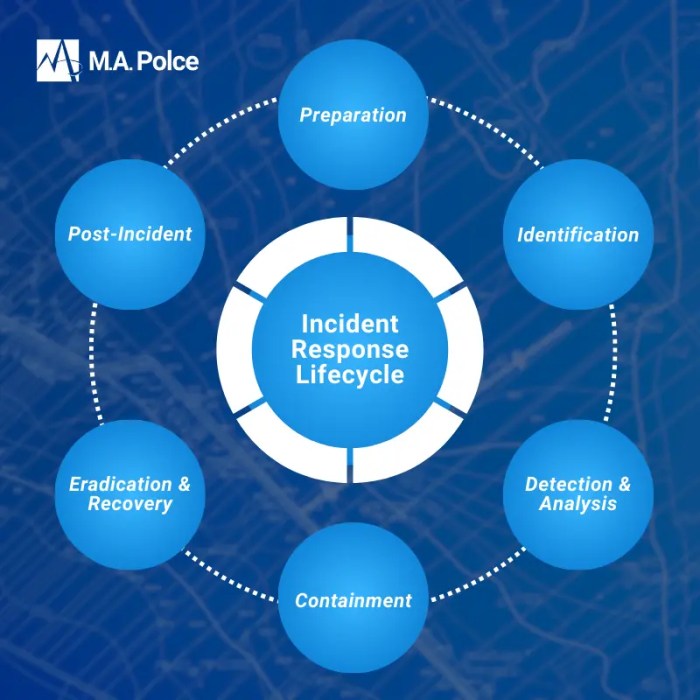
Tabletop Exercises for Incident Response: Definition, Benefits, and Best Practices
In the face of ever-evolving cyber threats, tabletop exercises are vital for strengthening an organization's incident response capabilities. These dyn...
152 posts in this category

In the face of ever-evolving cyber threats, tabletop exercises are vital for strengthening an organization's incident response capabilities. These dyn...

This article provides a comprehensive overview of Data Privacy Impact Assessments (DPIAs), essential tools for protecting personal information in the...
In the world of interconnected microservices, secure service-to-service communication is critical. Mutual Transport Layer Security (mTLS) provides a p...

This comprehensive article delves into Runtime Application Self-Protection (RASP), exploring its fundamental concepts, architecture, and operational m...

In the digital age, the integrity and admissibility of digital evidence are paramount for successful investigations. This article delves into the cruc...

This article delves into the critical process of de-provisioning user accounts, explaining its definition, triggers, and the vital role it plays in bo...
This article provides a comprehensive guide to implementing CIS Benchmarks for cloud hardening, covering crucial aspects from understanding the benchm...
The increasing convergence of Internet of Things (IoT) devices and cloud services necessitates a thorough examination of the associated security risks...

Cloud-based businesses are increasingly vulnerable to Distributed Denial of Service (DDoS) attacks, which can disrupt online services and lead to subs...

In today's data-driven world, protecting sensitive information is critical, and Key Management Services (KMS) are essential for achieving this. This a...

Effectively securing your cloud infrastructure requires a deep understanding of both Security Groups and Network ACLs. This comprehensive guide delves...
In an era defined by digital interconnectedness, cyber insurance has become a critical safeguard for businesses facing persistent online threats. This...