
Tactics, Techniques, and Procedures (TTPs): A Comprehensive Guide
This article provides a comprehensive guide to Tactics, Techniques, and Procedures (TTPs), crucial elements for understanding and combating cyber thre...
152 posts in this category

This article provides a comprehensive guide to Tactics, Techniques, and Procedures (TTPs), crucial elements for understanding and combating cyber thre...
This article offers a comprehensive guide to negotiating robust security provisions within your cloud service level agreement (SLA). It covers critica...
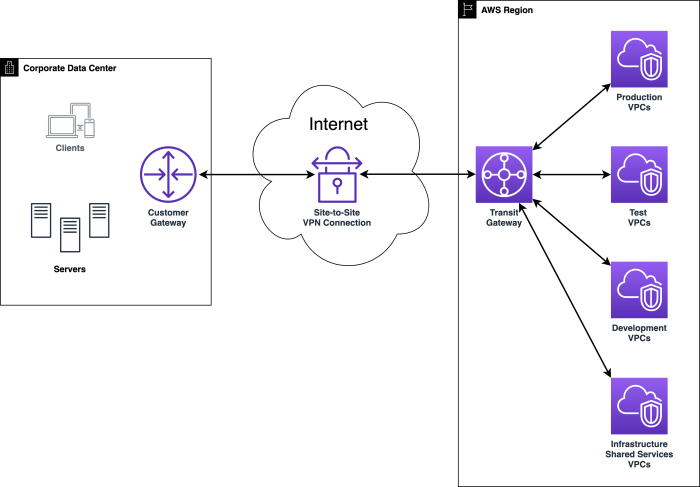
Understand the critical role of Virtual Private Networks (VPNs) in securing modern corporate communications. This article explores the core functional...
This comprehensive guide explores the transformative power of Zero Trust Network Access (ZTNA) in modern cybersecurity, outlining its core principles...
Cybersecurity Key Risk Indicators (KRIs) serve as vital early warning signals, enabling organizations to proactively manage and mitigate evolving cybe...

This article provides an introduction to threat modeling using the STRIDE methodology, a critical practice for enhancing software security. Learn how...
This comprehensive article explores the concept of honeypots in cybersecurity, detailing their purpose, diverse types (low, medium, and high-interacti...

This article provides a comprehensive overview of cloud-native security services, exploring their core concepts, key components, and numerous benefits...

The digital world is constantly evolving, and staying informed about the latest security threats and vulnerabilities is crucial for both individuals a...
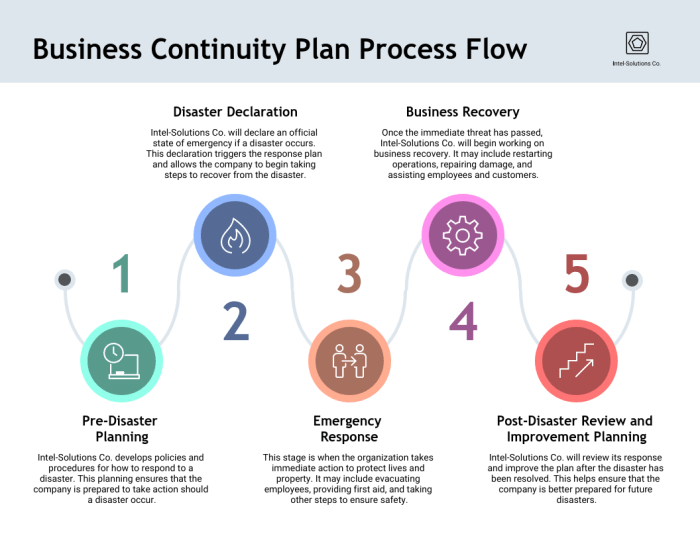
This comprehensive guide explores the essential integration of Business Continuity Planning (BCP) and Disaster Recovery (DR), providing a roadmap to e...

This article provides a comprehensive overview of User and Entity Behavior Analytics (UEBA), exploring its core concepts, components, and practical ap...

This article delves into the intricacies of legal hold and eDiscovery, focusing on the significant advantages of leveraging cloud technology for these...