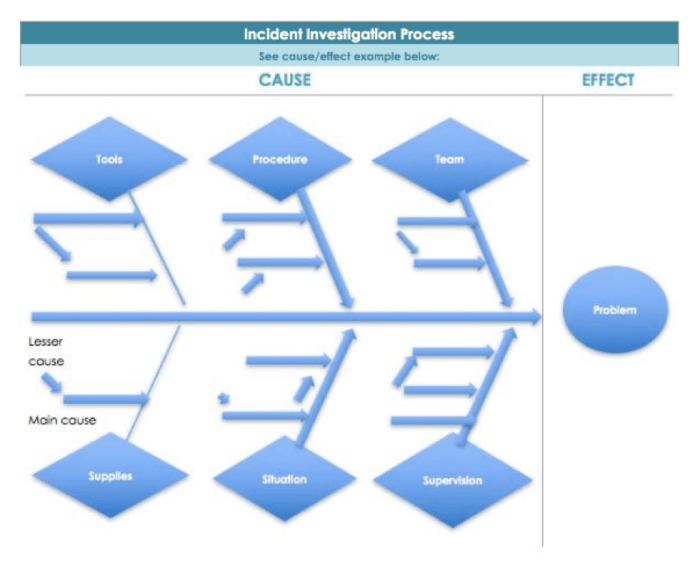
Root Cause Analysis for Security Incidents: A Step-by-Step Guide
This article provides a comprehensive guide to performing a Root Cause Analysis (RCA) following a security incident, a crucial skill in today's digita...
152 posts in this category

This article provides a comprehensive guide to performing a Root Cause Analysis (RCA) following a security incident, a crucial skill in today's digita...

This article provides a comprehensive overview of Static Application Security Testing (SAST), exploring its core principles, role within the Software...

This article delves into the critical practice of Continuous Compliance Monitoring (CCM) in cloud environments, explaining its core concepts and showc...

This article provides a comprehensive overview of security maturity models, essential frameworks for enhancing an organization's cybersecurity posture...

Cloud governance is essential for successful cloud adoption, and "policy as code" is revolutionizing how organizations manage and secure their environ...

This comprehensive guide explores Interactive Application Security Testing (IAST), detailing its fundamental principles, advantages, and practical imp...

This guide provides a comprehensive roadmap for establishing robust threat hunting capabilities, essential for proactively identifying and mitigating...

This article provides a comprehensive guide to managing secrets and encryption keys in the cloud, a critical aspect of cloud security. It explores fun...
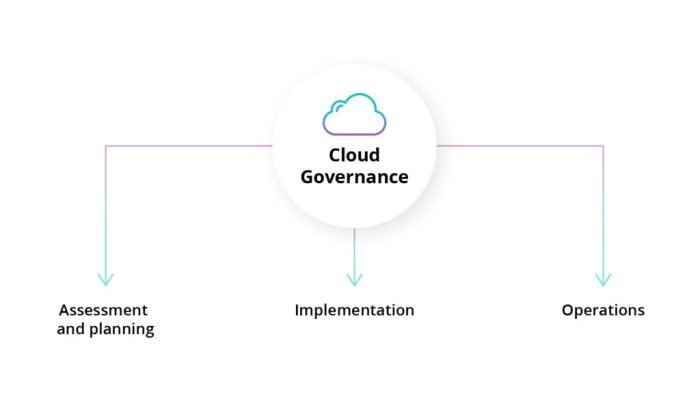
Establishing a formal cloud security governance framework is crucial for protecting valuable assets and maintaining compliance in the cloud. This fram...

Kubernetes Pod Security Policies (PSPs) are crucial for bolstering the security of your containerized applications within a Kubernetes cluster. These...

This article provides a comprehensive overview of the roles and responsibilities within a Security Operations Center (SOC), crucial for modern cyberse...

In today's evolving digital landscape, cloud security certifications are crucial for professionals seeking to validate their expertise and advance the...